Sorry to hear about your loss.
Maybe one short remark about seed words:
There are tools designed for this reason:
https://github.com/3rdIteration/btcrecover
The following table shows how long an attacker would need to brute force missing words:
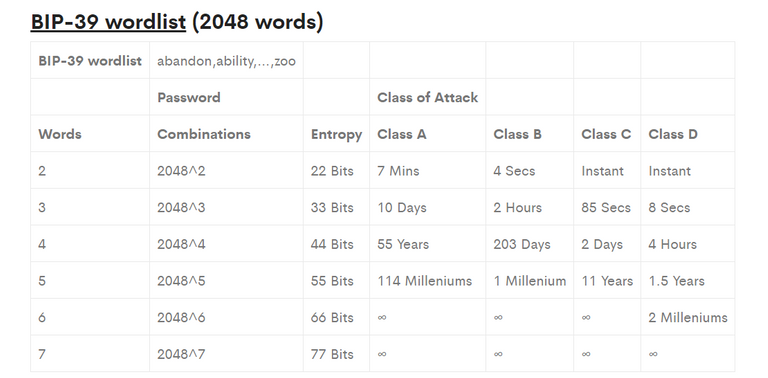
Where A - CPU, B - GPU, C -ASIC (does not exists yet), D - Cluster of Asics (does not exists yet)
Hey Holger, thanks for sharing. I appreciate it. I was not aware about this. Next time I will consider it and create a different system. Lesson learned.