Ok. I'm going to respond to several people at once because my business partly revolves around Monero Mining and the use of browser mining... And this might be long winded.
Back in October of 2017, while developing VidYen as an alternative to YouTube (but with the standard adverting model but more like a F2P game) I saw the article about Pirate Bay putting Coinhive browser miners on their website without telling their users and I was:
"That is terrible and unethical! But damn what if that technology could be used to monetize sites ethically? I'd rather use it than watch a bunch of advertisements taking up my time."
So I started working on Coinhive API's a way to track users so they could get recognition for mining. See, most of these sites just felt they could just drive by users and get away with silent mining, but you sort of notice when your CPU goes up to 100% or you battery drains in 90 seconds hanging out on a particular site.
So I (and a few other non-related projects) felt that if you gave the user the ability to consent and control the experience (say a CPU control or a stop button) you can make a better experience than advertising ever could.
Now the problem was that when we test with Coinhive, users antivirus would complain and Malwarebytes was screaming that Coinhive was a virus and malware, but the miner itself was not.
I'm a veteran from the 2008 adware wars and even though I use adblockers by default, I remember fixing dozens of computers in IT which the malware was just shoving ad popup after popup in the employees face.
The mining itself is not the malware just like the ad itself wasn't either, it was the delivery system, but most AV's and others that speak out against Coinhive and Monero.
Now Coinhive didn't help things as they turned a blind eye to the issue while not really helping out those who wanted to use this ethically. The begrudgingly made authedmine which supposedly always forces consent, but they didn't turn off the servers that didn't. They also stop responding to my emails so I realized I would need to move on.
I ended up actually using an open source miner that, I'm 99% sure was used for mass scale silent mining. But I slapped an interface on it that required consent gave the user control.
Now I get approached every now to deployed silent miners and confess I don't outright tell them no at first, but explain the logistics and try to convince them to put a consent system in as it would keep their users from being angered off and report them to Malwarebytes and then have the site blacklisted. As I know it would only take 5 minutes to find the same miner on GitHub and if I can steer them towards a consent system then... Well... We can shift it to a legit business. (Sometimes I feel like I'm in a weird nerd episode of Narcos on Discord where they are trying to go legit)
Now the logistics...
Browser mining of Monero is pretty easy to deploy. Requires no installation of software and can be done by very non-technical persons with five minutes reading how to embed javascript. (That said... If you are interested and non-technical just install my VidYen Point system on a WordPress site... The consent, reward tracking, and controls are built in wheres Coinhive you have to do all that yourself)
And let me be upfront.... Browser mining is highly inefficient. And considering the market prices the hashes per XMR for USD payout is quit low.
My guess... And this will depend on the machine. Is that you are going to get any where from 1 h/s for mobile user to 5-10 1 h/s with desktops.
I left my workstation on over the weekend to test the current hash rate (trying to make it more efficient) and this is the results from an i7 which is basically a gaming rig that can play Star Citizen.
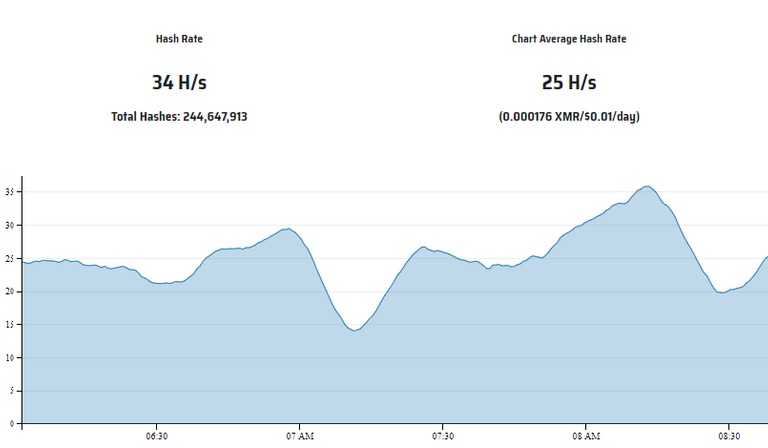
According to MoneroOcean, I am making $0.01 a day... And this computer is 24/7. Not really that efficient.
Its all CPU btw so browser mining does not tie into GPU at all and its running through javascript.
Now to answer the question... Why would you do this if the payouts are so poor per device.... It's simple...
It's free electricity and it scales even better.
Sorry for the bold, but even crypto mining experts don't get this point. The reason that they try to install silent miners it is all free electricity... And to my point it can be for ethical miners who sell a digital servers like media, content, or virtual gaming items (one day... one day... I'm working on it. I already got a mining to WooCommerce solution... So it is possible.)
Now let's get to the other issue... Miner (the person) tend to be min/maxers. Which mean they still act like the electricity costs them something or they want full effort even though its more likely to detect them.
Which is why when they go bad, they often try to install XMRig on your system and get the GPU as well.
Now considering, even Windows 10 defender will report that this is malware (along with Malwarebytes and every other competent AV), it is a bit harder to get the user to install and get past the systems.
But if they can they get access to the GPU. Now I can get 25 h/s with my CPU via my browser mining, but I can easily get 120 h/s with XMRig on my 980ti for a reference on the same pool which I guess is $0.05 a day or so?
Now, it is unlikely that most people will be running gaming rigs, but if you infect 10,000 computers at even $0.01, that's $100 a day easy.... So at that point you see why they want to do it.
And you'd be surprised who is not running AV and modern systems. I've seen someone on Discord claim he's infected a scam IRS call center in India when he found out they were running pirates versions of Windows 7.
And even today, was talking to someone who came on the pool Discord saying his work had go the server from XMRig installed on a computer at his work to which I gave some external suggestions ("Install Brave browser on every workstation and make it the default so if someone clicks on a Phishing link it will go through Brave first")
HOWEVER, as a fan of XMR Mining and browser mining (as well being in the business of it), I do not like it... It makes it harder to be accepted as a legitimate business and your one misreport away from Malwarebytes blacklisting you.
And to the article... I'm glad the XMR devs are promoting this. Yes, because of the privacy features, criminals use it, but they use BTC just as much for their bitlocker ransom ware.
XMR is not the means nor the malware. Its just the end goal.
Thanks for this post!
Wow. Such a complex comment.
I appreciate @vidyen for taking the time to write it all down. Seriously hell of a good job.
Yours
Piotr
This deserves more votes