
The U.S. Department of Justice (DOJ) recently announced the indictment of a Russian national and an organization he allegedly operated, the bitcoin exchange BTC-e, for operating an unlicensed money service business, money laundering, and related crimes.
“BTC-e was noted for its role in numerous ransomware and other cyber-criminal activity; its take-down is a significant accomplishment.” - Michael D’Ambrosio, Special Agent in Charge of the US Secret Service Criminal Investigative Division
Vinnik was arrested in Greece early on Wednesday, and will face charges in the U.S. The 37-year old allegedly owns and operates multiple accounts tied to the operation of BTC-e, and is also a primary beneficiary of BTC-e's managing shell company, Canton Business Corporation. Numerous withdrawals from BTC-e administrator accounts went directly to Vinnik’s personal bank accounts, the DOJ claims.
The indictment alleges BTC-e was operated to facilitate transactions for cybercriminals worldwide. The exchange received the criminal proceeds from numerous computer intrusions and hacking incidents, ransomware scams, identity theft schemes, bribes to corrupt public officials, and narcotics distribution rings. The investigation has also revealed that BTC-e received more than $4 billion worth of bitcoin over the course of its operation. “BTC-e was used to facilitate crimes ranging from computer hacking, to fraud, identity theft, tax refund fraud schemes, public corruption, and drug trafficking,” the DOJ states.
The indictment also alleges that Vinnik received funds from the Mt. Gox hack, and laundered these funds through various online exchanges, including BTC-e and the early bitcoin exchange Tradehill, which was based in San Francisco.
“Mr. Vinnik is alleged to have committed and facilitated a wide range of crimes that go far beyond the lack of regulation of the bitcoin exchange he operated. Through his actions, it is alleged that he stole identities, facilitated drug trafficking, and helped to launder criminal proceeds from syndicates around the world.” - Chief Don Fort, IRS Criminal Investigation
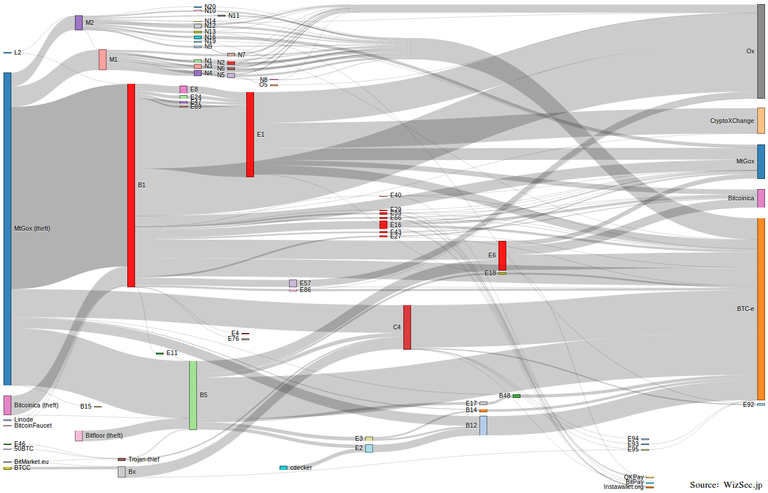
Soon after the mainstream press broke the news of Vinnik’s arrest on Wednesday, Kim Nilsson of the WizSec Bitcoin Security blog published a detailed blog post announcing that “Vinnik is our chief suspect for involvement in the MtGox theft (or the laundering of the proceeds thereof).”
What followed was the first of a series of posts revealing the results of their three-year investigation, which Nilsson says can be talked about publicly now, with Vinnik in custody. The “result of years of patient work,” detail many facets of the case, from the complete flow of the missing coins to a timeline of events that ties the MtGox theft to others major thefts in the bitcoin sector including Bitcoinica and Bitfloor.
Short for Wiz Security Consulting, WizSec is a blockchain-focused security startup based in Tokyo, Japan. Their funding comes directly from Bitcoin companies around the world looking for answers about the MtGox case, along with a general effort to strengthen their security against cryptocurrency theft.
The otherwise-unknown security startup has no formal website outside of their blog. “WizSec has been investigating the MtGox crash since soon after it occurred, making us probably the longest running non-official investigation,” the blog’s oldest entry says, in a post dated February 2015. To this day, the in-depth investigative results posted on the blog are among the most detailed on the subject of MtGox.
Nilson states that the WizSec investigation turned up evidence that identifies Vinnik not as a money launderer, not a hacker or thief, “his arrest news also suggests this is what he is being suspected for. He may have merely bought cheap coins from thieves and offered a laundering service.” As we reported in May 2015, WizSec holds little hope for retrieving the bulk of the 300,000+ stolen coins from MtGox.
According to Nilsson’s findings, the MtGox theft was initially performed in 2011, around the same time that BTC-E was founded. BTC-e was the third oldest and one of the largest bitcoin exchanges in operation, with approximately 700,000 users, according to the indictment. It also held the distinction of being the only exchange with any useful amount of traffic that didn’t require some form of identification from its users. This greatly helped BTC-e gain popularity, allowing users to obscure and anonymize transactions and the source of their funds. By lacking any anti-money laundering processes, the exchange acted like a magnet to cyber criminals, the DOJ's document detailed.
Located in Bulgaria, with a presence in Cyprus, the exchange also allegedly maintained a base of operations in the Seychelles Islands. The exchange’s web domains were all registered to shell companies in, among other places, Singapore, the British Virgin Islands, France, and New Zealand. The court document revealed that since its inception, the exchange has processed several billion dollars worth of trades.
“BTC-e was an exchange for cybercriminals worldwide, and one of the principal entities used to launder and liquidate criminal proceeds from digital currencies, including Bitcoin, to fiat currencies, including U.S. dollars, Euros, and Rubles.” - Court Document
Proceeds from well-known hacks and thefts from bitcoin exchanges were allegedly routed through a BTC-e administrator account associated with Vinnik, the DOJ claims. In particular, the exchange received a substantial portion of the criminal proceeds from one of the largest ransomware schemes, Cryptowall. An innovative trendsetter in modern ransomware, Cryptowall turned into a whole family of file-encrypting malware, which first appeared in early 2014.
In addition, BTC-e has been doing “substantial business” in the U.S. but failed to register as a money service business with the Department of Treasury. It further had “no anti-money laundering process, no system for appropriate “know your customer” or “KYC” verification, and no anti-money laundering program as required by federal law,” the DOJ detailed.
As such, FinCEN is seeking a $110 million civil money penalty against BTC-e “for willfully violating U.S. anti-money laundering (AML) laws.” Additionally, Vinnik is being charged $12 million for his role in the violations. If found guilty, Vinnik faces up to 55 years in prison on top of the fines. However, “Additional fines, restitution, and supervised release also may be ordered,” the DOJ concluded.
“We will hold accountable foreign-located money transmitters,” said acting FinCEN Director Jamal El-Hindi, “including virtual currency exchangers, that do business in the United States when they willfully violate U.S. AML laws.”
“Exchanges like this are not only illegal, but they are a breeding ground for stolen identity refund fraud schemes and other types of tax fraud. When there is no regulation and criminals are left unchecked, this scenario is all too common. The takedown of this large virtual currency exchange should send a strong message to cyber-criminals and other unregulated exchanges across the globe." - DOJ
Please vote and i will upvote
upvote https://steemit.com/photograpy/@pinkbiru21/rumoh-aceh