One of the main objectives of REMME is protection against various harmful attacks. After fast technology developing in connection online, important information security presently came in big demand. Development of Internet global network was far exceeding usual exchange parts of information, having connected the most various sides of our everyday life, being incorporated even in domestic appliances. Big Data, various portable devices, which can be of all forms force us to think of how to get proper protection for the important data which are transmitted through communication channels irrespective of who are you, service supplier for companies or just ordinary user.

$ $ $ How does REMME work? $ $ $
The fundamental of REMME is based on different levels (kind of multilevel architecture) and represent following levels:
- Physical.
- Communication channel.
- Transportation and network level.
- Application and session level.
- Representation level.
- Application level
Now we can look how base platform of REMME will be able to provide reliable protection to different companies which need real strict security and ordinary people against multilevel threats.
$ $ $ DDoS $ $ $
There are two different types of the DDoS-attacks, for example - low level (flood), and also next step which is high level (repeated inquiries to application). Most of the attacks relating to such low level, which can be done through a communication channel. Also those which belong to high level - through application level. Platform as well as SSL can limit considerably free access to request on either channels (IP Sec) or transportation level at once.

$ $ $ Hardware Trojan $ $ $
In this case platform provides indirect protection against virus hardware which can extend through his physical shape. If the general Disk USB works as key logger, then REMME can soften considerably losses of data as internet user shouldn't introduce passwords. The digital document can be offered for all compatible with USB devices (option is planned in the following REMME).

$ $ $ MiM attack $ $ $
Harmful means can take root and change information which belongs to the new victim, replacing on its fast and hidden way most useable components of the system. And by the way there are many ways for such attacks, for example, ARP simulating, the attacks to routers of the BOUNDARY GATEWAY PROTOCOL and replacement of the present answer of the DNS server. Just to get strait in network movement, will be only enough to just change the BOUNDARY GATEWAY PROTOCOL of Internet service provider. You won't really necessary to do something unusual to crack the router, because BOUNDARY GATEWAY PROTOCOL doesn't offer cryptographic identification of information secure exchange and part of network.
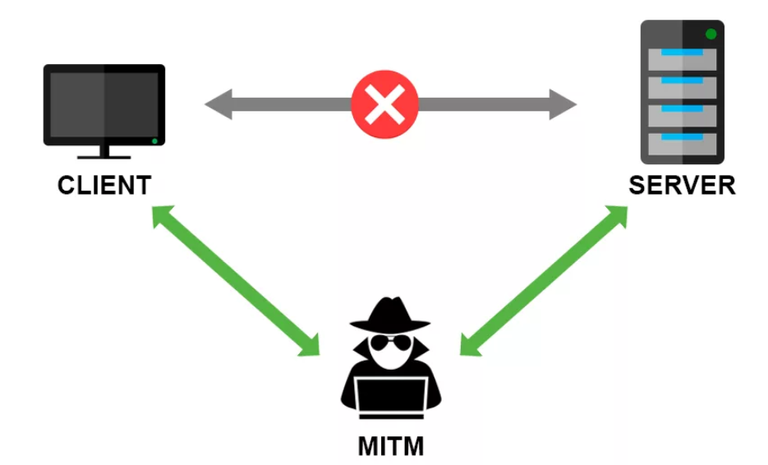
New technologies of enciphering REMME allow to eliminate interception of data or replacement of standard protocols with the unsafe switch of channels on protected ciphered (for example, the protocol of strict transport safety of HTTP which always forces the browser work with it). Usually it not always possible to parry attacks on MiM using for such thinks just usual standard certificates (when somebody get full access to somebody for certification), REMME can provide all necessary protection against attackers, as they won't be really able to make the present counterfeit documentations like the real owner, who logging in the secured system.
$ $ $ Pharming $ $ $
This way redirects the user directly to artificial IP address. So, and by means of the false reply from DNS, because it is rather easy to take the consumer, who even knows nothing about it directly in a framework, turning him vulnerable for the subsequent phishing or much more serious attacks. Platform technology will help to find whether it is available for system which you are going to work with the not valid signature.

$ $ $ Cases with Scripting $ $ $
This dangerous type of virus distribution adds the harmful external script for the website which works with data on the any available web page, for example, duplicating and sending all information to the working server. REMME itself can't directly change this situation, but can considerably minimize consequences from powered attack on users as all information which are used for user’s fast identification been stored in reliably protected storage of different data keys. Thus scenarios from the internet page won't get access to these data and often slightest suspicious actions have to receive confirmation through 2FA.
$ $ $ Team $ $ $
$ $ $ REMME project links $ $ $
https://remme.io/
https://t.me/remme
https://twitter.com/remme_io
https://www.facebook.com/remme.io/
https://medium.com/remme
https://drive.google.com/file/d/0B1jTRGmj_3khUV9RTERnYzNvaE0/view (Whitepaper)
https://bitcointalk.org/index.php?topic=2060387.0 (ANN)
https://bitcointalk.org/index.php?topic=3611368.0 (Bounty)
$ $ $ $ $ $ $ $ $ $ $ $ $ $ $
Username - Micronoid
Profile - https://bitcointalk.org/index.php?action=profile;u=1355858
Wallet - 0x5Cad90c82D21a65Fe5ad2A9D472018BA0B7025C3
Thank you for attention!
More reviews on my blog @jlove
Subscribe!
What is the full meaning of REMME
Protection of personal and other information from hacking.