
Protecting your Identity
Identity theft online is more common than you would believe. Take for instance a celebrity’s Instagram account, which most likely has been copied over a dozen times. Identities online are sometimes too underestimated and are therefore one of the biggest threats of human vulnerabilities. Learn the top dangers of identity attacks and how to protect against it.
Personally Identifiable Information (PII) – What is this?
Personally identifiable information (PII) is information that can be used to allow someone to locate and contact individuals. This can be things such as;
• Full name, Mother's Maiden Name
• Social Security Number
• Address, Phone number
• Vehicle Registration Number
• Biometrics
• other identifying characteristics
• Social Media:
When you share on social media you are making your private information public. That information can provide information to assist attackers:
• know our geographic location
• obtain information which may be our recovery answers
• Inadvertently reveal sensitive corporate or government information

What to do?
In order to secure yourself and even your family and friends, it’s important to not share too many credentials and private information. If you’re more paranoid than others, even valuate getting a fake ID in the real world as much as virtually. Below are the most efficient countermeasures for attackers to steal or utilize your identity for malicious purposes:
Credential information and PII
• Do not leave PII unprotected
Don’t let your personally identifiable information open to anyone. Always make sure to lock your computer when you step away, even if only for a few moments. When leaving for the day, do not leave sensitive documents on your desk or out in the open. Be sure to lock them away in a secure cabinet or the proper location. Do not send sensitive information through insecure means (a file hosting website, unencrypted USB, public email, etc. Read more about network security in the article End User Awareness 2 Protecting the Network).
• Secure social security number
Don't carry it around or write it down. If you need it written down, use your passport as a reminder and only that. Social Security Numbers are vulnerable to many high authority actions and should never be revealed to others—only remember it in your head.
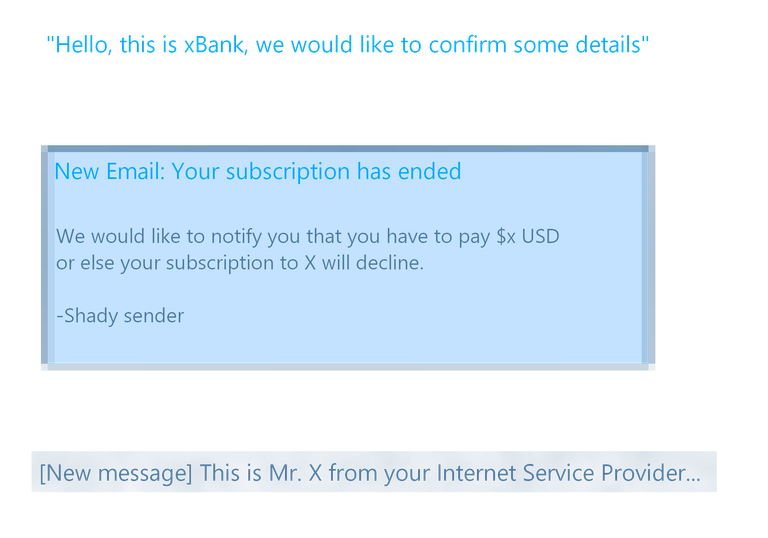
• Don't respond to requests by phone, mail or online
If you ever get a shady email or scam phone calls, hang up immediately. You never know what might be going on on the other side of the screen, and should, therefore, dismiss any action from a stranger or foreign subject that seem not legitimate.
• Watch out for shoulder surfers & ATM skimmers
When doing coded access to buildings or when using ATMs for instance. You never know who might be watching right over your shoulder and recording your pin codes or passwords. Always keep an eye out for people who are standing a bit too close than they should. Don’t be afraid to tell people to back off.
People sometimes even install ATM skimmers. These devices lay on the card insertion itself on the ATM and record your credentials on the card, steals and send it to the master maker. These are difficult to spot but can be checked by grabbing the card insertion plastic cover and shaking it moderately to see if there’s an extra layer that loosens.

• Don't store personal information or passwords
On notes or written down anywhere. Anything stored can be retrieved, and sometimes not always by the person who made them. Make a system of your own credential information in your head and remember it clearly. If needed to store personal information, make sure to encrypt it. Here are some top free software tools:
• LastPass
• BitLocker
• VeraCrypt
• FileVault 2
• DiskCryptor
• 7-Zip
• AxCrypt
• HTTPS Everywhere
• Shred receipts, credit offers, account statements, and expired cards.
Review your receipts. Promptly compare receipts with account statements. Watch out for unauthorized transactions and non-valid banks or companies. Always make sure you shred garbage and “delete” any information that can be retrieved from the trash and re-assembled.
Virtual Security and policies
• Install firewalls and virus-detection software
A virus is prone to attacking any saved credentials we have on our computer and should, therefore, be carefully watched out for. Install firewalls to make sure your network is safe from any malware that may come and always run malware scans frequently.
• Send private information properly
Financial data are some of the biggest targets for online attacks. Always make sure you surf on https or other encrypted protocols. There are many ways this can be stolen:
• A virus to record the keys we type
• impersonating bank websites
• scam emails
• websites which steal payment info
• websites which record the keys we are typing into other open pages
• Authenticate according to policy
Before giving out any information verify that the person you are communicating with is who they say they are. Always verify before sending critical information, not only over the phone but also through email. The person on the other end may have had their email account compromised. Be suspicious of requests that seem out of character and if necessary, verify the other person's identity.
• Defer questions to the authority
If in doubt, get guidance from another authority. Check with any manager or security team manager before releasing any information you are not sure about. The security team can help you with understanding how to protect PII that is saved on the network or needs to be sent across the internet.
• Follow company policy
Established policies and protocols always are the first check when we are unsure on how to handle requests for Personally Identifiable Information. Check and see if policy dictates what information can be given out, how to authenticate individuals it can be given to, and the secure way to send the information. If this documentation is unavailable, check with an authority. Defer Questions to Authority