
It's the most wonderful time of the year! That's right! Time for the third annual Advent of Cyber challenge from my favorite security training site tryhackme.com ! The first day brings us an oldie but a goodie with an IDOR vulnerability. In case you haven't heard of this vulnerability IDOR stands for "Insecure Direct Object Reference" and basically if the vulnerability exists a user can just utilize their web browser's debug mode (usually hitting f12 will bring this interface up!) to pass on a different user_id then their own to the web server. it's quite a simple hack with loads of power to be gained in exploiting it.
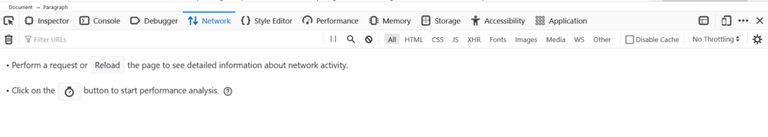
The debug UI in Firefox
In the THM challenge they started easy and had a very old version of this exploit from back in the days when they just put these variables in the URL and hoped for the best that users wouldn't be naughty I guess. Seeing as you should never see this version in the wild I can only assume that people were being naughty!
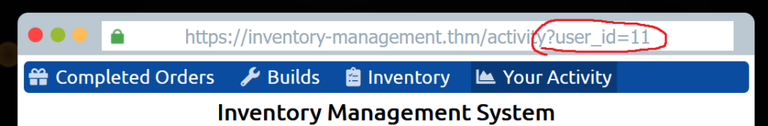
So basically you just twiddle that number up and down to access other users profiles. It's that easy. Yeah I don't know what they were thinking back then either. Sure made life more interesting though!
That's all well and good as the THM event is more geared to newbies, especially in the early days of it, and they give a nice link to a THM room with a more modern version of this vulnerability! So let's CLICK IT !!
Ok, this room has you load up an internal web page in the THM to give you some learning about the vulnerability and also goes into detail about how modern developers try to hide the user values in base64 encoding to try and obfuscate the information coming across the wire. After some more easy twiddling of numbers akin to the advent challenge we get to "A Practical IDOR Example" and this is where it really gets fun!
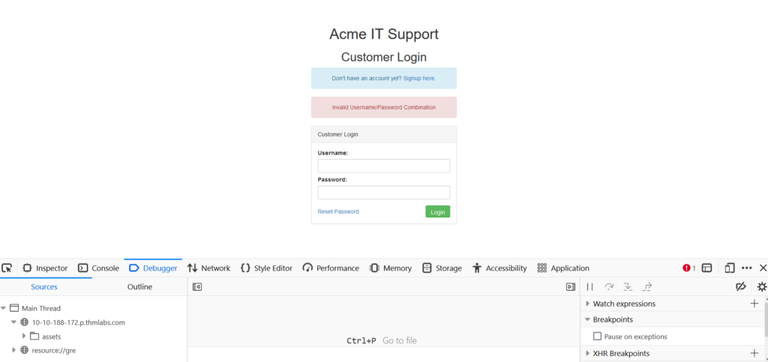
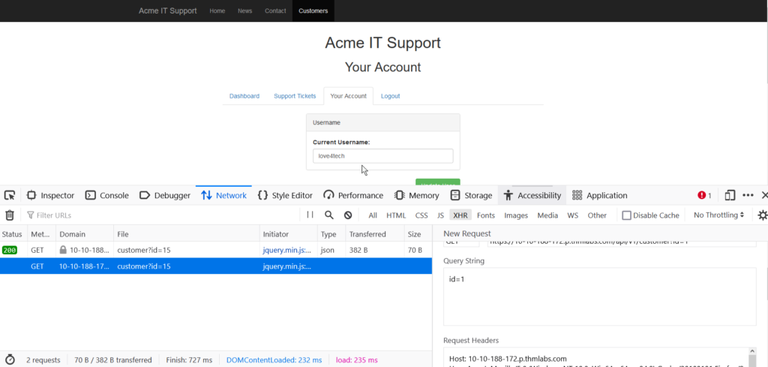
First off you need to make up a login to get access to the site to change our user_id so lets plug some crap in there and get us rolling forward! Once you are logged in make sure you have the debug UI open (f12) and hit the "Your Account" tab on the webpage. That should populate some information in the different tabs in the debug UI and you want to click on the "Network" tab to see the requests sent.
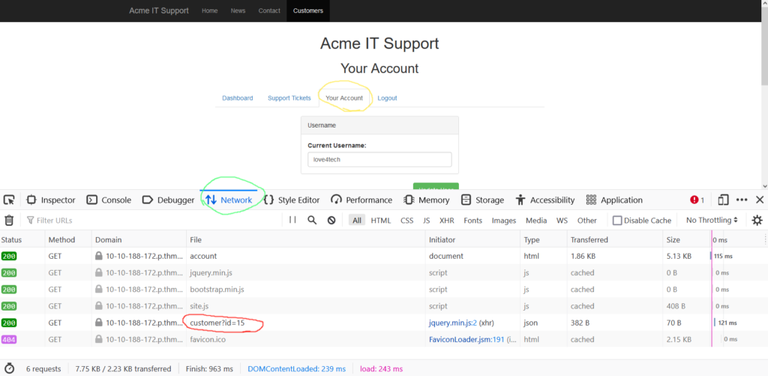
There it is. Plain as day. A user_id this time labeled as "customer_id" what we are going to do with this is just give it a right click on the "File" column and hit "Edit and Resend" and you will get a window to craft your own packet with any id you want! Just change the variable and fire the packet off to the web server!
That's all there is to it! Not only did we check out day 1 of TryHackMe's Advent of Cyber 2021 challenge we even took a bit deeper dive into the vulnerability to see how you would exploit it on a modern website!
Cheers all! Thanks for reading and happy hacking Threat Hunting!
Posted from my blog with Exxp : https://www.love4tech.us/2021/12/02/advent-of-cyber1-sh/
Vector Images by vecteezy.com