
Hi steemians !
I have presented you the forensic Volatility tool in my previous posts (Volatility #1 and Volatility #2), today I will introduce you "Rekall" which is almost similar to Volatility since this is a fork of it. The use is the same but Rekall enjoys improvements, especially at the level of some plugins, which I find, work better with Rekall. This is the case with the Mimikatz plugin that we will use to extract user passwords from a memory dump. Mimikatz is a tool that allows to extract passwords, hashs or kerberos tickets from memory, it has become an essential tool for pentesters.
For the demonstration I use, as for Volatility, the files of challenges of the site Root-Me !
1. Install Rekall on Kali
Since Volatility is already installed on Kali Linux, creating a virtual environment for a clean installation of Rekall is recommended.
1.1. Creating virtual environment
$ virtualenv /tmp/RekallEnv
New python executable in /tmp/RekallEnv/bin/python
Installing setuptools, pip...done.
$ source /tmp/RekallEnv/bin/activate
1.2. Rekall installation
$ pip install --upgrade setuptools pip wheel
$ git clone https://github.com/google/rekall.git rekall
$ pip install --editable rekall/rekall-lib
$ pip install --editable rekall/rekall-core
$ pip install --editable rekall/rekall-agent
$ pip install --editable rekall
2. Rekall : Windows password extraction
Unlike Volatility, it is not necessary to identify the source of the dump memory for Rekall to use the plugins correctly. We can directly switch to the extraction of passwords and masterkey with just a simple command:
$ rekall -f dump.img mimikatz
A few seconds later, the result is displayed:
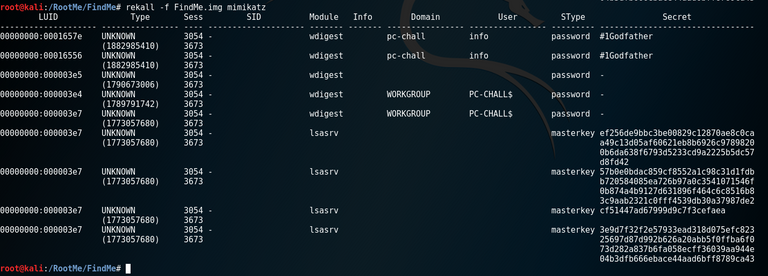
Password for account "info" is "#1Godfather"
The Rekall tool is really simple to install and to take in hand, it is of a formidable efficiency, which makes a strong ally during Wargame and CTF !
cool
Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.Congratulations! This post has been upvoted from the communal account, @minnowsupport, by Nybble from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, and someguy123. The goal is to help Steemit grow by supporting Minnows and creating a social network. Please find us in the
If you like what we're doing please upvote this comment so we can continue to build the community account that's supporting all members.