There's a lot of talk about Tor, and well there's different uses for it. Censorship resistance, Bitcoin clients, exchanges like Bitsquare and others. This guide is just for general knowledge, and I'm personally just a person who writes detailed notes.
There was a suggestion in comments about a VPN. I personally support and use AirVPN they take Bitcoin, have invested in Bitcoin and have great service. A VPN is a good solution and you can still use your regular setup. Tor is for very specific privacy, security or other.
It is difficult without javascript and such things to browse the web, but you can start with the most secure settings and then adjust down as needed.
Tor Browser
Download at: torproject.org All Tor network addresses will be followed with .onion, not .com. It is far more secure browsing .onion services.
forbidding javascript and other elements can make web browsing less convenient, but by allowing more elements you open yourself to potential vulnerabilities. It’s best to find the best possible security setting you can withstand while the web browsing experience is still functional.
Configuring Security Settings
Privacy and security settings can be easily configured. Click on the Onion in the top left.
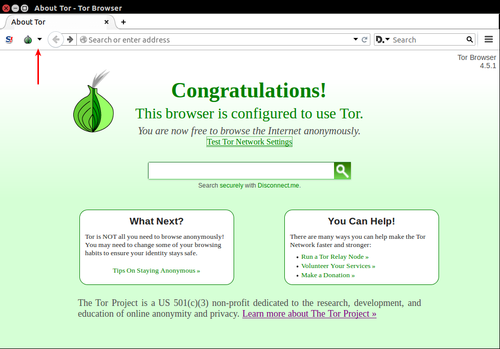
select “Privacy and Security Settings” Adjust the slider to your desired level of security.

Noscript basics
Depending on your security level selected in Tor, Noscript may not provide any advantage. That main advantage of Noscript is it’s easier to tailor allowing on specific sites, or for specific elements on the fly. Click the S in the Top Left next to the Tor Onion symbol and select forbid scripts globally. You should see a red line across the S. If you allow specific sites, you should check that the red line is there for those you do not allow. Allowing only specific sites may create a fingerprint of your activity. There are some advanced settings under options worth taking a look at.
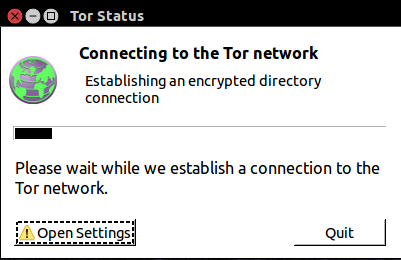
Tor bridge
in some cases if Tor is blocked or you wish to conceal the use of Tor a bridge can be configured. This makes it more difficult for an ISP to detect Tor. Bridges can help avoid censorship, and if your ISP Blocks Tor Traffic it is much more difficult to detect the nature of the traffic unless deep packet inspection is employed. It’s one of those things that since it’s there, might as well set it up as a per-cautionary measure and see if your connection is still, reliable and fast enough for your standards.
- Click Open Settings on the Pop-up Connection Box
1. Click configure
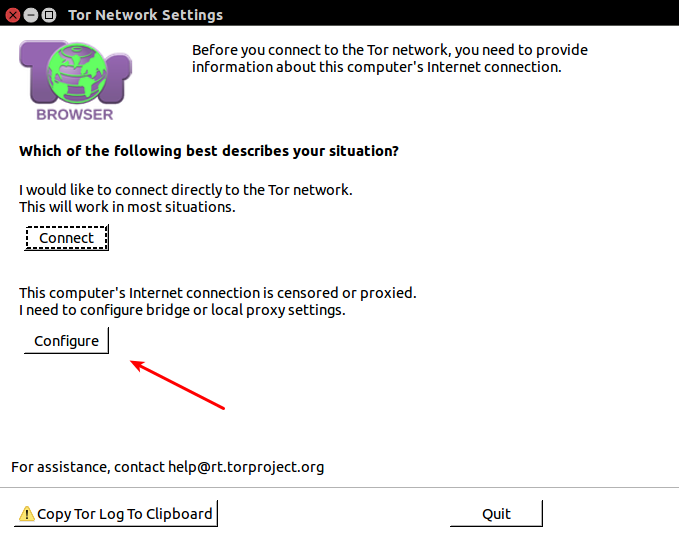
1. Select Yes to ISP Censors or Blocks

1. obfs3 is fine, see below for information on other options.
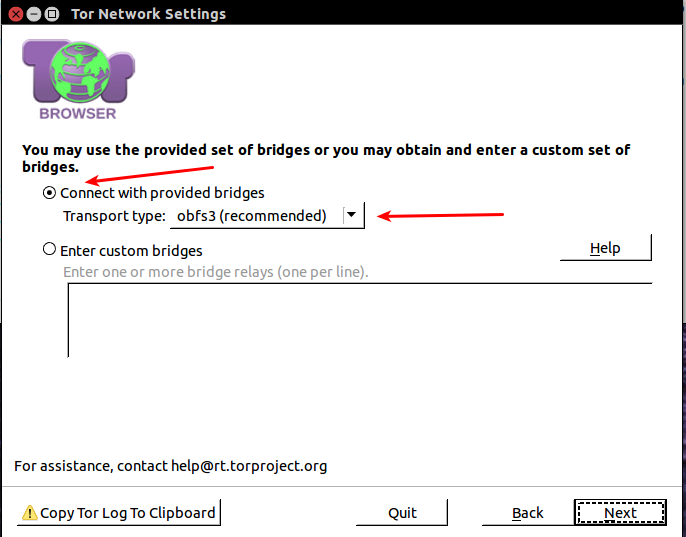
1. Most likely just skip use a local proxy
2. Click connect
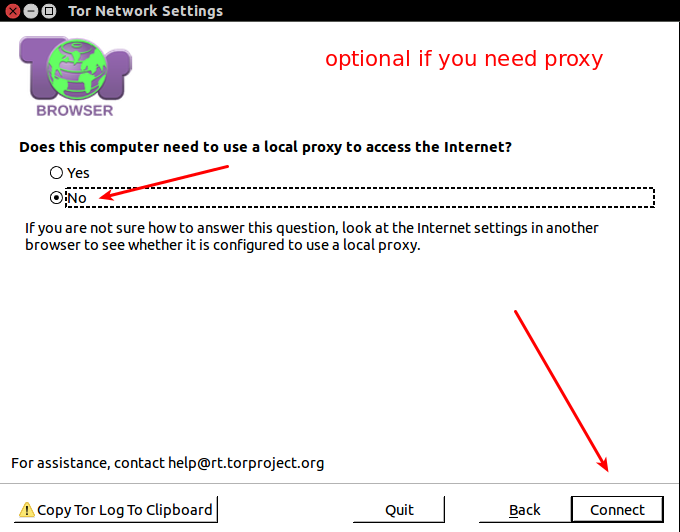
Optionally if Tor is already started you can
- click the onion icon in the top left of the browser and select
- Open Network Settings
- check My ISP Blocks Connections and hit OK.
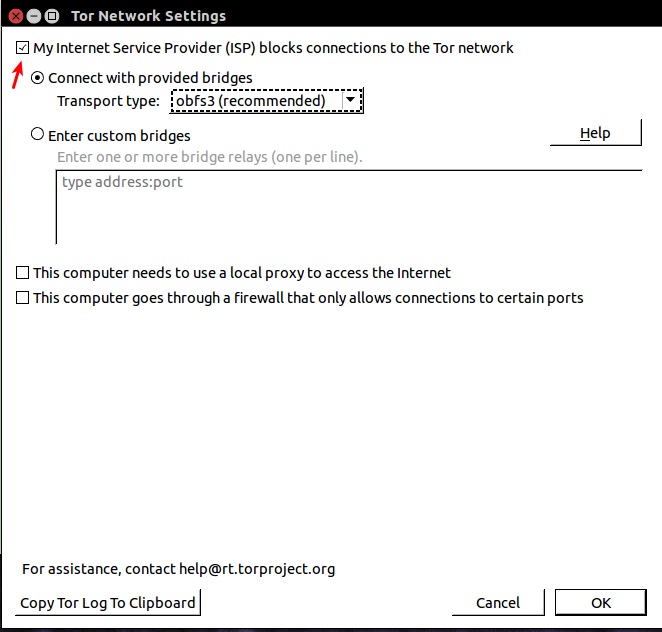
- use obfs 3 which is recommended, see next section on other types.
Pluggable Transports
Pluggable Transports are extensions to Tor which utilize it’s pluggable transport API. These are more advanced ways to disguise traffic flow, for instance making it appear as skype traffic or utilizing a flash proxy. Many are now included in the Bridge Option Menu, so this is a good resource to learn more about the specifics. Some may require custom installation. www.torproject.org/docs/pluggable-trans...
Firefox
If you need to use another browser Firefox is preferred. Here are some configuration settings and extensions that can be helpful.
Optional Configuration:
In the URL Bar enter: about:config

- geo.enabled = false
- geo.wifi.uri =leave blank
- network.http.accept.default = text/html,application/xhtml+xml,application/xml;q=0.9,/;q=0.8
- network.http.use-cache = false
- network.http.keep-alive.timeout = 600
- network.http.max-persistent-connections-per-proxy = 16
- network.proxy.socks_remote_dns = true
- network.cookie.lifetimePolicy = 2
- network.http.sendRefererHeader = 0
- network.http.sendSecureXSiteReferrer = false
- network.protocol-handler.external = false #set the default and all the sub-settings to false
- network.protocol-handler.warn-external = true #set the default and all the sub-settings to true
- network.http.pipelining = true
- network.http.pipelining.maxrequests = 8
- network.http.proxy.keep-alive = true
- network.http.proxy.pipelining = true
- network.prefetch-next = false
- browser.cache.disk.enable = false
- browser.cache.offline.enable = false
- browser.sessionstore.privacy_level = 2
- browser.sessionhistory.max_entries = 2
- browser.display.use_document_fonts = 0
- intl.charsetmenu.browser.cache = ISO-8859-9, windows-1252, windows-1251, ISO-8859-1, UTF-8
- dom.storage.enabled = false
- extensions.blocklist.enabled = false
Other useful options:
- Disable all plugins: tools → addons → plugins
- Disable all live bookmarks: bookmarks → bookmarks toolbar → R/click latest headlines → delete
- Disable all updates: tools → options → advanced → update
- Enable ‘do not track’ feature: tools → options → privacy
- Enable private browsing, configure to remember nothing & disable 3rd party cookies: tools → options → privacy
Useful plugins:
it’s best to keep plugins at a minimum but here are some to consider
- HTTPS Everywhere – www.eff.org/https-everywhere
- Privacy Badger – www.eff.org/privacybadger
- Close n forget – addons.mozilla.org/en-us/firefox/addon/...
- ublock – github.com/chrisaljoudi/uBlock#getting-...
- Modify Headers – addons.mozilla.org/en-us/firefox/addon/...
- NoScript – addons.mozilla.org/en-us/firefox/addon/...
- RefControl – addons.mozilla.org/en-us/firefox/addon/...
- User Agent Switcher – addons.mozilla.org/en-us/firefox/addon/...
- Adblock plus – addons.mozilla.org/en-us/firefox/addon/...
You may consider visiting ip-check.info to see what data your browser is sending.
This is content I have created.
Get onto a VPN as well if you're gonna be messing around on Tor. Just make sure it's legit & safe by going over reviews.
I personally use AirVPN, they take Bitcoin, fair price and have invested in Bitcoin things. I'm not a heavy tor user I more took notes to share, and I have quite a few tutorials, so I will share.
it's slow and don't plan to use it with steemit. For privacy it is a good tool, when you need it. I generally only need it if there is a privacy concern.