Sub Project Review Pt. 2

Foreword
Disclaimer: This article is not financial advice. The author is not a financial advisor and this article was not paid for.
For more information like this, join our Telegram, Discord and Twitter!
In the previous article, we covered some of the more remedial basics of how $SUB purportedly works by outlining the project's core tenets from their website and other published promotional materials.
In this article, we will be diving a bit deeper into the logical underpinning of $SUB's value offering as a cryptocurrency and comparing it to obvious, popular choices in their field with a competitive advantage such as, VPNs and TOR browsers.
Moving Onward With $SUB
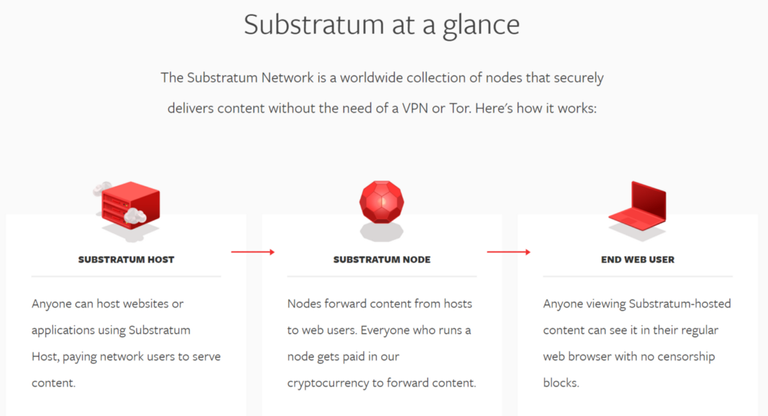
Almost as if they were reading my mind, the information following what I just reviewed on the website gives what it purports to be the technological facets of the underpinning that allows it to circumvent the process of having to use a VPN, dVPN, or even a TOR browser when it comes to surfing the web and accessing censored content.
According to the above graphic,
“Anyone can host websites or applications using Substratum Host, paying network users to serve content”
In my opinion, this is vague at best. So, I’ll reserve comment or judgment on the efficacy of this idea until later in the review when more information is given.
The above graphic also states that,
“Nodes forward content from hosts to web users. Everyone who runs a node gets paid in our cryptocurrency to forward content”
This is equally as ambiguous as the last statement (under the icon with a laptop), where the website states that,
“Anyone viewing Substratum-hosted content can see it in their regular web browser with no censorship blocks”
Again, this does not address the main issue at hand, which is avoiding detection from one’s government. Merely accessing the websites is something that a simple proxy could probably enable.
However, the issue at hand is not just merely accessing said websites but doing so in a manner where the communications will go undetected.
Below this is a section that’s titled,
“Our Technology Makes it Work”
Here, we'll see if we can answer some of the preliminary questions and concerns that were posed above and in the last article as well.
"Our Technology Makes it Work"

Since the idea still seems vague and relatively unsupported at this point, my next step was to click on the ‘See Our Technology’ button in order to get a better idea of how $SUB is proposing to make their project’s goal a reality.
Clicking On That Button Brought Me to This Page:
https://substratum.net/how-it-works/
‘How it Works’
Here, I expect to find out substantially more detailed information about exactly how $SUB’s protocol works.
At the top of the site it states,
“Substratum builds the decentralized web by leveraging the power of the individual. Anyone can publish, anyone can participate, and everyone is welcome to browse. Yes!”
Great.
Here's the Meat of the Idea:
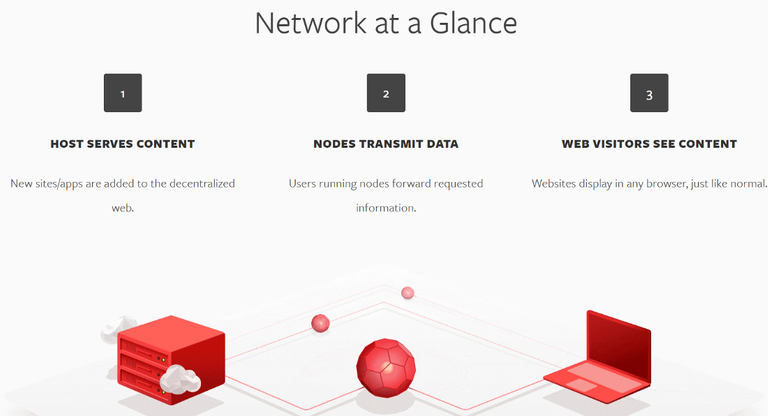
So, based on the image above and the other information presented on the page, I have a few concerns:
Concern #1
When it states that, “New sites/apps are added to the decentralized web”, that firmly implies to me that there is already some sort of protocol that $SUB has (similar to https or TOR), that users must register their own websites on.
That means that websites such as Twitter, YouTube, Facebook, Soundcloud, or whatever other very popular websites that one may want to use as a form of communication that is known by most people may not be accessible by most.
This is an issue for those that wish to communicate through those platforms specifically or reach a large/broader audience of individuals.
Example:
Suppose there is a civil war in a country, similar to the one going on in Syria currently. There are multiple different factions and conflicting stories coming out 0f the region about who is doing what to who and where and who the “real enemy” is. Let’s also suppose that there is some sort of nationwide censorship on all social media platforms.
In The Hypothetical Scenario Created Above, a VPN Would Be Useful for Two Reasons:
- It would allow any political dissidents or regular non-militant citizens/civilians to report on what is actually happening via recordings or ‘live posting’ and even call for help in some cases.
- It would allow these folks to access these sites covertly without being detected by their government (let’s assume that the gov’t is actively looking for those that try to bypass their policy and violations are punishable by death, internment camp or an unreasonably lengthy prison sentence).
From what I’ve seen on their site, $SUB would not satiate either desire.
It seems that $SUB would fail to:
a) Give people access to those platforms, which is major.
b) Provide some sort of mechanism that encrypts the transmissions of its users.
These are two HUGE drawbacks.
Concern #2
Some of this was addressed in concern #1, but I have an issue with the lack of information on the protocol that this decentralized web would be using. For example, your Google Chrome/Firefox/I.E. is a browser that is able to read http and https sites (there are a couple other extension prefixes, but those are mostly used for LAN connections or your personal computer’s files).
Specifically, for the internet, the new standard is https. The reason that this is used is because it is substantially more secure because it encrypts transmissions on websites. HTTP does not do this.
TOR sites, on the other hand, use an entirely different protocol with a host of sites on the “deep web” that can only be accessed via onion routing. This onion routing service makes it next to impossible to detect someone’s web traffic. Communications are obfuscated via this method as well.
The question that remains here is, ‘What is the protocol that $SUB uses?’ since they claim to host web domains and that peers on their network serve as the direct hosts.
And also, 'How is the protocol and packet routing method that $SUB employs as secure as https? How do we know?'
In addition, ‘How is it that people are able to connect to $SUB-enabled domains via a regular browser?’ Based on the author's knowledge of internet protocols and packeting, it seems virtually impossible for $SUB to operate through a regular browser like Google Chrome without either:
a) sacrificing a substantial amount of proposed ingenuity
and/or
b) Forcing users to use a protocol that has not proven to be demonstrably safe at a level or standard that is enjoyed by https protocols.
I ask these questions specifically because $SUB claims that there are no additional downloads needed in order to reach the websites that are being hosted by individuals on their server.
Concern #3
This may be my biggest concern — and that is trust.
What guarantees that the nodes forward the necessary information? They could easily transmit false information in order to phish users. This has happened to numerous legitimate websites in the past (MEW wallet is a recent example that comes to mind in the crypto sphere) via the hacking of either their domain's nameserver, ISP, or the website itself (to force it to redirect to an alternate IP address).
In order to understand my concern here, I need to explain a bit about how the internet works:
- Each website that you go to on your browser has a name, right? Let’s take twitter.com for instance.
- ‘Twitter.com’, in computer logic, does not actually mean anything. What ‘twitter.com’ actually is, is a ‘display name’ or a username for an IP Address.
- When you type in ‘Twitter.com’ in your browser, this information is sent from your browser through to the router or whatever connection you have to the internet.
- Your router receives said information as a ‘request’ to access ‘twitter.com’. Your router does not know what ‘twitter.com’ is either.
- Your router moves this request through major connection hubs nearby in a mesh networking fashion (on a macro level) in order to reach the nameserver.
- The nameserver is where this information is hosted. This is where the GoDaddy’s of the world host your web content.
- Once the nameserver (something like a GoDaddy or an Amazon) is reached, it already knows “Oh, Twitter.com? Okay that’s IP address 182.23.13.21” and it will dig up the page information that has been requested and send it back to your router.
- Your router sends that information back to you.
- Twitter.com loads up.
Summarizing the Process
What I wrote above is a very basic version of how the internet works.
How VPNs Work
VPNs are able to obfuscate your ‘identity’ on the internet through processes like SSH tunneling.
What this means is that VPNs essentially encrypt your transmissions before it even hits your router. So it will take your request to ‘twitter.com’ and encrypt the request itself, then it will send the request to the router, which will then forward it to the VPN’s server itself.
The VPN server will then decrypt the information and send it to the nameserver themselves.
So, the nameserver will be aware that a request has been made — there’s no way around that. But, it won’t be known who made it.
Your VPN will then route that information all the way back to you, at which point it will then be decrypted at the last possible point so that you can see the page.
The encryption that happens here is not necessarily the exact same as what you’re probably familiar with when it comes to bitcoin (i.e., through hashing a private key to formulate a public key w elliptic curve cryptography meant to reduce/eliminate the incidence of collisions)
I do not see any comparable process with $SUB, which is an issue.
Conclusion
The whitepaper analysis for $SUB will be released soon in conjunction with this report. Once that happens, we’ll be able to evaluate on a bit of a closer level exactly what $SUB’s model/framework is for implementing the goals that they state on their website as well as any other claims that they have made about their ecosystem.
For the time being, though, it seems that the statements that they have made are a bit lofty and, in lieu of the essential privacy that’s desired in these types of situations where a VPN would be sought, I don’t see how they could possibly compete…At all.
Congratulations @proofofresearch! You have completed the following achievement on Steemit and have been rewarded with new badge(s) :
Click on the badge to view your Board of Honor.
If you no longer want to receive notifications, reply to this comment with the word
STOP