
A new security threat, namely cryptojacking, is born following the explosion of cryptocurrency, Cryptojacking is defined as the unauthorized use of the resource of your computing device to perform cryptocurrency mining. A handful of video streaming sites as well as the notoriously popular torrent site The Pirate Bay have been accused of cryptojacking their users, not to mention the public wifi provider of one of the Starbucks outlet in Buenos Aires.
Do you perhaps notice a slow down in your system performance after surfing the web for awhile? There is good chance that you have also been cryptojacked! ( Or maybe not. Maybe it is just time taking its toll on your computer 😂 ) However, even if you haven’t been cryptojacked yet , you should read this article as well to enlighten yourself on the subject and inform yourself with the possible preventive measures that you can take to avoid falling victim to this new form of cybercrime. As the cyberspace advances, there will be emergence of more new and creative forms which cybercrime can take. As digitalization becoming more and more prevalent in various aspects of our everyday life, these attacks aren’t likely to go away soon, especially in the realm of cryptocurrency where the entire space is still in its infancy. Therefore, it is our duty to always keep ourselves educated and informed. Here’s a few other common cyber attacks that you should also be looking out for. ( We will cover these individual attacks in the near future )
- Malware, spyware, ransomware
- Phishing
- Password Attacks
- Distributed Denial-of-Service (DDoS) Attacks
- Man-in-the-Middle” (MITM)
- Drive-By Downloads
- SQL Injection Attack
- Cross-Site Scripting (XSS)
- Malvertising
- Rogue Software
- Social engineering/cyber fraud
Alright, enough babbling. Let’s have a closer look on the subject and what can you possibly do to prevent yourself from becoming a victim.
What Is Cryptojacking?
Cryptojacking basically implies that someone has hijacked your personal device to make use of its CPU power to mine cryptocurrencies. The hijacker execute the crypto mining code on your computer without your knowledge to capitalize on the computing power of your device – known as Hash Power. The only sign you might notice is an overall decline in system performance or lags in execution.
Previously, to be susceptible to such an attack, one has to install some sort of malicious software. However, things have evolved. Now, just a small embedded JavaScript is sufficient to makes use of the processing power of just about any device that visits such sites. ( In browser cryptojacking ). JavaScript runs on practically every website that you visit, You load the page, and the javascript mining code just executes itself. No need for installation, and no need to opt-in and whatsoever. Hackers hack high traffic websites to insert their mining scripts while some online businesses make use of mining scripts as a way of generating alternative income for their business.
How To Avoid Cryptojacking
We are not completely sure of the legal implication of cryptojacking as of right now but what we are certain is that, it is unethical because they are taking advantage of unsuspecting Internet users without their consent.
People who have their devices hacked will observe their devices heating up quicker or battery draining faster or power utilization of the CPU will suddenly increase.
You can check if you have been hacked and your system power is currently being used to mine digital currencies. Simply open your task manager and look at your CPU usage for your browser.
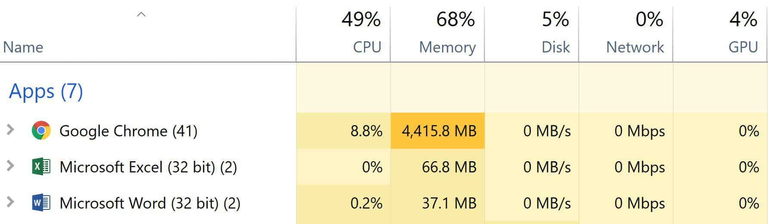
You can also avoid future in-browser cryptojacking with the aid of some techniques, tools and plugins. Some of them are:
- Nocoin ( Chrome Extension )
Nocoin is a free chrome extension that helps you to block websites from hijacking your CPU power. This open-source extension will detect the presence of such activity and provide you with the option of blocking the activity or whitelisting the website.
minerBlock ( Chrome Extension )
Similar Extension as described above.
Anti Miner ( Chrome Extension )
Another Option
No Script ( Firefox Extension ) / Script Safe ( Chrome Extension )
You can also use JavaScript-blocking extensions such as Noscript ( For firefox ) or ScriptSafe ( For Chrome ) to prevent the mining script from running. However, such extensions could be quite aggressive at times and could prevent the normal functionality of the websites as it disables all scripts from running on pages.Adblocker
Another alternative that you can use is adblocker. If you know specifically which websites are guilty of such activity, you could manually add the website to your list of blocked domains.Opera Browser
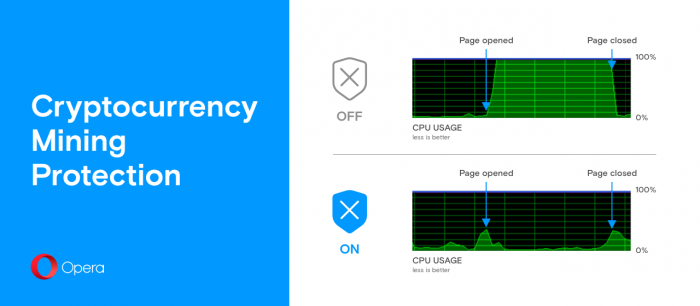
Opera has recently integrated mining protection in its browser. The feature is automatically enabled the moment you switch on the browser's default ad blocking tool.
Coin Hive
Coinhive is the company behind the common JavaScript miner popularly used for for cryptojacking ( although the company expects the websites using their services to ask for the users' consent ). If you wish to explore crypto mining scripts, Coinhive offers this service in a number of innovative ways including:
- Flexible JavaScript APIs
- Proof of work short links
- Proof of work captcha
Conclusion
Until now, thousands of websites and millions of individual users have been cryptojacked. Crypto mining without consent ( aka cryptojacking ) is no doubt a condemnable practice, however , In browser crypto mining itself is something truly innovative. It has created a brand new way of online monetization. Some websites that employ such monetization methods are very honest about this and notify you as soon as you landed on their page and seek for your consent to "borrow" your CPU power. ( They should also inform you how much processing power they are intend to utilized ) Some of users don't mind it and find this a better idea that traditional ad monetization while others have a different opinion. Have you ever been cryptojacked? What's your opinion on this new way of online monetization? Let us know your thoughts in the comments section below!!
Unfortunately, until regulators target Coinhive and similar out-the-box Cryptojacking services; there is no stopping this. Jmho
Source:
What is Cryptojacking ? And What Can You Do To Prevent It