September 12, 2017, 2:00 AM GMT+6
North Korean hackers target South Korea’s ethereum exchanges
Crypto-currencies become tool to raise and launder money
North Korea seems, by all accounts, to be venturing up endeavors to secure bitcoin and different digital currencies, which could be utilized to dodge exchange confinements including new authorizes affirmed by the United Nations Security Council.
Programmers from Kim Jong Un's administration are expanding their assaults on digital money trades in South Korea and related locales, as indicated by another report from security scientist FireEye Inc. They additionally ruptured an English-dialect bitcoin news site and gathered bitcoin recover installments from worldwide casualties of the malware WannaCry, as indicated by the specialist.
Kim's clear enthusiasm for digital currencies comes in the midst of rising costs and prominence. Similar components that have driven their prosperity - absence of state control and mystery - would make them valuable raising support and illegal tax avoidance instruments for a man undermining to utilize atomic weapons against the U.S. With fixing assents and use of cryptographic forms of money expanding, security specialists say North Korea's grip of computerized money will just increment.
"We unquestionably observe sanctions being a major lever driving this kind of action," said Luke McNamara, a scientist at FireEye and creator of the new report. "They likely consider it to be a minimal effort answer for get hard money."
The 15-part Security Council on Monday affirmed sanctions went for rebuffing North Korea for its most recent rocket and atomic tests. U.S. authorities said the new measures would cut the nation's material fares by 90 percent, confining its capacity to get hard money.
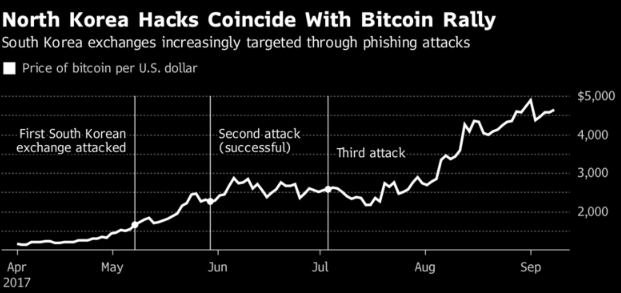
So far this year, FireEye has affirmed assaults on no less than three South Korean trades, incorporating one in May that was fruitful. Around a similar time, nearby media announced that Seoul-based trade Yapizon lost more than 3,800 bitcoins (worth about $15 million at current rates) because of robbery, in spite of the fact that FireEye said there are not clear signs of North Korean association.
North Korea's broadcast communications service didn't react to a messaged ask for remarks. The nation's negotiators and authority media have denied the nation assumed any part in cyberattacks, including the hacking of Sony Pictures Entertainment in 2014.
North Korea works what South Korea accepts is a multitude of programmers extending its concentration from military secret activities to budgetary robbery. The administration's Reconnaissance General Bureau, which specifically reports to Kim Jong Un, handles peacetime digital operations from undercover work to organize interruptions and utilizes an expected 6,000 officers, as indicated by a 2016 report from the International Cyber Policy Center at the Australian Strategic Policy Institute.
In the current round of assaults, South Korea may have turned into an objective not only because of its vicinity to Pyongyang and shared dialect, but since the nation has turned out to be one of the busiest exchanging center points for digital currencies this year. Seoul-based Bithumb is the world's greatest trade for ethereum. In June, it said programmers had stolen client data from a representative's PC, without recognizing the assailants.
"As more cash goes into digital currency trades and more individuals purchase bitcoin and ethereum, trades wind up noticeably bigger focuses for this gathering," said McNamara. He said so far he didn't have prove that Kim Jong Un's administration has focused on digital currency trades outside of South Korea, yet did not discount the likelihood later on.
Other than trades, FireEye said an English-dialect bitcoin news site was broken by North Korea, which would likely enable programmers to distinguish individuals going to the site. It declined to name the site and said it trusts North Korea inclines toward bigger targets like trades than singular proprietors of digital forms of money.
The firm said already it had discovered an association amongst Pyongyang and the WannaCry assault from May and June, which influenced more than 300,000 PCs around the world. McNamara said he likewise observes signs North Korean programmers are getting associated with cryptographic money mining.
Assaults on the South Korean trades were brought out through purported stick phishing assaults, or messaging documents bound with malware to particular targets. FireEye distinguished the malware, known as PEACHPIT, and gave cases of archives it was connected to, including one distributed by Seoul-based Hyundai Research Institute about the condition of bitcoin businesses. Whenever reached, the creator of the report affirmed he composed it in 2014, yet was ignorant that somebody was appropriating an official statement about it this year.
The gathering behind the hacks, which FireEye distinguished as TEMP.Hermit, has become well known out of bitcoin robbery, including a 2015 assault on South Korea's atomic industry. The programmers have additionally been tied by other security firms to a year ago's assault on Samsung Electronics Co's. corporate emissary application and, most noticeably, the rupture of Sony Corp's. film studio, which the FBI faulted for North Korea.
"They're truly fit performers in contrast with other North Korean movement we see," said McNamara. "They've been imaginative by they way they utilize their digital secret activities ability."
The malware utilized as a part of bitcoin hacks is connected to the gathering associated with assaults on the installment frameworks of worldwide banks a year ago, as per FireEye. The FBI is additionally looking at North Korea's connect to the burglary of $81 million through the New York Fed a year ago, Bloomberg Markets announced a month ago.
FireEye said if the programmers needed to change over bitcoin or ethereum into dollars or won, they'd likely first trade them into harder-to-follow cryptographic forms of money like Monero and after that into fiat cash. A comparative system was utilized a month ago to purge the bitcoin wallets identified with WannaCry.
"They could bargain a trade and exchange those bitcoins to different trades somewhere else in Asia or trade them for a more unknown digital currency," said McNamara. "There are assortment of things they could do to money out."