
Protecting Networks
Network attacks are the most common technical threat to a network. Even if we keep our data safe on our computer, it may still be possible for an attacker to get ahold of our data while it is traveling across the network or the internet. To help keep our data safe it is important to understand the risks of sending data, and what we can do to keep it safe while it is traveling from one computer to another.
A quick introduction to networking
You must understand how communication works online for you to understand cybersecurity. I’ll give you a quick crash course for novice nerds in that:
When you play around in the console of websites, surf around on pages or do things “online”, information is being translated to binary, then sent away to other servers. You usually never talk directly to a medium and always hop between destinations. When you have reached the destination that you are requesting, information such as your destination, basic information about your computer, fingerprints, and identification of who is and other metadata is being delivered. The receiver uses this information to validate you for who you are, as well as authenticating information packages that are customized for you, and more. This type of information is typically encrypted, but not always.
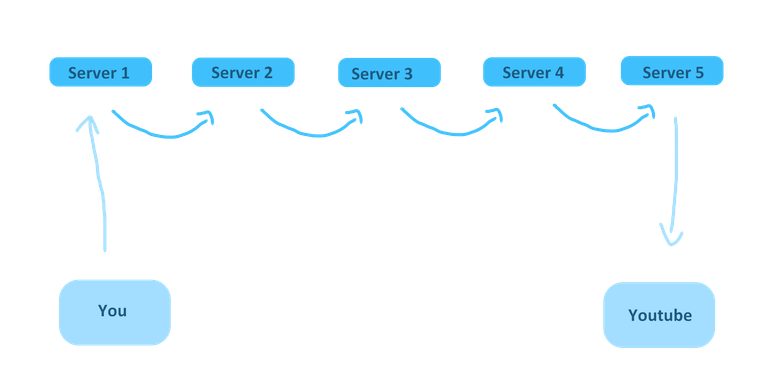
Like I said earlier, we never have direct contact, but hop between servers. Now Image all this information being redirected to over 5, 10, 20, even 30 different mediums that are delivering these packages. You would imagine how many other threats that are facing you just after that delivery as well. In this text, I will talk some sense into beginners and novice nerds (yes you) about online security and how to protect your network as well as protecting yourself from online threats.
Encryption and connection
Below I have broken down some basic topics to always have in mind when you are surfing the web. These are easy to follow and should be respected to maintain a protected network whenever you connected and send information.
• Encrypt and password-protect data you are sending
When we are sending data over a public network, we do not want people to be able to see what we are sending. Encrypting the data we are sending can be done with https and with a virtual private network. Sometimes we want to encrypt sensitive data so that it cannot be opened unless the person reading it enters a password
• Encryption and passwords with emails and files
When sending emails with secure attachments, do not assume that the other person's email has not to be compromised. Password protect the attachment so it cannot be read without the other person entering a password.
This goes the same for data we email to ourselves or even data that we store on the network in public folders. Check with your security team on who has access to certain network folders and ask about any encryption or password protection solution for critical files.
• Make sure that you are sending data to secure websites
When we are about to log in to a website before we type in our password we want to check to see if the website is https. This means that the only computers that can see what we are typing into the login are our computer, and the website we are logging into. Logging into a page that is the only HTTP, and does not have a lock, is very risky in a public space.
• Always look for the lock
Take a look at many webpage addresses. In the address bar, you may see “http” or “https”.
If you see that “http” then any information you are sending to that page can be read by anyone else on your network. Passwords, comments, searches and any other information you type to these pages can be seen.

(I made this picture purely out of rectangles and circles, so please forgive the bad quality)
Pages with “https” protect the data you send to them so it cannot be read by others. It keeps other people from seeing the information you send by creating a secure connection between your computer and the website. This should always be used when purchasing things online.
But use caution with https certificates!
In some cases, even if the website you see has “https” someone may be looking at your data. This can happen most often when you are connecting to the internet in public places where your computer is trusting a connection that may not be trustworthy at all. It is necessary to take special care when navigating the internet on these networks to prevent personal or private data from being seen, and our computers from being accessed.
• Update devices before using public networks
Even when we have encrypted our data and are logging into secure https websites, we still want to use caution when we are using a public network. Before connecting to these networks, we want our computer security up to date (such as updating firmware and software). Hackers can get into systems that are old and have security holes in them. If you give your computer the newest updates, you will automatically be equipped with security patches and ready to stand against attackers.
• Choosing how to connect to the network
When we connect to a new internet connection, we are often given the option to set this network type as "Public", "Work", or "Home". Our computer makes it very easy for us to tell which network type we should select when we connect to a "Public" internet connection.
Making sure that we select the "Public" network connection type when we connect to a public internet connection, helps our computer decide to use more strict security and not to trust other computers on that same public network.
• VPN options
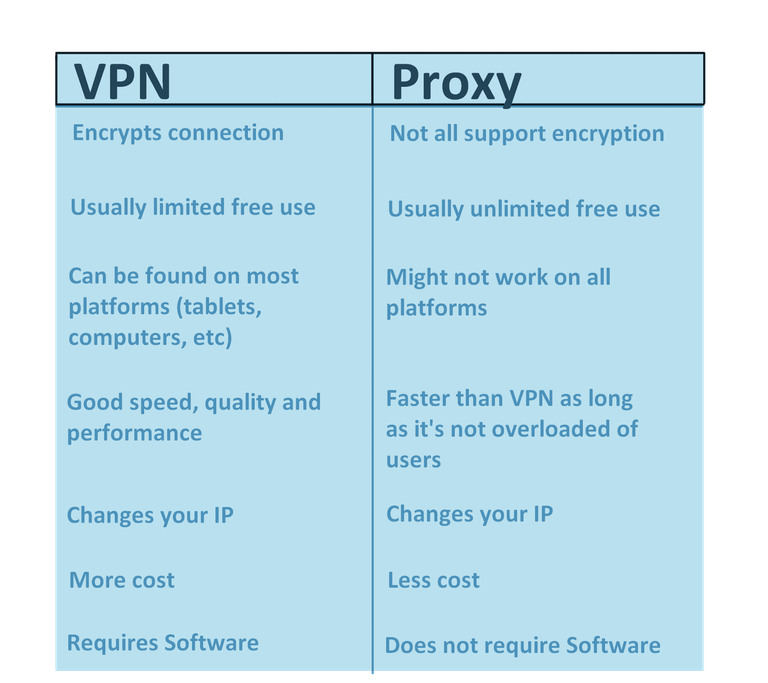
Virtual Private Networks (VPN) help us to keep our information safe even when we are connected to a public internet connection. If our company laptop has special VPN software installed on it that allows us to connect to our work network, we always want to enable this whenever we connect to an internet connection. If you’ve also heard of proxies and know that these can help hide your location, here's a quick template for the difference between a proxy and a VPN:
• Wi-Fi vs Cable
Whenever we are in a situation where we can choose between connecting to the internet through a cable connection or a Wi-Fi connection, always choose the cable connection. Cable internet connections are much more secure and help prevent many of the risks associated with Wi-Fi connections.
• Sending Info
Even after considering all the other security measures we have discussed, the best practice when connecting to a public internet connection is to avoid sending extremely sensitive information from our computer. Sometimes we may need to do some work while at the coffee shop; however, if it is possible to delay sending confidential information until we are connected to a more secure internet connection, then we are successfully adding another measure of security.
Downloading and bringing other equipment
• Protect physical access to your system (log out, lock)
Don’t trust everyone around you too easily and always make sure you lock your computer. Unless you want people to have unauthorized admin access to all of your systems that is. Win + L
• Don't connect the device to the network
Without knowledge of the security team, you can never know what is allowed and what is safe. Always tell your security team that you’re connecting a new device or system and wait for permission. If you connect a foreign system to the network and it is infected, you may expose the entire network for vulnerabilities and breaches (a home laptop that might be infected for instance).
• Don't bring media to work from home without approval (USB, CDs, hard disks, drives etc)
The same goes here. Without knowledge of the security team, you can never know what is allowed and what is safe. Always tell your security team that you're connecting a new device or system and wait for permission. USBs, CDs, Hard drives or disks may also be infected and can locally destroy your network or even infect larger areas.
• Scan files before download
Never trust the files you download and believe in any green colors you see. Malware can easily cling onto files and, commonly, the file you download is not the original file in the first place. Always scan the file before installing or even downloading it to make sure it’s clean and proper. It’s also possible to check the hash of the file if you are more knowledgeable. (Read more about hashing in the article What is Cryptography – coming soon!)
• Download from trusted sites
Always download from legit websites with legitimate certificates of approval and security. These can be checked in settings or by snooping around to check the validity of the website. (Read more about this in the article End User Awareness 6 Protecting Against Websites – coming soon!)
👍
~Smartsteem Curation Team