Are you tired of break-ins and theft of your personal data because of poorly composed passwords? REMME offers a solution that makes passwords unnecessary and totally wipes the human factor from any process requiring the verification. The skillful team behind the REMME platform developed the innovative concept of a decentralized protocol named as Public Key Infrastructure (shortly - PKI) along with multiple subsidiary DApps and a distributed ledger.

Website - https://remme.io/
Facebook - https://www.facebook.com/remme.io/
Twitter - https://twitter.com/remme_io
Telegram - https://t.me/remme
Whitepaper - https://drive.google.com/file/d/0B1jTRGmj_3khUV9RTERnYzNvaE0/view
ANN thread at btt - https://bitcointalk.org/index.php?topic=2060387.0
Bounty thread at btt - https://bitcointalk.org/index.php?topic=3611368.0
The concept of REMME’s protocol
To cut the long story short, based on the open-source code REMME’s PKI protocol improves customer experience by upgrading all IT safety components.
The PKI protocol offers 4 main solutions:
- Eliminates the necessity for any centralized method of storage;
- Makes the user credentials’ leak unachievable;
- In 80% cases it changes the weak methods of security by replacing standard password storage (PINs and user made passwords);
- Minimizes or gets rid of the human factor (for instance, social engineering and phishing). In such way, there is a minimum risk of the password’s theft or revealing it by mistake.
6 killer features of REMME
Who may benefit from applying REMME’s services, apps and tools? Everyone who is interested in protecting his valuable information in the most secure way. Think of REMME as a reliable restless guardian of private data in your life – from emails to bank accounts. REMME offers a non-trivial solution by refusing from password protection of any kind.
Its unique PKI protocol gives a chance to use a few really innovative features, especially for business owners, even on the market of creative decentralized apps and services. These killer features are:
1) Blockchain instead of a certificate-based system
No need in any certificate-based center – your business can save money and its data with the smart blockchain technology replacing the authority earlier provided by a certificate-based core.
2) Many blockchains to choose from
The entire system can be handled with various blockchains and even sidechains – you are free to pick up the most convenient security solution for your business.
3) Users love the password-free authentication
Instead of making user filling out forms or complicated passwords, REMME offers a one-click solution that is equally simple and 100% secure.
4) User’s registration happens instantly
Unlike similar decentralized services, REMME offers an instant registration. You don’t have to wait for the rise of the next block in the chain or pay fees to speed up the registration.
5) Support of most well-known messenger services and apps
The protocol widely applies the bots for the most trustworthy messengers. A registered user gets a verification token delivered via the chosen messenger service.
6) Users may have a few accounts for different purposes
A user is free to sign up with an unlimited amount of accounts on REMME platform. In such way, users may get numerous SSL-certificates completely free. When typing login, you can pick up what registered account you want to use.
Other pros of the project:
- The platform is developed by the very experienced team of blockchain developers who previously worked on the development of decentralized services and tools;
- On the official website there is a sophisticated whitepaper translated into few languages;
- Adequate roadmap milestones;
- The project’s token (REM) has a trustworthy conversion rate to ETH (at the moment of writing, 1 REM = 0,00002796 ETH);
- REMME has a potentially big target audience and a few competitors;
- The concept is proved by the PKI protocol;
- REMME has a huge potential for popularity and ongoing growth.
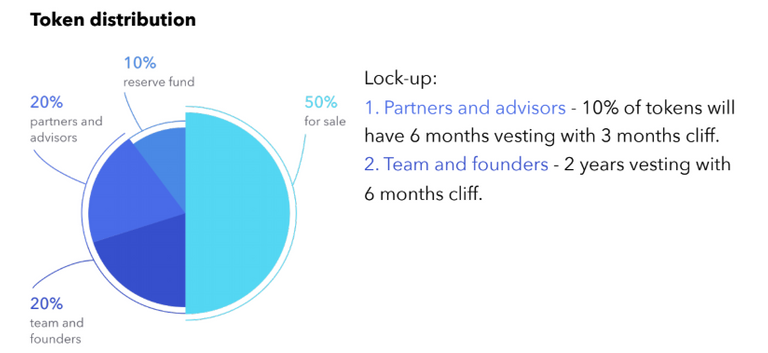
REMME gives a chance to forget about using passwords and upgrade the security of your private data on the more profound level. In fact, you can even develop your own security protocols based on the PKI system.

Author of the article - Gogul
https://bitcointalk.org/index.php?action=profile;u=1382097
0x4e05c5382e9ab309dd478eb4EAc258B9197d50e1