We would like to report that we have found a minor vulnerability in our off-line voting tool. The code was audited and forked by the community many times, but this little bugger slipped everyone's attention until we found it ourselves. It is related to the autofill functionality of browsers, which when enabled, will store your private key in the browser autofill cache on the computer used to generate the transaction. This itself does not expose your key in any way, but technically can be exploited by a third party with access to your particular computer.
For those of you who have already used our tool to vote, and have the autofill function enabled, please manually clear the autofill cache of the browser you used to generate the transaction. This will erase any traces of this sensitive information.
Here's is how:
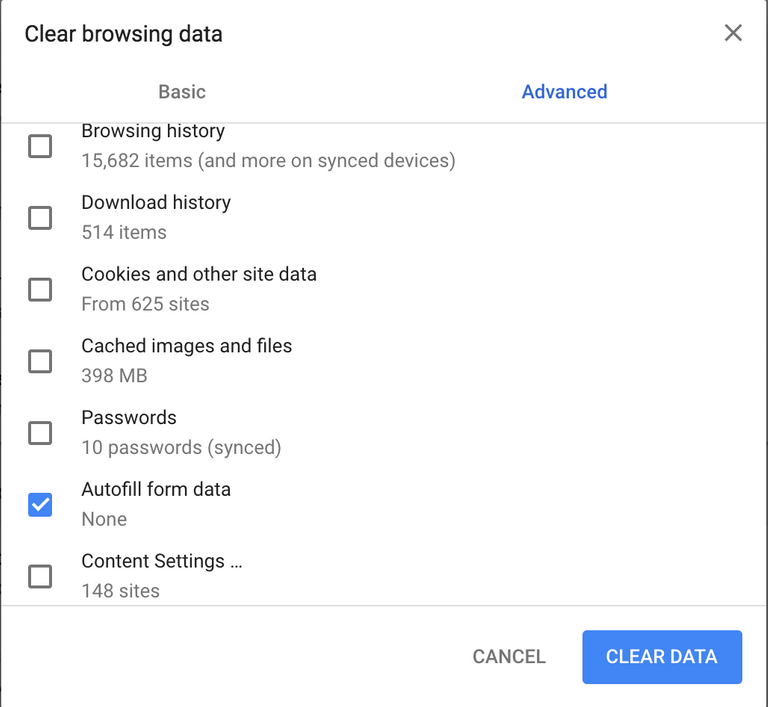
For Google Chrome for Windows press Shift+Ctrl+Del. For Google Chrome for OSX press Shift+Command+Delete
from the below window select Auto Fill Form Data and press Clear Data.
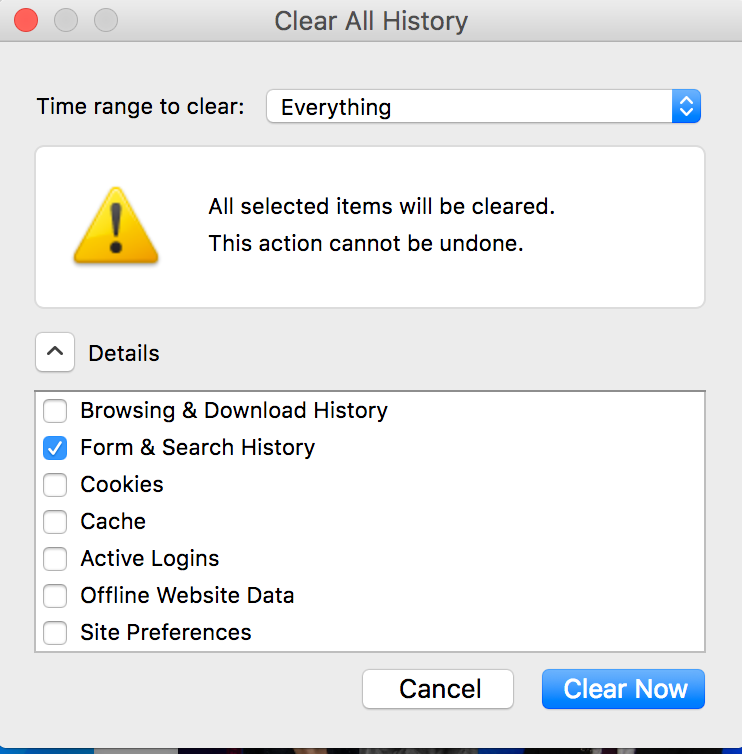
For Firefox for Windows press Shift+Ctrl+Del. For Firefox for OSX press Shift+Command+Delete
From the below window select Form & Search History and press Clear Now.
This vulnerability does not expose the user to any attack, as long as their computer does not fall into the hands of a malicious actor. Still we feel it is urgent to inform the community of such an attack vector, as unlikely as it may seem. As of this morning, this vulnerability has been patched and for the new voters, the private keys will no longer reside in your autofill browser’s cache, regardless of the browser settings. Also, the very minor risk applies only to these browser instances where the auto-fill function was enabled by default, which is a very bad idea from a security standpoint.
We wish to apologise for any inconvenience this might cause and hope that our prompt response will be sufficient to address this without any fallout. Please share this information with whomever you think could be affected.