What is Social Engineering?
Hacking people
The current technique to harm organizations
Know the criminal procedure that puts the security of your organization's information at risk and the four steps that must be followed to mitigate the risks.
With the evolution of technology and technical security measures, if something has become clear is that the most important link in the famous chain of information security of organizations is the person. The security of information is not guaranteed only with the definition of incident management procedures or the implementation of encryption mechanisms, to give some examples.

Source
What is the benefit of stealing the identity of a person? Both directly (exploitation of contacts for scams and frauds) and indirectly (hunting new victims based on a seemingly legitimate profile).
Speaking of social engineering is talking, most of the time, about phishing: a phishing that has evolved over time, and that is becoming more and more subtle, relying on strategies of obfuscation of URLs and automatic copying (or purchase of templates) that emulate official pages. And with special attention to ransomware and the different types of phishing that we can find today.
How is Social Engineering used in attacks against companies?
Psychological motivators: the most common and effective psychological motivators in cyber attacks are urgency and / or fear (46%); the authority (43%); and, the habit, curiosity and false confidence (11%).
Objective of the Attack:
Fraud: consists of stealing money without using force.
Infection: victims are tricked into downloading malicious software.
Theft of credentials: the victims are redirected to a fake website, and access codes to different electronic systems are subtracted there.
Content: cybercriminals use various topics of interest: media, political, sports, work, etc. In addition, when they want something specific to a company, they get to know the tastes and interests of a particular person within it.
Vector or Medium: the most common vectors (ie channels or means of deployment) are electronic mail, navigation, social networks, wireless networks, storage devices, and - even - personal visits in the work site.
Why Social Engineering should worry us?
Currently, we see that Social Engineering is the tip of the spear for cyber attacks. Unfortunately, it is not given due importance and focuses on Information Security in the technological tools. Antivirus, firewalls, antispam, etc. are acquired, but these products must be complemented with the management for human resources.
What should be done?
To manage your Information Security, human resources are vital: to prevent employees from being victims, you must prepare them to detect possible cyber attacks. The best way is through continuous awareness in a controlled environment.

Source
IN THE CASE OF CRYPTOCURRENCIAS
There is a strong correlation between popularity, price and Bitcoin phishing attacks. We can also see that ransomware infections do not really correlate with the price of Bitcoin, while most phishing campaigns against bitcoin wallets really do, which means that the more expensive Bitcoin becomes, the more attacks Let's see.
Cisco OpenDNS Labs
Fortunately, phishing, more than computer skills, consists of pure social engineering. That is, cheating: it is often supplant the identity of an institution, authority or even website to appear before the victim and request their bank credentials or Bitcoin password. It is quite common by email, but it also falsifies authentic websites in order to deceive its victims. Although antivirus is always necessary, in this case it is worth much more attention, because if you correctly detail each message you can immediately notice the differences with an authentic one.
This time the domain that is being falsified is Blockchain.info, for which they have also been oriented towards Google accounts in order to access AdWords and position their false addresses as high as possible in the results. AdWords is simply the Google ad that many people often click inadvertently. In addition, certain results of key terms such as 'buy bitcoins' written in the search engine could also lead to phishing pages.
In order to warn users, OpenDNS Labs reported that the site dheekshapromoters.com serves as an index that redirects to other phishing pages, and also listed a good number of domains created this Christmas season by [email protected], whose main feature is that everyone always differs, at least in a single letter or character, to the original domain that they falsify: Blockchain.info. In this way there are, for example, blockchainls.info, blockcha (i) nfo.info, blocklchaina.info, blockchanifo.info and, most recently, blockchain.inf0. Therefore, it is always important to pay close attention and write the URL correctly.
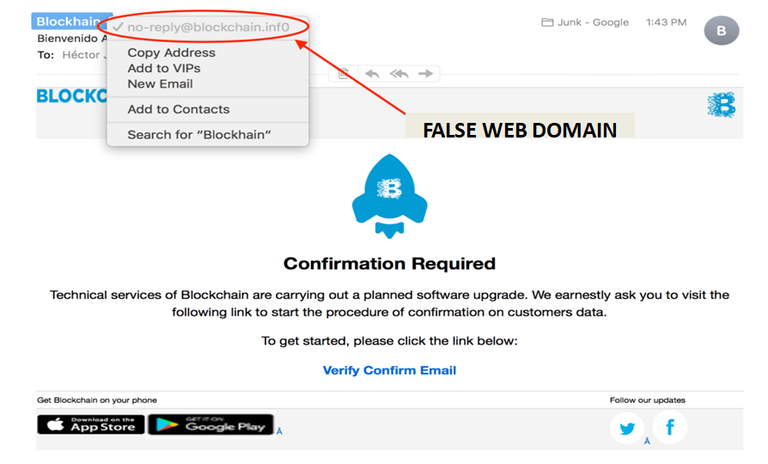
Source
In addition, it has been noted that ransomware and phishing can get to work as a team, because while the user who has been attacked by ransomware is searching the web to acquire bitcoins to pay the ransom, he is likely to press one of the AdWords for phishing and grant your credentials to buy the cryptocurrency, without knowing that these are being stolen.
Faced with this threat, it is only possible to keep the antivirus updated and be alert when the online portfolios are going to be used: as much as it may seem, it may not be the site we believe.

Congratulations @childrensclothes! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
Click here to view your Board
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!