Bitcoin wallets, purses or wallets, other cryptocurrencies and crypto-assets store the private keys that are needed to access the balances registered in a public address or key of the corresponding block chain and be able to spend them. Currently there are several types of cryptocurrency portfolios that can be categorized using two variables: ease of use and security.
image
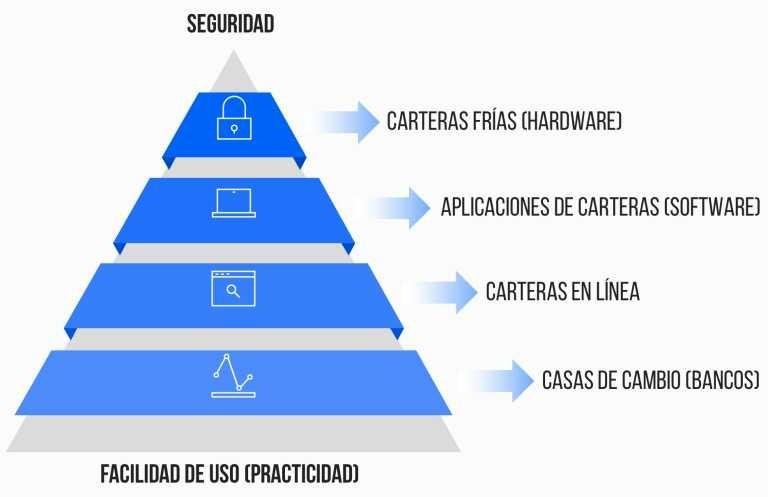
Types of cryptoactive portfolios, categorized by security and ease of use
At the tip of the pyramid shown in the image are the safest and most difficult to use portfolios, while in the background are the easiest to use, but also the least safe. The pyramid also represents the adoption in use of each type of portfolio: those of the fund are widely used, while those of the cap are not so widely used; a contradictory condition of the ecosystem of cryptoactive portfolios, given the fact that it is money with what we are dealing with. Safety is a determining factor in a good portfolio of cryptoactives.
Starting at the bottom of the pyramid, there are exchange houses, which act as a bank of cryptocurrencies: users enter their crypto-assets in an assigned address and the "bank" is responsible for managing them, that is, they move the money of the users to one or more central portfolios and from there they carry out the instructions of payment, purchase or sale that their clients indicate. They are useful for the exchange between cryptoactives and fiat currencies. These services are prone to hacking, scam, service drops and other risks, so that users' money may be unavailable or simply disappear; In addition, they usually change the conditions of use at their discretion, causing account closures and other inconveniences to users.
Some house exchange services are Coinbase, Poloniex, Bittrex, Xapo, Bitfinex, Bitstamp, LocalBitcoins and many others.
The exchange houses represent a business that allows the encounter between the real world (physical currencies) and the digital one (cryptocurrencies), although there are also those between cryptoactives. Users who store their savings in these services run the risk of losing their money. With the development of Bitcoin technology, advances such as Atomic Swaps will make its use unnecessary in the future.
One step further up the pyramid are the online portfolios: websites that allow users to mobilize their money independently, having exclusive control of their private keys and without having to install any software. In this type of purses (and in the following two of the pyramid) an abstraction of the private key is generated in the form of 12 or more words called seed or backing that must be written down by the user in paper or other resistant medium and outside of line, in order to safeguard your money.
In the online portfolios the probability of hacking users' funds decreases drastically, even so it is not zero, since a hacker could install some malicious code in the website and steal the seeds of the users who access the page. The unavailability of funds remains a problem in these purses, as they may suffer from temporary falls for various reasons.
Blockchain.info and MyEtherWallet are two of the most used online portfolios.
In the penultimate step of the pyramid are portfolio applications: softwares that can be installed on computers and / or mobile devices and serve as an interface to view balances in the addresses that the user has and mobilize the money in them. They can generate a new seed or use a previously created backup, as well as allow the activation of a code or extra key, at the software level, to mobilize the money.
These applications eliminate the problem of unavailability of money (unless you damage or do not have the device with the software nearby) and completely transfer responsibility for security to the user, who must keep his device free of viruses, refraining from entering insecure pages, connect to free Wi-Fi networks and insert any unknown peripheral, such as pendrives or external hard drives, into the system.
Examples of portfolio applications are Exodus, Jaxx, Electrum, Mycelium, Coinomi and Bitpay.
At the top of the pyramid are wallets in hardware, also called cold wallets: physical devices that hold the private key of associated accounts offline, which allows signing transactions without exposing the seed. These portfolios are similar to a pendrive, are connected by USB to the computer and represent the safest way to protect cryptoactive. These devices allow you to send cryptocurrencies even in unsafe environments, such as outside computers.
The portfolios in hardware are the only ones that generate a direct cost for the user. Their prices vary, but they can be obtained from $ 50 and up. Some recognized brands are Trezor, Ledger, KeepKey and Digital Bitbox.
ESSENTIAL CHARACTERISTICS OF A CRIPTOCURRENCY PURSE
Control over money: cryptocurrency portfolios can allow individual management (only the user owns private keys), joint management (the owner and the company own private keys), or by a third party (the company owns the keys) private) of the money stored in them. Depending on the control over the management of the money that is chosen, the responsibility and control of the user and the security of the funds in the portfolio increase or decrease.
Validation: cryptocurrency purses can be used to validate completed transactions, full validation (full node, fully download the blockchain), simplified validation (simple node, just download block hashes), or centralized validation (full node) of a third). Based on the type of validation used by the wallet, it must be trusted or not that a third party performs the correct validation of the transactions carried out.
Transparency: cryptocurrency purses can be completely transparent (the application code can be audited and verified by the user), transparent (the code can be audited, but can not be verified by the user), or nothing transparent (the code of the application is closed and the application runs remotely). Depending on the degree of transparency, the user should trust more or less that the developer of the application did not add secret or malicious codes that could cause them to lose their funds or be stolen.
Environment: cryptocurrency portfolios can be installed in vulnerable environments (prone to viruses) with or without two-step authentication, secure environments (such as cell phones where applications are isolated), and highly secure environments (such as physical cryptocurrency portfolios) , gadgets). Given the type of environment used, the user must activate mechanisms such as two-step authentication and place complex passwords to their portfolios and devices to avoid loss or theft of funds.
Privacy: cryptocurrency portfolios may or may not reveal information about their users to the network nodes (such as the IP address), re-use or not the addresses of the portfolios with each payment, and allow or not the use of the Tor browser to prevent other people or companies from associating transactions with the user's IP address. Depending on the type of privacy that the portfolio provides, the user should be more or less aware of the information that reveals the network.
#cryptocurrency #wallet #anarchy #money #new #news
#introduceyourself #introduce #bienvenida #video #youtube
@OriginalWorks