****One of our bots recently discovered a new and sophisticated Hit BTC phishing device. We decided to dissect it.****
Is that HitBTC?
HitBTC is a cryptocurrency exchange, on average, more than $ 250mln of daily volume.
Like most cryptocurrency exchanges, HitBTC uses Cloudflare for DDOS protection and, like most cryptocurrency exchanges, it has a tendency to go down during high traffic periods. During this time it is not unusual for users to view Cloudflare anti-DDOS waiting screens, Cloudflare snapshot pages, or other Cloudflare error pages. You will immediately see why this is relevant.
The Phishing Kit
The logic behind this phishing device is very smart, but this makes it quite difficult to detect that you are not in a valid domain.
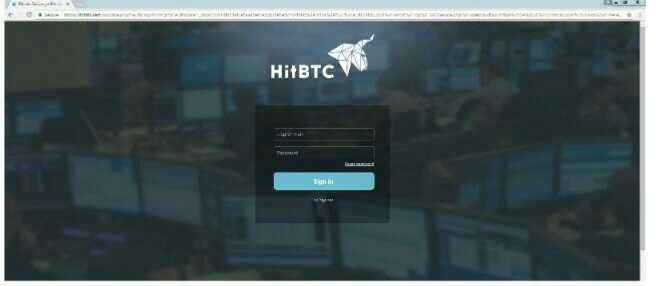
The phishing domain is currently hiding behind Cloudflare's proxy - we have issued a removal request - but this is what the victim will experience.
*Users enter their email and password into the login form on the phishing site.
*The user clicks on the "Enter" button. If we cancel obfuscate JavaScript, we can see the following code is executed when we press "Enter".
*An iframe from the screen that mimics CloudFlare's waiting screen is displayed while user details are sent to the backend script that tries to enter at HitBTC.

*If the log in is successful (because the user does not have 2FA enabled), the user is shown a 502 Cloudflare error screen. Six seconds later, they are redirected to the legitimate HitBTC domain. At this point, user login details have already been stolen.

*If the login is not successful (because the user has 2FA enabled), the user is slipped into Cloudflare's waiting screen. Seconds later, they released 2FA forms.
*After users enter their 2FA code, the code is sent to the attacker's backend, a small login, and the user returns to the legitimate domain.

Regardless of whether or not the user has 2FA enabled, after the phishkit has login details, it will display Cloudflare 502 errors and redirect the user to a legitimate domain.
What makes this phishkit so dangerous is that users cannot detect that they have just been compromised:
*Even if users suspect something might be wrong and decide to check the URL, they are now in a valid domain. They must see their browser history to see that they enter their details on a phishing website.
*It's easy to write experiences as errors and assume something is wrong during the login process. This makes perfect sense because how phishkits use Cloudflare to wait for familiar screens / errors when they test logins.
Deeper Diving

When we investigate the backend scripts, we see that they have an application running on port 5000. We know this because a regular error view brings up the traditional Nginx page:

However, if we navigate to anything with a path of /^twofa/ then we get a different view:

The known background scripts (called via XHR) are:
POST /register
POST /twofa_short
GET /getcsrftoken
Playing a victim
I created a HitBTC throwaway account (without 2FA enabled) and submitted my details. The following network logs:

As you can see, the background script (called POST / register) responds with an OK response - meaning the backend application can enter my HitBTC account. I was then shown the Cloudflare wait screen and then transferred to a valid domain through 302 There is a redirect.
Now that the bad guys have my details, I assume they will create an API key that will give them full access to my account. They will then use this access, perhaps, buy shitcoins by a large margin, as we saw with Binance. That said, at the time of the analysis, there was no API word created. It is possible that they only create an API key if there are coins or funds in the HitBTC account.

What can you do to stay safe?
As you might collect now, the internet is "wild-west" and even more so when dealing with cryptocurrency. The attackers are increasingly sophisticated and it is increasingly difficult for you to detect that you are on a phishing website.
*Never save all your funds on the exchange.
Use a cold wallet with any coins that you don't actively use.
*Spread coins on multiple exchanges and use a different username, email address and password.
Always use 2FA (although that doesn't always help in this case).
*Always check the URL before entering your login details.
*Navigate to your crypto website through bookmarks that you create yourself.
*Regularly check your account and check unnecessary API keys that you no longer use or don't remember making.
*Close all active sessions to your account that you no longer need.
*Activate all notifications and notifications available to the exchange. Matters such as buy / sell orders, creation of new withdrawal addresses, creation of new API keys, login process from unknown devices, and any other features provided by the exchange. We recommend that you be notified if there are changes as soon as possible.
*If something is missing, take the time to take a closer look (for example, check the URL, check your browser history.) Don't rush to make mistakes and don't ignore things.
*Install EtherAddressLookup, which will block you from visiting URLs that are known to be malicious (such as the phishing website above!)
*Report dangerous scams and phishing websites to https://etherscamdb.info. We also index all of these phishing websites there if you want to check something or look deeper into the diversity of fraud.
Thanks for using eSteem!
Your post has been voted as a part of eSteem encouragement program. Keep up the good work! Install Android, iOS Mobile app or Windows, Mac, Linux Surfer app, if you haven't already!
Learn more: https://esteem.app Join our discord: https://discord.gg/8eHupPq