Whenever I discuss the blockchain technology, I usually begin my narrative with Bitcoin. The reason for that is quite simple: everybody is familiar with the term Bitcoin to some degree or other. GReAT experts have told the team all there is to know about this famous crypto currency, and some of us even tried mining for Bitcoin blocks when this project first started. Put simply, Bitcoin is a technology for transferring value from one party to another bearing in mind that both parties do not trust each other a priori. Bitcoin operates on the basis of a distributed database of transactions — the so-called blockchain. In even simpler terms, a blockchain is a set of protocols and technologies for distributed storage of transaction data, while Bitcoin is a crypto currency that utilizes such properties of blockchains as decentralization and anonymity to achieve greater stability and earn more trust from users. The blockchain is structured in a way that network participants automatically reach a consensus on the contents of the blockchain records, while guaranteeing the invariability of records and the overall network security. Let me illustrate this using an example: suppose you need to transfer funds using a blockchain protocol. Transactions happen among a certain number of network participants among whom trust is not required. There is also no need for the involvement of a particular centralized trusted authority (such as a bank) that would guarantee the validity of transactions.
It would seem like an absurd and impossible situation, since all participants in this type of commercial process want to be certain that an exchange of items of value has taken place in one way or another. So how can a consensus be reached in a distributed network where participants do not trust one another? The secret is quite simple: a blockchain is not merely a technical implementation of the transaction transfer protocol; rather, it is a kind of ecosystem at the juncture of technologies and economic principles. In other words, a blockchain loses a number of its properties in the absence of economic principles. For starters, let us begin by looking at the blockchain structure from a technical perspective.
As its name suggests, it is a chain of blocks:
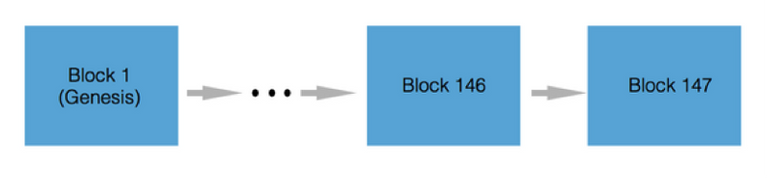
These blocks and their chain are generated according to specific rules and synchronized among all network participants.
In turn, each block consists of a header and a list of transactions. The block header in turn includes: its own hash, the hash of the previous block, the hash of transactions, and additional service information.
The hash of any block consists of the hash of transactions. As a result, all information about the completed transmission of data is stored, and it cannot be spoofed without replacing the entire block. In this way a block becomes a kind of container for a set of transactions. Meanwhile, the presence of the hash of the previous block allows arranging blocks into a chain and provides protection against block spoofing. It is a quite reliable algorithm, isn’t it?
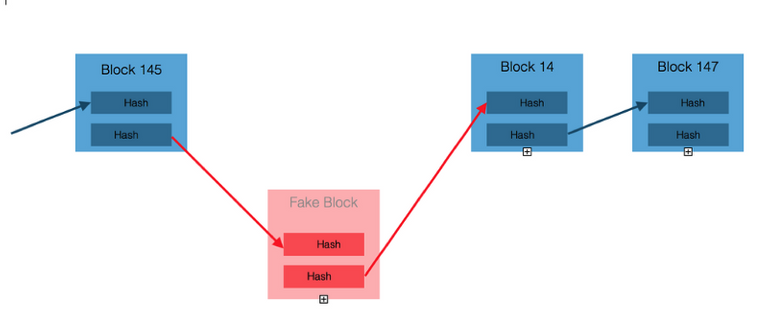
Let us look at the rules according to which a block is generated. This is where magic begins, making the blockchain resistant against hacking by the transaction recording and transmission system. Here are a few essential principles that guarantee a transparent and decentralized network:
All network users have access to the complete copy of the blockchain and store (or have the capability to store it) on their systems;
Any network user can generate blocks;
Users are rewarded financially for generating blocks;
A computing problem has to be solved to generate a block;
Now let us examine this in more detail. The first and second items on the list are more or less clear. I should only mention that storing the entire database copy is not obligatory in modern versions of blockchains. Regarding the third item: users are rewarded for generating a block, which creates an economic incentive to attract additional users who will generate new blocks. This process of creating blocks is known as mining and the person creating them is called a miner. We will come across this term many times subsequently.
The fourth item is the most interesting of them all. What kind of computing problem is that? This is where the Proof of Work principle comes into play. Incidentally, it deserves a whole separate chapter.
The problem can vary depending on the blockchain implementation. As a general rule, it involves computing a certain hash in a way that allows solving the problem only using the brute force method.
As I mentioned at the very outset, blockchains are associated with the circulation of crypto currency in one way or another. Since Bitcoin is the most popular crypto currency, let us examine the operating principle of the blockchain as exemplified by this currency. Imagine that you have a set of transactions that are not yet included in the blockchain but are only candidates for inclusion. Miners receive these transactions and enter a competition of sorts for who can generate a specific block sooner than others and receive a reward. As I mentioned earlier, generating a block requires solving a certain computing problem. The problem involves generating a hash (the SHA-256 function). It should not be just any kind of hash; its numerical value has to be less than a certain number N. The result of SHA-256 is unpredictable, which is why the right hash can be chosen only using a brute force search. This usually requires a large number of recalculations that use up CPU/GPU resources of the mining computer. Once the block hash satisfying the rules has been found, the miner generates a block and sends it to other network participants for verification. If the block has been generated correctly, it is included in the chain and the miner receives a reward. Note that the rate at which blocks are generated does not change despite the growing network capacity (number of participants). The speed is balanced by complicating or simplifying the computing problem (by increasing or reducing the number N).
After reading all this, you probably ask yourself the perfectly natural question: Why is all this needed? The answer is quite simple: for network security. After all, the network has certain inherent problems and threats that are neutralized in the blockchain. I am totally serious!
The network is distributed, and sometimes a parallel branch of blocks can form because miners were either unaware of one another or acted wrongfully on purpose (e.g., to perform the transaction in one chain and then spoof it in another). How should the only valid branch be selected? A rule applies whereby the main branch is the one where more CPU/GPU resources have been expended on generating this branch, i.e. essentially the branch containing more blocks. So if a miner starts a separate branch of blocks with its own history of transactions (either accidentally or intentionally), this branch will be declared dead sooner or later and discarded by the network. Transactions in this branch are canceled.
A separate branch (the lilac branch in the figure below) can become the main branch only if it is longer than the main branch (black); this can happen if more CPU/GPU resources are expended on generating the lilac branch compared to the black branch. This is in turn possible when somebody controls 51% of the network’s computing power.

In addition to this threat of the blockchain branching off, there are also other threats, but I think they should be covered in a separate article to avoid overloading the reader with information.
The economics of the process are the most interesting aspect of this technology.
The network owes its security in many ways to the economic incentives embedded in the protocol. Let us examine the main questions that you may have and answer them right away. So:
Why are users willing to expend their computing power on mining?
- They are rewarded for successful mining.
- When the number of miners decreases, the probability of successful generation of a block increases, which raises the probability of a reward, which in turn attracts new miners. This makes the network a self-regulating organism.
- The reward for miners should be understood as a collective payment for network security and operation. Depending on the blockchain implementation, the reward is either accrued by the protocol (by generating new “coins”) or provided as a per-transaction fee, or both.
- A miner is interested in successful mining. To generate a block, the miner needs a copy of the blockchain all the way to the last block, which creates an incentive for the soonest possible network synchronization.
- The miner receives a reward only for a block generated in the main and only blockchain branch. When the miner expends resources on mining in a parallel branch, this miner is wasting resources, which stimulates miners to work in the main branch.
What if somebody secures 51% of network power?
- The probability of this scenario does not equal zero. What’s more, there used to be a mining pool close to this situation, and this pool voluntarily scaled down its power to avoid crossing this threshold. Why? Because this pool has already invested heavily in the mining infrastructure and risked undermining trust in the network and thereby reducing the value of its investments to naught.
There is currently a fairly large number of various blockchain systems. For example, you can view the top 100 blockchains here. By looking at these systems, you can get a rough idea as to the diversity of this ecosystem. Incidentally, all systems appearing in that ranking have their own features and numerous differences. For example, not all of them use Proof of Work approaches. Some of them try to stand out from among the others by focusing on a specific problem (which is yet another topic for a separate article).
Nonetheless, all of those systems use two important and quite different approaches to using this technology.
A public blockchain is a system fully open to any user. Any user can connect to the network, view the history of transaction and even participate in mining. We have already discussed the operating principles of a public blockchain, and it is in this type of blockchain in particular that economic incentives for users are so important. Bitcoin is the best-known example of a public blockchain.
It is a class of blockchain systems in which only participants authorized by a certain centralized operator (or operators) can participate. For example, this can be an implementation of a protocol for performing transactions between certain subsystems or between companies. In this case, the principal value of the distributed network architecture is the ability to reduce or entirely remove the load from centralized services. Economic incentives embedded in a public blockchain are used on a limited scale or not used at all. For example, a miner generates blocks not because it receives a reward directly but because it is a dedicated server within a company, which was allocated specifically for serving the local blockchain system.
As a result, a permission blockchain system loses many of the economic mechanisms that served as protection against spam, duplication, and similar threats. However, some threats become irrelevant or significantly mitigated in some real-life applications of permissioned blockchains. Let me give you a few examples:
- Etherium blockchain, any transaction requires spending “gas” (an internal term representing “coins”); in this way the network protects itself against flooding and unmotivated participants. In the case of a permissioned blockchain, this charge may be canceled, but this does not result in flooding because only authorized and responsible participants join the system.
- In a public blockchain, miners perform mining in exchange for a fee and in this way keep the network secure. In a permissioned blockchain where exchanges happen between two parties, simply dedicated servers can act as miners on both sides, and it’s enough to make sure that the computing power of one side does not exceed 51%. Of if the parties trust each other, a large number of miners becomes unnecessary altogether. Incidentally, in such systems PoW is often replaced by Proof of Authority, which is also a topic for future articles.
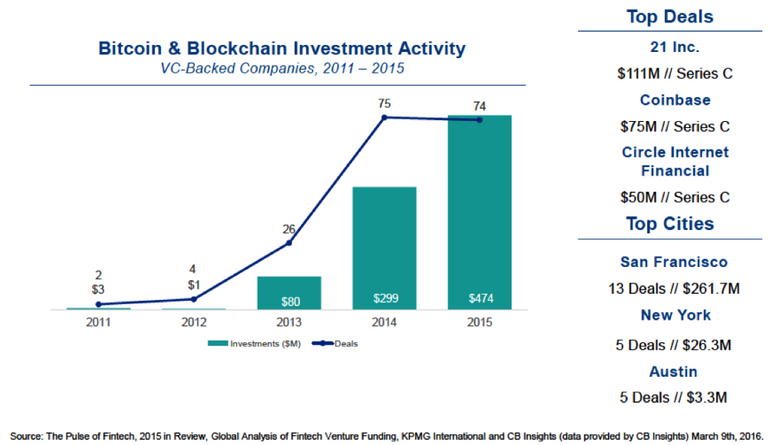
As you can see, the amount of interest in blockchains has increased drastically over the past three years. Not surprisingly, blockchains are particularly interesting for the finance technology industry. And yet the use of blockchains is not limited to the financial sector alone. The blockchain operating principles are perfectly suitable for industries that roughly meet the following criteria:
- There are two or more parties that have no reasons to trust each other 100%;
- There is an intermediary whose services are expensive;
- There is an intermediary untrusted by the parties;
- A history of changes/actions needs to be documented reliably;
Needless to say, these are not obligatory criteria, and they are not always sufficient. However, they provide an excellent starting point for considering the applicability of blockchains. What are the possible examples of applications? Here are a few classical examples:
- One of the biggest current trends is IoT (Internet of things). A blockchain allows arranging transactions and micro-transactions (it is important to single out micro-transactions because they are currently rendered impossible by commission fees and similar centralized system maintenance costs) between a machine and another machine or between a machine and a human. In this way, we can implement economic interaction among drones. Consider a relevant real-life example: sharing of hard drive space among different participants (computer, NAS), etc. You can configure the client application to lease out some of the space and collect a certain amount of rent for it. There are already startups like that.
- Another example where the property of blockchain invariability is utilized are systems that record information about diamonds in a blockchain. A diamond has a number of characteristics that allow establishing the identity of a specific specimen conclusively. In other words, there cannot be two diamonds with identical sets of characteristics. This allows creating the hash of a diamond, recording it in a blockchain, and keeping track of the history of the diamond’s origin, sales and purchases. This is important for jewelry and insurance companies.
- Ripple network: This is an example of a permissioned blockchain in which banks can exchange transactions without the involvement of a centralized intermediary (SWIFT). This approach reduces the cost of transactions and allows for much faster processing.
- Or consider a DNS records storage system. There is already a blockchain network that allows registering a domain. In this case, the database of domains is stored in the blockchain in a distributed manner, and blocking access to one of the domain becomes quite complicated.
- At a recent conference, I encountered an excellent example for using a blockchain. There is a market for factoring services (in simple terms, when a supplier sells goods and the buyer needs a payment deferral, factoring services come into play). This causes the supplier to experience a cash gap. The factoring company buys out the debt from the supplier at a certain interest rate. One of the major problems in this market is that a supplier can sell its debt to several factoring companies at once. Meanwhile, factoring companies are unable to form a single database because they have reasonable fears of a takeover of their business by major competitors. A blockchain is perfectly suited for such scenarios. Each debt can be recorded in the form of a hash (based on financial transactions properties) into the common blockchain, and any factoring company can conclusively check whether or not this debt has been sold already without disclosing information about the debt itself. It’s an ideal example of real-life application.
Originally published at https://polys.me/blog