

Dear my steemian friends, in this section I will discuss the pseudocode of the combination of Vernam Cipher and Rivest Cipher 4 algorithms in the encryption and decryption process in Cryptography. Immediately in the following discussion.
3. The Permutation Table Process
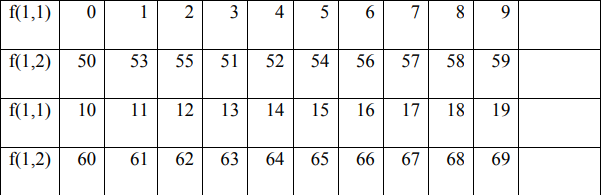
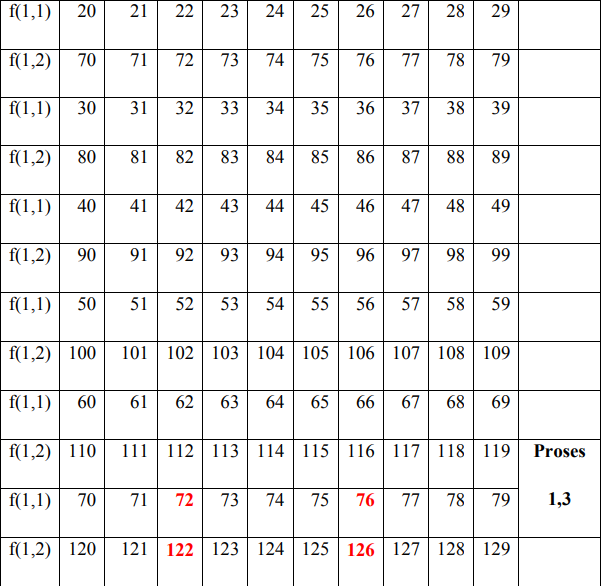
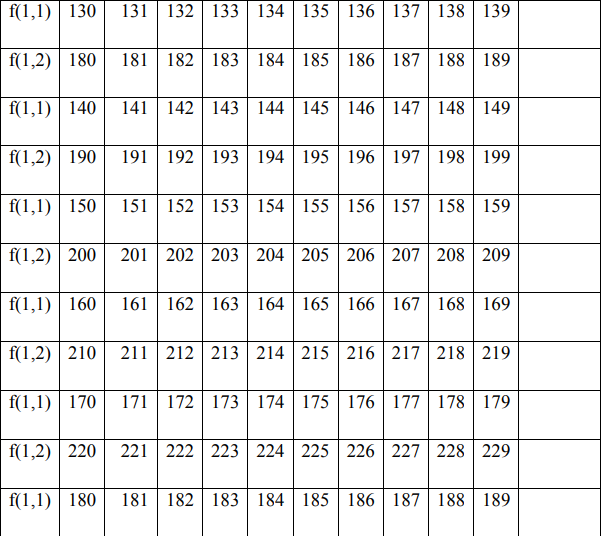
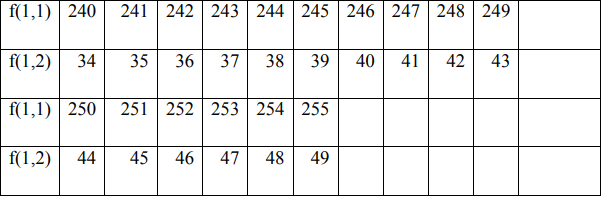
In the encryption process, the permutation process is carried out between f (1) and f (2) by filling in f (1) and f (2) with the value starting from the key value f (1), if the value f (i) has been entered then fill in the next column in the order 0 to 255 without entering the value of the number that has been entered previously.


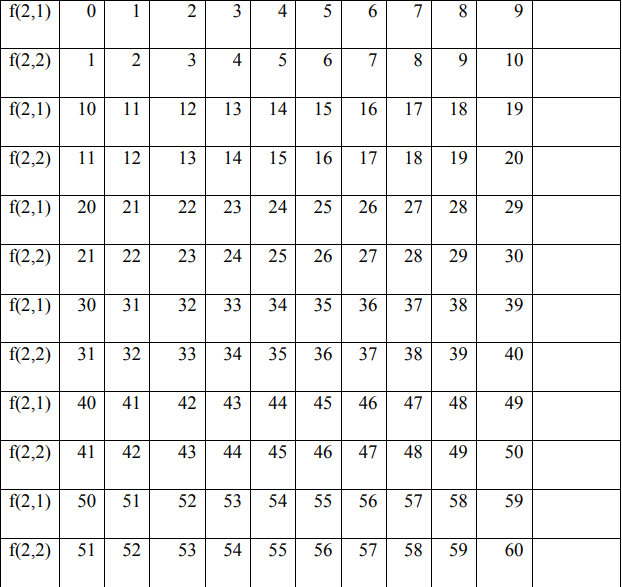
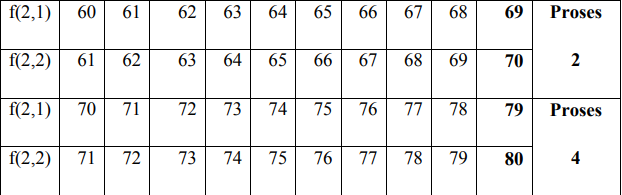
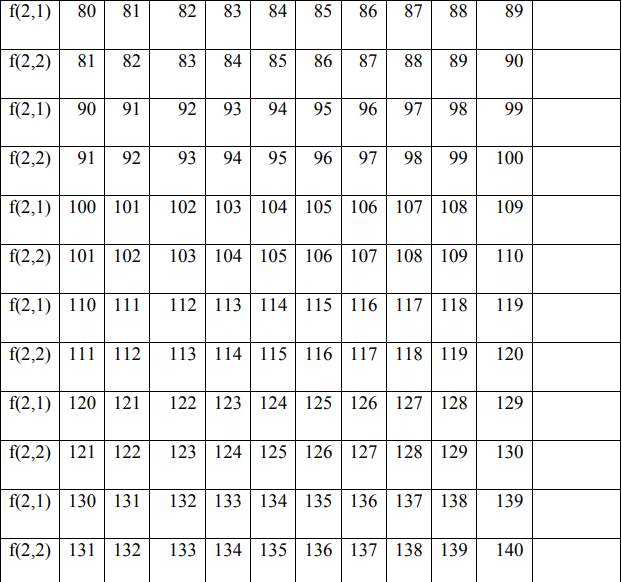
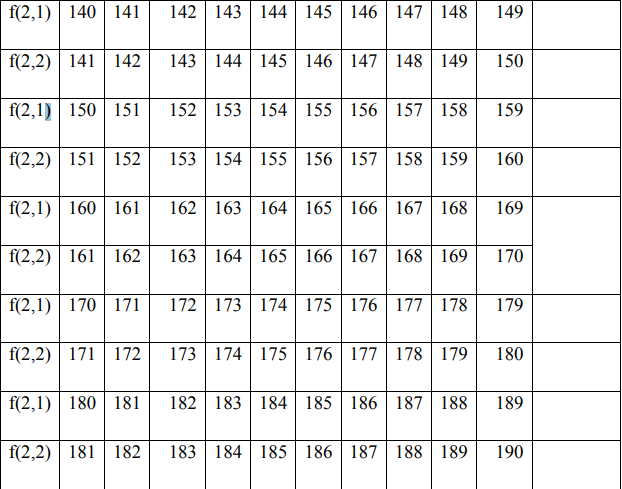
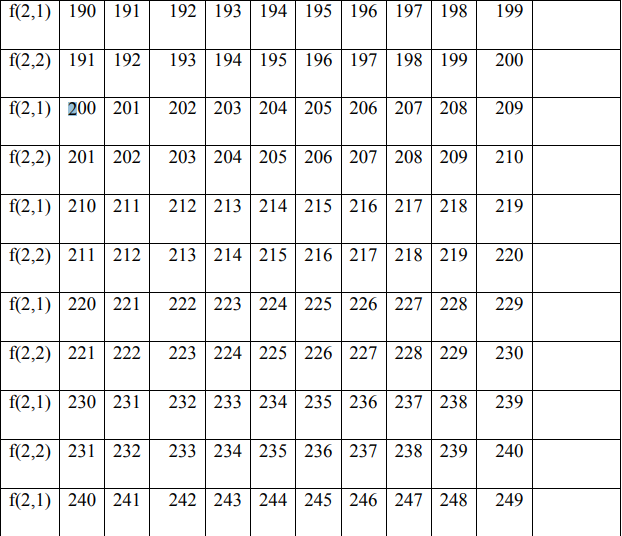
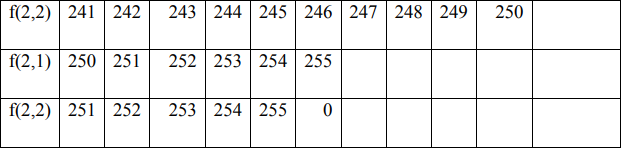
4. Encryption Process
ncryption is done in the following ways:
- Look for the Ascii Code value from Plainttext P(i) numbered f(1,1) if it is found to take the value f(1,2) in accordance with the order of the plainttext as chipertext C(i)
- Next Find the Ascii Code value from Plainttext P(i) with the number f(2.1) if it is found to take the value f(2.2) according to the order of the plainttext as chipertext C(i)
The process is as below :
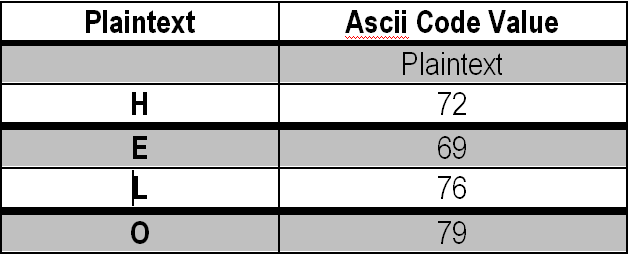
- Find the value 72 from table f (1,1) and take the value f (1,2) as the encryption value f (1,72) = 122
- Find the value 69 from the table f (2.1) and take the value f (2.2) as the encryption value f (1.69) = 70
- Find the value 76 from table f (1,1) and take the value f (1,2) as the encryption value f (1,76) = 126
- Find the value 79 from the table f (2.1) and take the value f (2.2) as the encryption value f (1.79) = 80
Thus, the result of encryption for HELO plaintext is 122.70, 126, 80
5. Decryption Process
The decryption is done in the following way:
- Look for the Ascii Code value from chiperteks C(i) in the row of numbers f(1,2) if it is found to take the value f(1,1) in accordance with the order of the plaintext as chipertext P(i)
- Next Find the Ascii Code value from ciphertext(i) in the row of numbers f(2.2) if it is found to take the value f (2.1) in accordance with the order of the plaintext as chipertext P(i)
The process is as below:
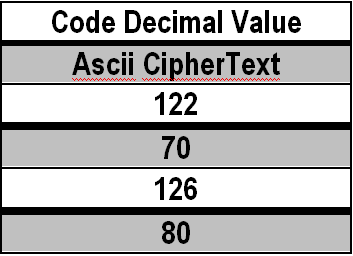
- Find the value 193 from table f(1,2) and take the value f(1,1) as the encryption value f(1,122) = 72
- Look for the value 70 from table f(2.2) and take the value f(2.1) as the encryption value f(1.70) = 69
- Find the value 197 from table f(1,2) and take the value f(1,1) as the encryption value f(1,126) = 76
- Find the value 81 from table f(2.2) and take the value f(2.1) as the encryption value f(1.80) = 79
Thus the decryption results are: 72 (H), 69 (E), 76 (L), 79 (O)
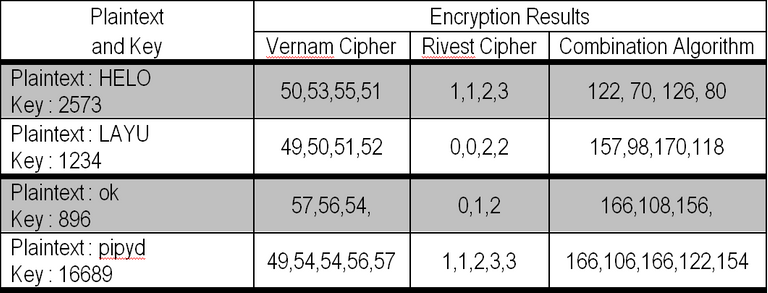
Based on the table above it can be seen that there are differences in encryption results using Vernam, RC4 algorithms and a combination of Vernam and RC4 algorithms.
6. Strength of Algorithms
The strength of the algorithm is described as follows.
- The algorithm will encrypt and decrypt from a sbox f(1) and f(2) based on two different keys.
- Encryption and decryption processes are carried out in f (1) and f(2) interchangeably, so it will be difficult to know where the position of the text will be encrypted and decrypted, because the position of encryption and decryption is determined based on the key of the RC-4 and Vernam Chiper processes.
- If one of the keys is f(1) or f(2), then another key must be found so that the plaintext can be solved, because both f(1) and f(2) must be valid.
- The program will encrypt and decrypt a sbox f1(1) and f(2) based on two different keys.
- In doing encryption and decryption, the combination of vermicelli and RC-4 requires 2 different keys from different processes, and for example if "A" manages to find 1 key in the text cipher then "A" must be able to find another key if it will open the intended ciphertext.
- In doing encryption and decryption, the combination of vermicelli and RC-4 perform randomization of characters that will be taken as chipertext or plaintext according to the existing key and the length of the key and plaintext or ciphertext are 0 to 255 karakkter, thus "A" it will be difficult to find the correct chipertext because of the randomization.
In closing the discussion in this paper, I draw some conclusions. With this conclusion, a comparison can be taken that can ultimately provide improvements in the future.
- Vernam Cipher algorithm has a weakness, if one key is found it will be easy to solve the plaintext or ciphertext because it only uses XOR operations.
- The weakness of Rivest Cipher's cryptographic algorithm is to use only one operation. If the key is found it will be easy to get the plaintext or the ciphertext, because it only uses the XOR operation.
- In the combination of RC-4 and Vernam Cipher will produce a new algorithm that is more difficult to solve, because it uses the method of two operations.
DONE...!!!


Wondering How Steemit Works, Read Steemit FAQ?


Thanks for using eSteem!
Your post has been voted as a part of eSteem encouragement program. Keep up the good work! Install Android, iOS Mobile app or Windows, Mac, Linux Surfer app, if you haven't already!
Learn more: https://esteem.app Join our discord: https://discord.gg/8eHupPq