
Dating Problem
Santa Catalina, in the Lovers Cove. Emma and Michael meet accidentally. Both don’t know Catalina . Both are tourists. Michael is lost. He would like to ask Emma for the way to his hotel, Hamilton Cove. And maybe whether she would like to drink a hot chocolate with him. But he doesn’t know her. And if she says no? “I would ask her, if only I knew that she would accept”, he thinks. But he is shy. Too shy.
Emma is lost as well. She would like to ask Michael for the way to her hotel. And maybe whether Michael would be willing to accompany her or not. It’s already getting dark. She would of course then invite him for a cup of hot milk with honey. And some coffee cake. In order to thank him. And maybe … who knows. But what if he says no? Should she dare to ask? “If I knew that he would not laugh at me, I would ask”. But Emma is shy. Too shy.
They cross each other. Watching each other. Not asking each other. Finally, they both find their way. Michael to his hotel, Emma to hers. The wrong way. They will never meet again.
If only they would know the techniques of secure multi-party computation.
One of the famous problems in the area of distributed protocols is the so-called “dating problem”: Emma and Michael want to find out whether they both want to date each other, but each of them does not want to tell whether he/she wants to date or not. A bit more formally, Emma and Michael both hold a bit INPUTa and INPUTb, respectively, and they want to compute the AND of the two bits. And of course, if one of them inputs 0, then he/she should not learn the bit of the other one.
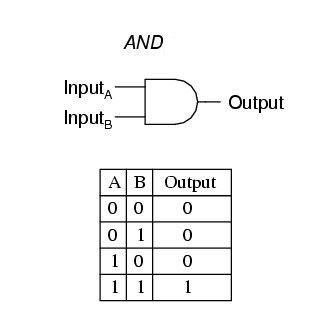
AND LOGIC
This problem is a very simple instance of a general problem:
How can a set of players (e.g. Emma and Michael ) compute an arbitrary function (e.g. the AND) of their private inputs (e.g. INPUTa and INPUTb) in such a way that all they learn is the result, but they all learn nothing additional about the other player’s inputs? Surprisingly, this problem can be solved. The technique to solve is called secure function evaluation (SFE)
There are many other attractive problems that are falls in these criteria:
In Yao’s millionaires problem, two millionaires want to find out which of them is richer, without revealing their actual wealth. In Chaum’s spymaster problem, a set of spymasters want to find all double-spies without revoking the anonymity of “honest” spies.
An even more powerful concept than SFE is multi-party computation (MPC). Here, the participants cannot “only” evaluate functions of their inputs, but they can get the help of a (virtual) trusted party. This trusted party assists the players in every possible aspect (where securely evaluating functions of the players’ inputs is just one possibility).
MPC has many practical applications. Using MPC, any system involving a trusted party can be realized without need for such a party. As an example, stock markets heavily depend on the honesty and independence of some central service, which every investor must trust.
But what if the functionality of this central service can be distributed among a set of players (e.g., among the investors themselves), and thereby creating a trustless environment ?
This is where Enigma fits.
Enigma is a decentralized computation platform with guaranteed privacy. It’s goal is to enable developers to build ’privacy by design’, end-to-end decentralized applications, without a trusted third party.
Now wouldn’t it be amazing to have a trustless third party, rather than having to rely on a centralized one Enigma uses secure multi-party computation (sMPC), in which data queries are computed in a distributed way, without a trusted third party. Data is split between different nodes, and they compute functions together without leaking information to other nodes. Specifically, no single party ever has access to data in its entirety; instead, every party has a meaningless piece of it.
“It is scarcely possible to read the news without seeing yet another reason to be able to perform computation on encrypted data.”
Unlike blockchains, computations and data storage are not replicated by every node in the network. Only a small subset perform each computation over different parts of the data. The decreased redundancy in storage and computations increases efficiency.
Everyone loves to say this or that thing is the next ETH, next BTC , next Google(Some say Enigma is) etc. I won’t, because this is cryptoland. It’s all about creating a new way of doing things, new technologies that are alternative to the existing structure. I won’t comment on price(or Mcap) because you wouldn’t believe me anyway If I say that this is worth billions.
Now Why do I think ENIGMA will be big?
It’ll be a data marketplace(“Data is the new oil”) where you can buy, sell and compute on encrypted data. You can read about various applications of ENIGMA in the whitepaper. If you still can’t imagine how big ENIGMA will be I’ll try to explain by giving some more examples:
Take two drug companies. Each has a database of molecules and toxicology test results. They want to combine their results without revealing what molecules are in the databases. What can they do? If they decide to use the Enigma Platform, they can synergistically share their results without giving away their proprietary data.
A common problem in Supply chain collaboration is that partners are not willing to exchange the necessary data, such as costs and capacities, for security reasons. They fear disadvantages in future collaborations, e.g. price negotiations, due to the insight into their price calculation. This is even often true for simple data exchanges, such as in vendor managed inventory. Secure computation can implement these planning techniques provably without disclosing the input data.
Using secure computation to avoid satellite collisions. The growing number of satellites orbiting the planet is increasing the danger of collisions. This is not only a theoretical scenario, and two satellites actually crashed in 2009. This could be avoided by sharing (exact) information about the satellites orbits. However, satellite owners are not willing to make the orbits of their satellites public. But using MPC, the parties can cooperate and learn whether a collision is going to happen and nothing else!
Credit rating for small banks. A farmer runs into a bank…He need loans to support their companies, and the banks want to assess how well the farmers are doing to find out what is the probability that the farmers will go bankrupt and not pay the loan back. Big banks have many clients, so they have a big sample to compare with. But small banks do not, and they would like to have access to more data to jointly credit-rate farmers. This is a classic MPC scenario, where each bank inputs his database of clients, and the new farmer can input his data and figure out his ranking and nothing else.
E commerce websites like Ebay… I don’t think this one needs explanation.
Secret-ballot voting is one of the most attractive applications of multiparty computation. A secure voting scheme guarantees the correctness of the tally while preserving the privacy (and independence) of the votes. The function to be securely computed is the sum of the votes.
Hospitals generate large amount of patient data. Combining data could be of help in developing better diagnosis and treatment tools. Govt. policies protect patient privacy. It would be easier if everyone could work on encrypted data and compute some desired function of the data.
So if there’s a set of mutually distrustful parties in a distributed network to compute a joint function of their private inputs without disclosing anything beyond what is already revealed by the function output, Enigma protocol can be used there
The concept is so broad that it can’t be covered in one post. Make sure to read the whitepaper and generally about MPCs. If you have any questions regarding Enigma or it’s token ENG you can ask the team on one of their community channels
Telegram- https://t.me/enigmacatalyst
Discord- https://discord.gg/8VGM8k8
References
https://enigma.co/enigma_full.pdf
https://enigma.co/
https://scholar.google.com/
https://en.wikipedia.org/
Thanks for the layman's explanation of what Enigma is trying to solve. I have a lot of faith in the team and their vision, but it'd good to hear it from other's perspectives.
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://medium.com/@kt008/solving-the-so-called-dating-problem-with-enigma-protocol-278262b455ff
Haha I like your approach from a dating perspective! Well writen :)