The Black Hat group managed to exploit three wallets, before the White Hat group intervened and swept up all other affected wallets.
A basic principle of Blockchains is that all actions are traceable. So, can we drill into the blockchain and inspect the messages sent by the attacker? The answer is YES, we can.

---
The havoc was wreaked by two simple messages, sent in sequence:
- initWallet => resets the wallet’s owner address.
- execute => it executes the ETH transfer, thus stealing the funds.
The illustrations belong to the aeternity wallet, but the other attacks (including the White Hat’s) rely on the same logic.
The initWallet message
The initWallet function was only supposed to be invoked at wallet initialisation (read more in my previous post). It sets the address of the owner of the wallet, thus giving it full control over its assets.But it was wrongly made publicly visible, hence allowing calls from the outside at any time. That’s the vulnerability the attacker used.
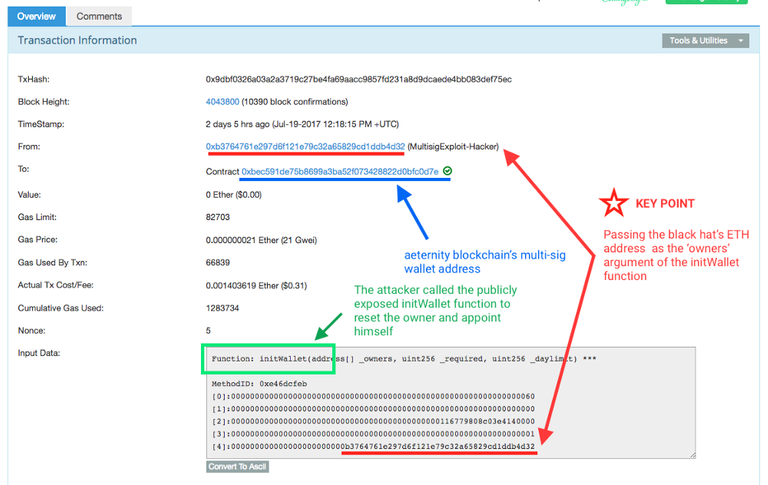
https://etherscan.io/tx/0x9dbf0326a03a2a3719c27be4fa69aacc9857fd231a8d9dcaede4bb083def75ec
Explanation: the message wraps a function call to initWallet passing in the hacker’s ETH address as the new owner. Notice how the address passed in as an argument matches the address from where the message originates, i.e. the Black Hat.
This call only cost the attacker 66839 Gwei, i.e. $0.31.
At the moment I took the snapshot, the block that includes this transaction had over 10,000 confirmations.So it’s pretty irreversible and it gets harder and harder to reverse every ~18–20 seconds (ETH average block mining time), even if a hard fork is organised.
EDIT: As Nick Johnson pointed on Reddit, a hard fork could return the funds without requiring a full reversal of the subsequent chain, albeit being impractical and highly complex due to the fact that funds have been moved further, contracts have committed suicide, etc.
The execute message
Now that the attacker has appointed himself as the new owner of the aeternity wallet, they can use their private key to sign an outgoing transfer for the balance of the account (82,189 ETH).
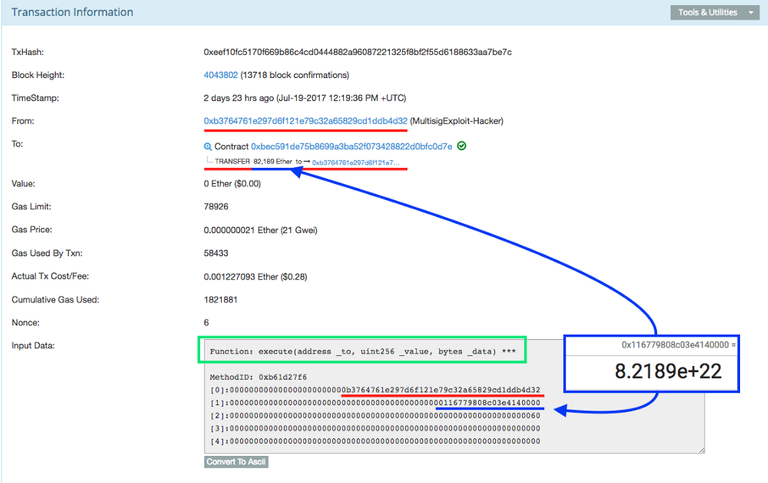
https://etherscan.io/tx/0xeef10fc5170f669b86c4cd0444882a96087221325f8bf2f55d6188633aa7be7c
Explanation: as you can see, this message wraps a call to the executefunction, passing in its own address as the beneficiary and the amount to transfer (82,189 ETH).
The call data is encoded in hex. The amount is expressed in Wei, once converted to decimal it matches the internal transfer that the contract ended up making, as you can see.The attacker paid the equivalent to $0.28 for transferring an amount equivalent to $18M (as per today’s ETH price).
Note: The attacker could have chosen any other address that they controlled to send the funds to, but they chose the same address designated as the new owner.
The White Hat intervention
These two messages are the same messages the White Hat group employed to acquire control of all other affected wallets . Always in groups of two:

https://etherscan.io/txs?a=0x1dba1131000664b884a1ba238464159892252d3a
If you enjoyed this article, please upvote it on Medium, and share it on Twitter, LinkedIn, etc.
I’m also open to opportunities in the Blockchain space; find me on LinkedIn.
Feel free to follow me on Twitter for more stuff like this: https://twitter.com/raulvk.
Thanks for sharing
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://medium.com/@raulk/dissecting-the-two-malicious-ethereum-messages-that-cost-30m-but-couldve-cost-100m-155e023a9500
how does this work ? a bot on a tekst website ?
Looks like a bot to me
Congratulations @raulk! You have received a personal award!
Click on the badge to view your Board of Honor.
Congratulations @raulk! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!