In my last two posts, I described the process of Proof of Work and explained the details regarding the economics of Bitcoin mining. With this post, I remain in the domain of mining and want to have a look at the infamous 51% attack. If you're new to my blog or unfamiliar with mining-related aspects of bitcoin, I recommend the check out the following two posts first:
- Steemit.com/@sblue: Proof of Work - Sudoku on a planetary scale! — Steemit
- Steemit.com/@sblue: The Economics of Bitcoin Mining

Image by TheDigitalArtist - Source: Pixabay.com
Introduction
If you do your research on Bitcoin, one of the first things you will encounter is the 51% Attack. It is a very crucial detail of the Bitcoin ecosystem. One that is often not fully understood, which is why I'd like to explain it in detail in this post. Two cases need to be distinguished when talking about the 51% Attack: Changing the Future and Changing the Past. Although both can be approached utilising the 51% Attack, changing the past is significantly harder than changing the future. In this blog post, I'll focus on the 51% Attack employed to alter the future. I will explain the details of a 51% Attack that changes the Past in a future blog post.
The 51% Attack - Changing the future
Let us have a look at how the 51% Attack can be utilized to change the current blocks and the blocks to be mined in the future.
The Blockchain, Hash Rate and Proof of Work
As explained in my previous blog posts, mining is used to process transactions and secure the network. Transactions are packed into a block by a miner who then tries to find a nonce value that results in a hash of the block header that conforms to the requirement given by the current difficulty. This makes creating a block difficult, is called proof of work and creates the tamper-resistant Blockchain of Bitcoin. In this post, we will primarily focus on the Blockchain and the Hashrate as illustrated in the image below.
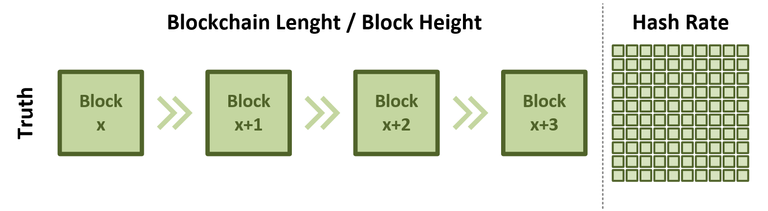
Bitcoin Blockchain - Block Height & Hash Rate. Illustration created by @sblue. Each Block depends on its predecessor and provides the hash of its block header to its successor. The Hash Rate provided by all miners is illustrated as 100 small squares, representing 100%. The illustrated version of the Blockchain is considered to be the truth since no conflicts exist.
Each time a new Block is created, the Blockchain length (also called Block Height) is increased by one block. Each block depends on its predecessor and provides the hash of its block header to the succeeding Block. Proof of Work is utilised to achieve immutability, backed by the Hash Rate supplied by every miner in this world. Depending on the Hash Rate, Difficulty is adjusted to sustain a Block Time of 10 Minutes.
The Consensus - Resolving Conflicts
Whenever there are two conflicting versions of the Bitcoin Blockchain, the consensus algorithm of Bitcoin resolves this conflict by choosing the longer chain as the new truth. This simple consensus algorithm works because Proof of Work makes it difficult to mine a block. There's work involved in creating each block, which makes a consensus algorithm as simple as "The Longest Chain Wins" possible.
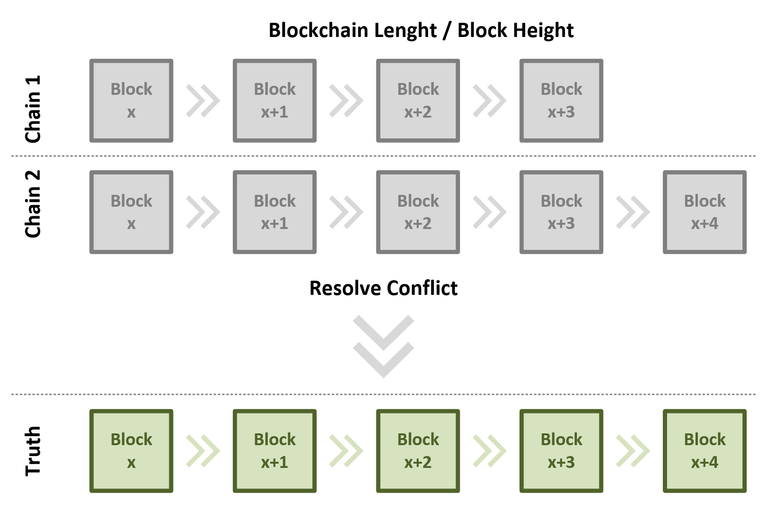
Bitcoin Blockchain - Conflict resolution. Illustration created by @sblue. In any case of conflicting versions of the Bitcoin blockchain, the longest chain is considered to be the truth.
Executing the 51% Attack
Given the facts above, we can now have a closer look at what the 51% Attack is, how it works and what it would take to execute it. As the name suggests, the 51% Attack requires the attacking party to obtain 51% of all the Hash Power available. This Hash Power is then used to mine new Blocks privately. Because the attacking party owns more than 51% of all hashing power and mines a private/hidden chain, the length of that hidden chain will eventually overtake the length of the public one. Once the hidden chain is more extended (higher Block Height), it can be announced to the public and will be accepted as the new truth, given the fact that it's the most extended chain. It is possible that a longer chain can be achieved with less than 51%, but 51% is required to have certainty that the attack is successful.
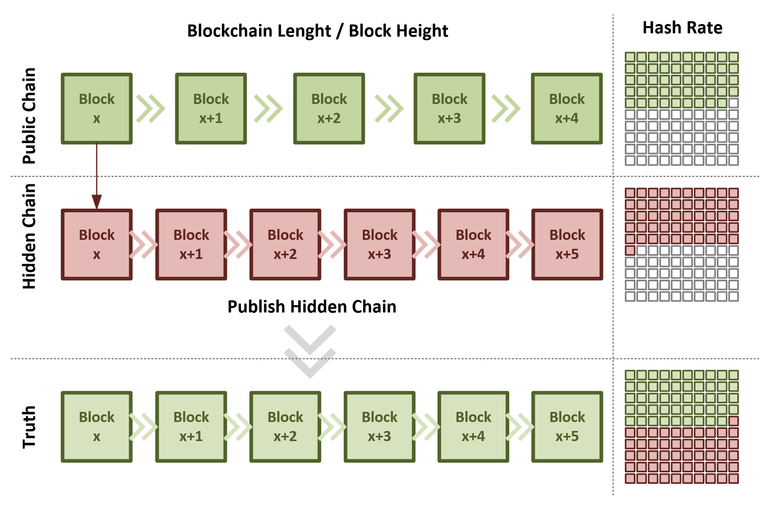
Bitcoin Blockchain - 51% Attack. Illustration created by @sblue. Once an attacker was able to acquire more than 50% of the global hashing power a hidden chain can be mined that will eventually surpass the length of the public chain. Once the hidden chain is longer than the public one, it can be published an will be accepted as the new truth. Allowing double-spending of any Bitcoin that is owned by the attacking party.
An attack like this would allow the attacker to double spend Bitcoins, prevent transactions from gaining confirmations or prevent other miners from mining any valid blocks. Let's have a look at the double spend issue. Given the image above, the attacker starts mining a private or hidden chain on block x. While doing so, the attacker would then buy all sorts of expensive stuff like a house, a Lambo or other things, spending Bitcoins through transactions on the public chain. Once the attacker spent all the Bitcoins on the public chain, the hidden chain that was mined privately, will be published. If the announced chain, not containing the transactions of all the expensive stuff the attacker bought, is longer than the current public chain, it will be accepted as new truth. If enough time passed, the attacker already got all his goods bought on the old public chain and regained all Bitcoins since they were spent in a version of the chain that is no longer valid. And this is the 51% Attack utilised to perform a double spend transaction.
Problems in Practice
Although the attack seems rather simple in theory, with the current hash power, it is considerably hard to execute it. Besides the fact that it needs incredible amounts of Hash Power, the attacker would also need to time the attack correctly. The time of the attack should be chosen in regards to Difficulty adjustment, to prevent an incentive of new miners joining the operation on the live chain. Furthermore, 51% of hashing power can be obtained using two possible ways: Acquiring new Hash Power slightly higher than the current Hash Rate or executing the attack with Hash Power that was already acquired at an earlier point in time.
Price
According to blockchain.info, today's Hash Rate is at 28'623'865'750 GH/s. An attacker can now either somehow acquire (or already acquired) 51% of this Hash Power or the attacker acquires another 28'623'865'750 GH/s + 1%. It is immediately clear that this requires considerable amounts of money. 51% of the current Hash Rate is 14,598,171,532.5 GH/s and would require approximately 1'042'727 Antminer S9, providing 14 TH/s (14,598,171,532.5GH/s / 14'000GH/s). Considering the price of $1'450.- per miner, the resulting investment for this attack amounts to 1'511'954'150.- USD (1'042'727 * $1450.-). Another choice would be to acquire new hash power, which exceeds the current one. This would result in the need of (28'910'104'408GH/s / 14'000GH/s) approximately 2'065'007 Antminer S9 providing 14TH/s of Hash Power. The investment in this venture would amount to 2'994'260'150.- USD (2'065'007 * $1450.-). Besides the huge investment, an attacker would also need to install and configure the hardware and pay the rent for housing as well as the electricity needed to run 1 to 2 million miners. As you see, with today's Hash Rate, the sheer amount of devices and money required, makes a 51% Attack almost impossible.
Timing
Besides the fact of a huge upfront investment, timing is another crucial component. We have to remember that we are in an ever-changing ecosystem. The volatility of the Bitcoin price impacts the Hash Rate as well as the Difficulty of the main chain. With progress in time, an attacker would need to sustain 51% to be successful. If the attacker starts right before a bull run, the elevation of the Bitcoin price could incentivise additional miners to join the operation on the public chain, requiring the attacker to upgrade the hash power accordingly. Another factor related to timing is Difficulty. If an attacker chooses to utilise existing power, the 51% Hash Power would be taken from the public network, causing a significant drop in Difficulty when the next adjustment happens. Until Difficulty is adjusted, both chains would operate with a significantly higher Block Time with chances of new miners joining the live network even before Difficulty is adjusted.
Execution with new Hash Power
The attack with new Hash Power assumes that an attacker chooses to acquire new Hash Power that amounts to a value higher than the one on the public chain. Bringing the advantage, that the start of the attack would not be noticed since there would be no Hashing Power dropping out of the live network. Besides the fact that this is a stealth attack, it doesn't force an adjustment of Difficulty on the live network due to a decrease of it's Hash Rate, thus not incentivising new miners to join the operation on the live network. The only thing that impacts the Hash Rate and Difficulty of the live chain in this scenario is the change of the Bitcoin price itself. On the downside, this attack is twice as expensive to execute compared to the execution with existing Hash Power.
Bitcoin Blockchain - Execution of 51% Attack with new Hash Power. Illustration created by @sblue. The Attacker acquires new hash power that exceeds the hash power currently in existence. The hash power is represented by small squares. Since the attacker acquired new hash power, the sum of total hash power of the public and hidden chain amount to more than two times the value of the public chain.
Execution with Existing Hash Power
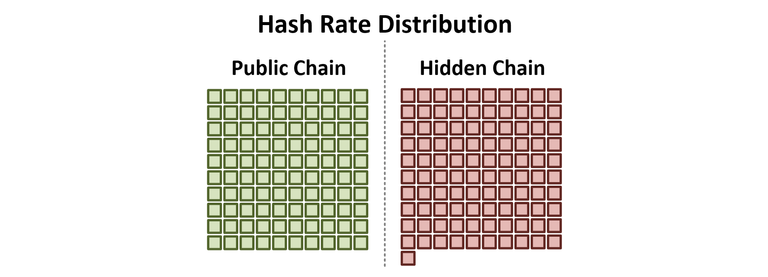
In this scenario, the attacker acquired 51% of all the miners running on the live chain and decides to start the attack, by stopping to mine on the public chain and starting to mine a private, hidden version of the Bitcoin blockchain. The moment the attacker launches the attack, 51% of the total Hash Rate will disappear from the network. Alerting all users of Bitcoin around the world, that something fishy is going on. Furthermore, it would result in a temporary increase of the Block Time, that will result in a massive decrease of difficulty as soon as the block for adjustment has been reached. Since both chains operate from the same starting-block, increased block times would apply to the attacker's hidden chain as well as to the real chain, slowing down the creation of blocks by approximately 50%. The most significant problem for the attacker is the fact, that once Difficulty adjusts, there will be a massive incentive for new miners to join the live network, forcing the attacker to upgrade the mining operation of the hidden chain accordingly. Although the situation can be affected by timing the attack depending on the adjustment of difficulty, the difficulty adjustment remains in favour of the public chain, since only the public chain provides real rewards, while the rewards of the hidden chain can only be claimed in case of a successful attack. For the attack to be successful, the attacker would need to sustain 51% Hash Power, resulting in additional investment and a higher effort to perform a successful attack.
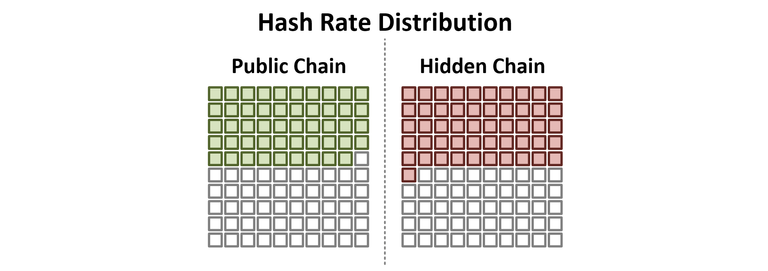
Bitcoin Blockchain - Execution of 51% Attack with existing Hash Power. Illustration created by @sblue. The Attacker moves 51% of the existing Hash Power to a private/hidden mining operation, creating a hidden chain. The hash power is represented by small squares. White/empty squares represent the hash power that is missing compared to the previous 100%.
Conclusion
Although the principles of a 51% Attack are rather simple it is almost impossible to execute it, considering today's Hash Rate. The amount of required resources (Money, People, Locations, Electricity) is so high, it is far beyond of what one individual could acquire and execute. Even if the attacking party is a group or an agency funded by a government, the required resources are so significant, that it remains almost impossible to execute the attack. Besides the sheer amount of resources, there are other uncontrollable aspects that make the 51% Attack even harder to execute. The changing price, as well as the continuous adjustment of difficulty, would only allow sustaining the attack for a short period of time. Furthermore, the rewards of the attack are limited to double spending of Bitcoins the attacker already owns, prevent transactions from gaining confirmations or prevent other miners from mining any valid blocks. The attacker would not be able to reverse other peoples transactions that happened before the attack, could not prevent any transactions from being sent at all and can not change the numbers of coins generated per block. Furthermore, the attacker can't create new coins other than the Block Reward and would not be able to spend Bitcoins not owned by him/her. Considering the possibilities as well as the limitations, performing a 51% Attack is an unviable venture with a reward that doesn't match the effort and risk that need to be taken. Even if someone acquires 51% of all hashing power, the Risk/Effort vs Reward ratio of honestly mining blocks surpasses the one of attempting an attack by far.
I hope I was able to give you an overview of how the 51% Attack works. Although the attack looks rather simple in theory, I hope I could illustrate how difficult, resource consuming and risky it would be to put such a plan in action. If you have any questions, feedback or input, please leave a comment below.
Thanks for reading and have a great day!
Sources and Additional Information
- Bitcoin.org - Bitcoin Whitepaper
- Bitcoin.org - Open source P2P money
- GitHub.com - bitcoin/bitcoin: Bitcoin Core integration/staging tree
- Bitcoin Wiki
- Bitcoin Wiki - Controlled supply
- Majority attack - Bitcoin Wiki
- Weaknesses - Bitcoin Wiki
- Books – Andreas M. Antonopoulos
- Blockchain.info - Bitcoin Block Explorer
- Bitmain.com - Asic Bitcoin Mining Hardware From Bitmain
- Bitmain.com - Antminer S9
- CoinWarz.com - Cryptocurrency Mining Calculators and Profit Calculators
- Cryptocompare.com - Mining Calculator Bitcoin, Ethereum, Litecoin, Dash and Monero
- YouTube - Ivan on Tech: 51% Attack
- YouTube - Ivan on Tech: 51% Attack II
- CoinMarketCap.com - Cryptocurrency Market Capitalizations
- Pixabay.com - Stunning Free Images
- Steemit.com/@sblue - The Economics of Bitcoin Mining
- Steemit.com/@sblue - Proof of Work - Sudoku on a planetary scale!
- Steemit.com/@sblue - WTF is Money? And why Bitcoin is more than just a currency.
- Steemit.com/@sblue - What is Bitcoin? - When Money becomes a content type!
- Steemit.com/@sblue - What is Git / Github? - The 3 minute journey through Bitcoins GitHub history
- Steemit.com/@sblue - Introducing Crypto-Puzzles
Hello @sblue. Great. You got my upvote and resteem. Thank you for sharing.
Hey @olivia94! I'm happy to hear that you liked my post. Thanks for your comment and resteem!
I'm listening to you on TOTL right now with @ethandsmith and @awakentolife - and i love your outlook on this!!! This post might be over my head - but I will try to dig into this right now :) really enjoying your perspective that you're sharing live!!! :)
Hey @dreemsteem! Thank you for your kind words. I'm happy to hear that you like my post / first appearance on TOTL. Due to a long day and a small timezone issue, I was almost too tired to present and tempted to only listen in. In hindsight, it was the right decision to get my first run in presenting and it was a pleasure being on TOTL. 😊👍
I agree!!!! I'm so glad that you came too hehehehe and will look forward to the next time!! :)
great read I upvoted and followed you
Coins mentioned in post: