
Day 3 was BORING! There I said it. It was just dirbuster. A brute force dictionary style web server directory finder. I didn't even need to launch the machine attached to the room save for at the end to grab the flag. We just gonna move on because day 4 got fun again!
WE GET TO PLAY WITH BURP SUITE!!!!!!!!!!!!!!!!!!!!!!!

Burp Suite or “Burp,” as it is commonly referred, is a proxy-based tool used to evaluate the security of web applications by allowing users to craft, manipulate, and repeat web requests against a target web server.
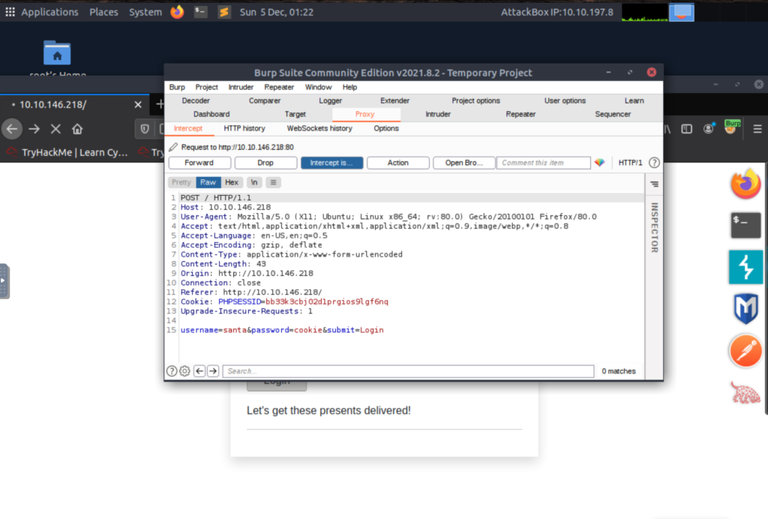
Fire up burp suite and make sure intercept is off for now. then load up the page we want to evaluate. In this case a login page. After turning intercept back on I submitted a known account name with a password guess and caught the POST request coming out on my machine as seen above. easy part is you just right click on that window and select "send to intruder" to send that packet to be manipulated before it's sent on its way across the internet and to our intended target using a dictionary attack and burp's "sniper" mode to fuzz the password variable. As long as your dictionary has that password in it you will get access. This is why everyone needs to use a strong password with multiple character sets and 2FA!
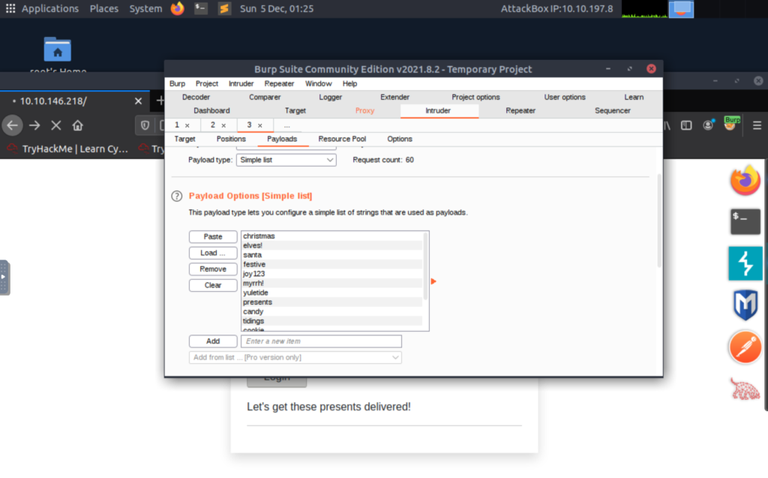
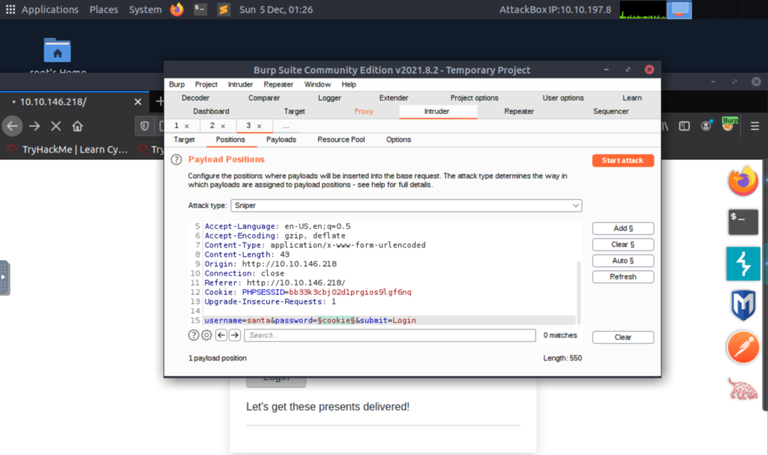

As always there is links to room to learn more but seeing as I already Earned this bad boy badge over here for finishing those rooms previously I decided not to do them again. Day 5 is coming up! Let's see what kind of fun stuff they have in store for us over on tryhackme.com and their Advent of cyber 2021 challenge!
Cheers everyone and happy hacking Bug Hunting!!
Posted from my blog with Exxp : https://www.love4tech.us/2021/12/05/getfuzzy-sh/
Vector Images by vecteezy.com