
Protecting Against Social Engineering
Social Engineering may present the greatest threat to confidentiality today, which is why it’s important to understand not all threats are technical attacks. Simply by manipulating people, attackers can be more successful with less effort.
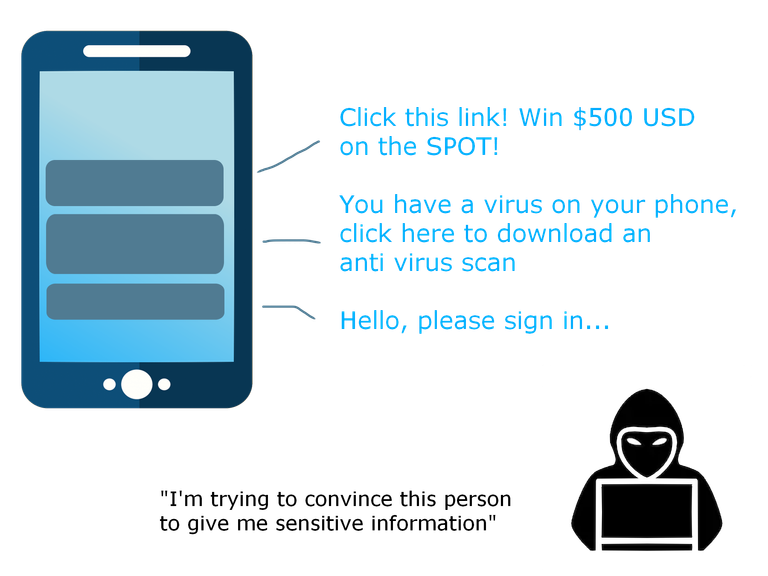
Social Engineering exploits the flaws in people's actions, habits, customs, and laziness; mass Emails, calls, letters or messages with the intent to deceive you. Most typically used to get money, information or have you install or open a malicious file. You have most likely been out for a SE attack but was never aware of it. Beneath are the top topics within Social Engineering attacks you may come out for and what they do:
• Phishing
The fraudulent practice of sending emails to induce people to reveal personal information or send money. The attacker seeks to obtain personal information such as names, addresses, phone numbers, and Social Security Numbers.
Often the information is obtained via email. The email appears to come from legit business/person, contains malicious attachments, or contains a link to a fraudulent web page that appears legit in most cases.
| Smishing | Vishing | Spear Phishing | Whaling |
|---|---|---|---|
| “SMS phishing” Getting texts with links to fool you to reveal info or download malware. This could be a fake bank trying to get you to update your information or other credentials. | “Voice phishing” Using a telephone to scam someone. Most commonly tech support scams that are done over a call. Ever heard of fake banks that try to get you to “fix” your account or “repay” some loans? | Spear Phishing is an attack directed after a specific individual, organization or business. This is an attack that goes after “regular” phishing information. | Whaling is an attack directed against highly placed individuals such as presidents, CEOs or CFOs. These have the intent to steal more special sensitive information. |
Be aware:
Hackers can recreate a legit-sounding copy of an institutions IVR system, which will prompt the victim to verify information using fraudulent IVR. This is like crafting questions to make it professional and believable, looking like they’re someone else when they’re not.
Physical practices
| Baiting | Quid Pro Quo |
|---|---|
| Similar to phishing, but this time the user is promised some type of good. This might be a dropped USB flash drive with an intriguing label in a highly trafficked area that is left in the open with the intent of someone finding it and using it. The victim will proceed by inserting the driver out of curiosity and is infected with malware via autorun or autoplay. This can also be a thumb driver, CDs, and other devices that automatically run programs if plugged in. Mostly used to gain access to your computer and eventually the whole network. | Similar to baiting, but is a promise of service. This could be a cold call as technical support in hopes of reaching a person with a significant problem. The victim then discloses private information and or install malware that is supposed to “fix” the significant problem. The tech support could also ask for access to computers which will also install malware on the machine. |
| Shoulder Surfing | Dumpster Diving |
|---|---|
| Looking over someone's shoulder to gain information. Noticing which type of software they use, what they're doing, passwords, information, etc. This is often an identity theft technique and is most commonly found at airports, bars, restaurants, and grocery stores. Eavesdropping is also a high risk in social places like these and should be looked out for since it grabs valuable real-time information. | Jumping into the dumpster to find shredded papers, information saved on hard disks or passwords written on papers. Often used to find documents that can be credential for figuring out a company or individual information. It can be manipulated by making employees think it's someone from the company. Fun fact: this is legal in the US. (so be aware) |
• Reverse Social Engineering
Instead of the attacker going to you, the attacker wants you to contact them. Such as tech support scams.
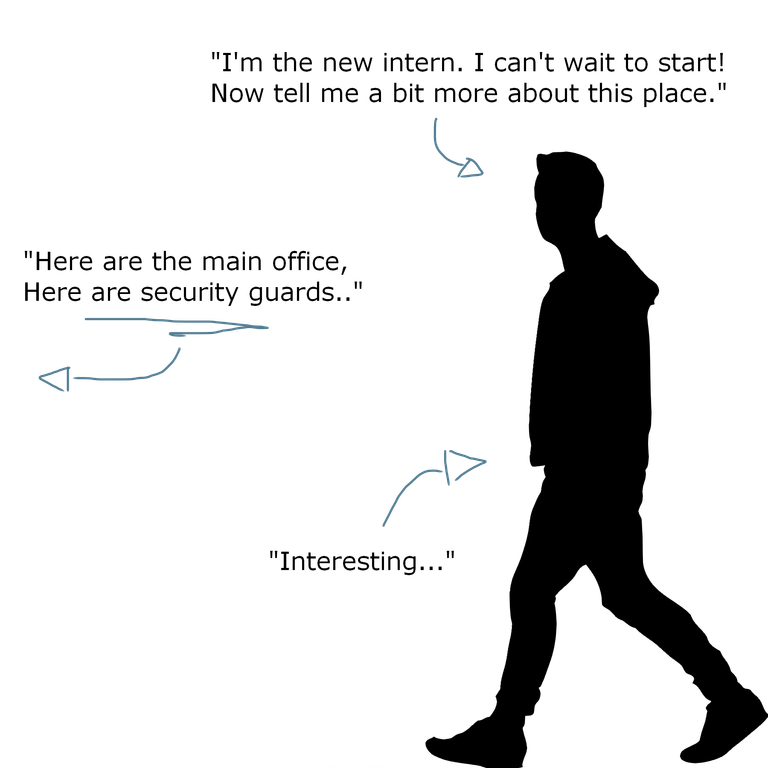
• Tailgating
An attacker may impersonate someone and use a fake badge to get into the building by blending in. He may follow an authorized person through the access door. Most commonly looks legitimate and thus is allowed to walk behind a person with legitimate access to enter a restricted area. If the attacker does not have a fake badge or a badge at all, this is called PIGGYBACKING. (just following someone who props open a door)
• Social Media
When you share on social media you are making your private information public. Social engineering is feeding off of this information, which is why it’s important to shut off and close your account down to strangers. If not, that information can provide information to assist attackers:
• know our geographic location
• obtain information which may be our recovery answers
• inadvertently reveal sensitive corporate or government information
(read more about this in End User Awareness 3 – Protecting Identities)
• Pretexting
This involves building a sense of trust of the victim, such as posing as an IT auditor to manipulate people at the company's front door to let them it. It could also be someone contacting you to confirm your identity with certain pieces of information.
Pretexting is at most cases an attacker pretending to be someone that they're not with pieces of information (or making the situation innocent and likable) that seem trustworthy.
It could be done in person, over phone, email or mail and is used to get information or gain access.
• flattery, assuming authority, appearing busy/in a hurry, threatening repercussions, disguises
• claiming to be from a service company/presenting claimed credentials/declaring a sense of urgency
What to do
• Delay real-life information
Some information, such as when you are leaving the house for vacation, should be shared after you arrive back home. While it may be exciting and difficult not to post pictures while you are gone. Instead, take and save the pictures and upload them once you return home.
If you are away on business or deployment, pictures taken during events should not be shared online while away (or sometimes not at all). This is especially true of pictures taken of military installations or troop movements which can be detrimental to national security.
• Know your secret question risks
What type of security questions do you have set up for your password recovery?
- Mothers Maiden Name?
- Make and Model of Your First Car?
- Name of Your First Pet?
- The year you met Your Spouse?
Could someone determine the answer to these questions by doing a bit of snooping on social media? Know the risks associated with putting your information online and consider this when setting up your security questions.
• Privacy settings/matter
Do not accept friend requests from people you do not actually know
Social media accounts (such as Facebook and Twitter) are often targets for attackers because they provide a new "identity" for them to attack others. Someone who can exploit our social media account has access to contacting our friends to ask for their personal information by impersonating you.
Don't leave valuable information on your desk either. Always keep your personal things with you, non-reachable for others.

Remember to install anti-malware and scan your computer regularly. If you can, do your best to know your system and remember how things should be and what it should look like. This way you will know when something is up and suspicion is required.
• Variate and secure passwords
Be sure that when setting up your social media passwords, you set a password which is secure, only used for that one website, and is changed regularly.

• Require multifactor authentication
Always require more layers of security before getting access. It’s important that an attacker can’t get a hold of your password and email and impersonate you with your user account. Always set up separate security measures.

• Trust no one and follow the company policy
This can be interpreted in many ways. I’m not saying to not trust your grandmother, but choose wisely who you want to give out your own information or access. Don’t be too nice and let people scan their own card when entering a building. Don’t ever succumb to pressure, no matter how stressful the other person may be. Take your time and take things calmly.
Always follow company policy. Remember that it is there for a reason and trust the people who are in their own field of expertise. If you have questions or are in suspicion of something, always call your security team. Remember that if it sounds too good to be true, it probably is. Always be suspicious, be aware of the threats and remember what to do if you encounter them.
Congratulations @genezyz! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Vote for @Steemitboard as a witness to get one more award and increased upvotes!