
If you have known anything about blockchain and cryptocurrency it’s definitely because of the encryption that comes with cryptocurrencies. Since 2009 the blockchain has evolved, leading the way with basics about blockchain which had to do with decentralization of the currency, the immutable transactions, the Smart contract technology and the most inviting of them all is the anonymity behind transaction on the blockchain. These fundamentals of anonymity of the public chain 2.0 have turned it a safe haven for crimes such as money laundering like illegal drug sales, human trafficking and a whole lot of wrong stuff going on lately. Usechain is out with landing project that will usher us into the blockchain 3.0. It’s basically a first
Let’s meet Usechain
The Usechain public chain is built on basics of the blockchain but created with many “firsts” such as the mirror identity protocol (MIP) to deal with the anonymity that comes with the transaction on the blockchain which has actually affected adoption of the blockchain technology by governments, large corporations.
Major competitors
Usechain as a platform has many firsts to offer but has stiff competition from the Bitcoin , Ethereum and the EOS. Now let’s look at the distinguishing technology between Usechain and these competitors.
The distinguishing technology behind Usechain
Security & Performance
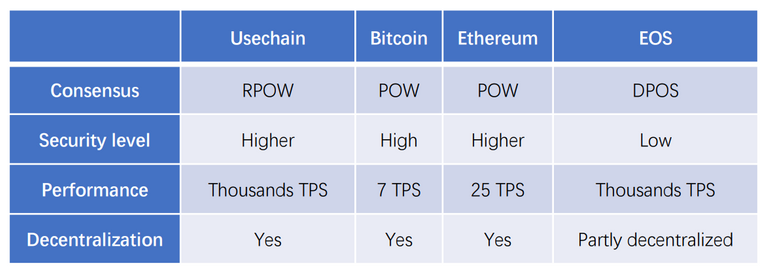
Core to Usechain is the verified identity on the blockchain, the mirror identity protocol is more concerned with security and performance where many startups are really not paying attention to. This form of security is of two verified layers wherein the mirror identify protocol makes use of verified addresses on all transfer. This is against the type of security performance obtained on the EOS which is terribly low and quite better with the Bitcoin while the same level of high security is gotten from the Usechain and Ethereum.
Initially, the verification process will be handled by several third-party agencies, that will lay track for any Investigation should there be the need for any. This will obviously puncture the idea that the blockchain technology is a safe haven for money laundering crimes.
Sharding
The Usechain public chain is also introducing sharding technology in the identity blockchain which is also a foremost introduction to the blockchain technology. In this case, a set of transactions on the networks are divided into different nodes on a shard on the network which meant to increase the speed of transactions confirmation on the network that amounts to thousands of transfer per sec just like the EOS. This is contrary to the way other blockchain companies carry out confirmation using all nodes on the network to perform confirmation of transaction leading to a huge delay in completion of transactions like the Bitcoin and the Ethereum which performs 7 transfers per sec and 25 transfers per sec.
Also, sharding technology protects the Usechain public chain from possible attacks and increased capability to accommodate more transactions. The sharding technology is integrated into the Internal Virtual Machine to enhance computational operation while reducing cost and enabling support for existing subchains. The Identity Virtual Machine (IVM) is adaptable to detecting loopholes in smart contracts. The IVM on the Usechain identity blockchain is meant to verify contracts while they are being compiled basically securing both end users issuing and receiving the smart contract on the Usechain platform.
On a regular blockchain, a single address is created and not verified to the owner, however, Usechain utilizes the main address and a sub-address. Both of these addresses requires a verification to initiate any transaction making the security on Usechain much more advanced from other blockchain enterprises.
Consensus
From inception, the foremost computation of consensus algorithm used was Proof of Work (POW). The proof of work was created to allow the fastest node to carry out the needs accounting function utilized by the Bitcoin and the Ethereum except for the EOS that uses DPOS. It is noteworthy to mention that proof of work consumes more electricity which is expensive unlike the Random Proof Of Work (RPOW) utilized by the Usechain public chain. The software-based RPOW doesn’t consume as much electricity as the POW and is hundred times effective for the whole system.
My thoughts
The Usechain public chain is here with many “firsts” which is an obvious frontier for what the blockchain should look like. Honestly, most loopholes found in other blockchains are corrected in the Usechain and in my opinion, it’s the public chain of future.
Questions regarding this innovative Mirror Identity Blockchain, are welcomed from our esteemed readers.
Additional information on Usechain can be gotten from their Website or the Whitepaper.
Website: https://www.usechain.net/
White Paper: http://www.usechain.net/usechain_en.pdf
Technical White Paper: http://www.usechain.net/usechain_tech_cn.pdf
Facebook:https://www.facebook.com/UsechainFoundation/
Twitter:https://twitter.com/usechain
Github: https://github.com/usechain