
Photocollage by KD Neeley
The Open Protocol
ID, Bevy, Passenger, and Genesis
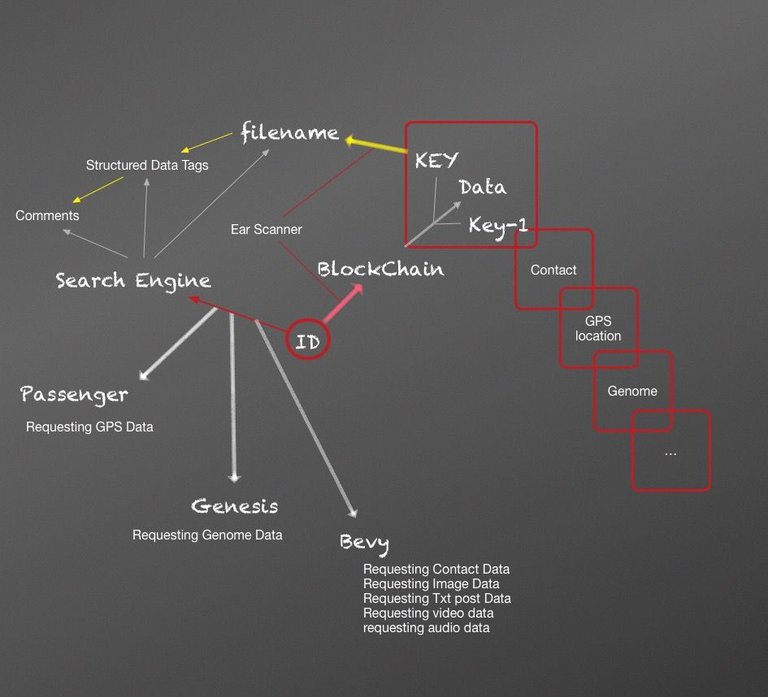
Sitting down at her MacBook and adjusting her ear scanner, Sara waited a moment as it buzzed. A laser lit up and crawled across the unique features of her canal.
"Authorizing..."
She was in. It was the first time she installed ID, and the first set of data she wanted to introduce into her identity blockchain was her own genome sequence. The class had been simple enough, and she understood the interface.
File>New Block
She selected the dataset containing her genome and hit "Upload." Now it was time to wait. The green progress bar began to fill, "4%...5%..." She could install Genesis while she waited. She launched the disk image and pulled the .dmg over the Applications icon and dropped it. The upload completed and it was time to launch Genome. It would be the first application granted access to Sara's identity chain.
She opened Genome and waited as it loaded the list of clients, "NIH, GenomeConnect, Trials Gateway...." the list went on. She could authorize any number of these clients to access the data in her genome sequence for their research. Selecting one of the clients brought up a description of the research project. The first one she selected described how her genome could be used to search for cures to various cancers.
"Approve"
Genome accessed ID and requested permission to read the specific file types in her blockchain containing her genome data. Genome told ID which file types it was looking for and ID brought up the single file she had uploaded onto her blockchain. Sara clicked on it and chose "Authorize". She waited again as her ear scanner lit up and ensured her identity. It was done. Now her genome would be used in cancer research.
Passenger is the next application Sara wants to try. There's a party at Kate's house tonight, and she can use Passenger to catch a ride to it. The first thing to do is install the mobile ID app on her phone. She installs it. She disconnects the Bluetooth to her ear scanner and connects the ear scanner to her phone. Sara touches the ID fingerprint icon, and it launches. The ID app requests her approval to access her ear scanner, and she grants it. That little buzz again as the light crawls across her canal. Done. She immediately has access to the files she's uploaded to her identity chain. In the ID interface she selects File > Upload > Location. She quickly authorizes the ear scan again, and her GPS location is written to her identity chain. Now she has GPS data she can use with the Passenger application.
Sara launches Passenger, and it pulls up a map showing her current location. She selects the icon for payment types and selects the various ways she can pay drivers for transport: Ether, Bitcoin, Dollars...the list goes on. She hasn't set up an Ether wallet yet, so she selects Dollars as her preferred method of payment. Her settings are saved. She looks at her profile and sees that she has no Passenger rating because she's never used Passenger before, in small letters below the empty stars it reads "new rider."
There's an icon with the ID fingerprint, she selects it, "Passenger would like to access your location files."
"Authorize," says Sara. Her ear scanner vibrates a little as it registers her canal.
"Syncing..." After ID syncs with Passenger, she's back to the Passenger application, and her GPS coordinate appears. She selects it, and the nearest address to that location is listed first, it's her home address. Nearby locations are also listed. She decides to meet her driver at the nearest corner store. She can walk there and pick something up for the party before her driver arrives. She selects the store from the list. The store address appears, and Sara enters the address of the party she wants to go to. The distance and route are calculated, and a list of drivers slowly starts to appear as the Driver clients receive her request and decide if they'll accept the route and for what price. Three driver clients appear on the list, all with good ratings and Sara selects the driver with the lowest bid per mile even though the arrival time is longer. She'll have plenty of time to walk to the corner store and wait for the driver. She enters her payment information, and the transaction is recorded by Passenger. It knows she can afford the ride and holds the funds until drop-off.
There's 30 minutes before the estimated arrival time, and it's only a three-minute walk.
She disconnects her earpiece from her mobile and reconnects to ID on her MacBook. She has at least twenty minutes to sort through some files and decide what else she wants to upload to her identity chain. She knows it would be illegal to upload her music files, but those can be accessed through the Toonz app as each artist creates their own identity anyway. Besides, she doesn't need to upload her music files to listen to them. She has other events coming up on Facebook and Google+ and on her iCal, and even though they're all synced on iCal, there's got to be a better way to coordinate events with ID. Something simple and elegant. Something that doesn't care where the appointment data derived from and can automatically RSVP, cancel, or schedule a meeting regardless of what applications her contacts are all using, as long as they also have ID. How did Kate manage to invite everyone on Facebook, Google+, and email? Sara texts Kate, "Hey what app did you use to invite me to your party? You're on ID right?"
"Yeah are you on now!?" Kate replies.
"Yeah :) I uploaded my genome and got a ride. I like it."
"Go to Connect > search and type in my contact code bodaciousbabe55."
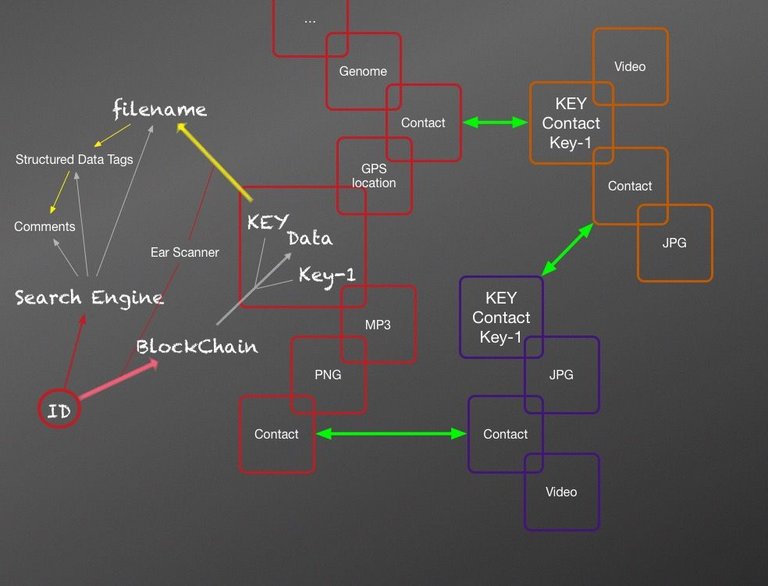
"lol ok," Sara clicked on the connect menu in ID and searched for bodaciousbabe55. A menu popped up from settings, and asked: "Create a unique connection name." Sara typed in 'SaritaBlue' and hit 'Authorize.' Her ear buzzed again as ID scanned for authorization and generated her connection identity. A connection to Kate wrote to Sara's blockchain. She had her first set of contact data. She clicked on bodaciousbabe55 and saw a list of social network identities for Kate. Sara checked ID on her mobile device and selected 'Contacts,' bodaciousbabe55 was listed, and now Sara could send text messages to Kate from the ID applications, make voice calls to Kate, or even start a video chat. She saw that group-conference options were also available. She could connect to as many contacts as she pleased. A notification appeared in the ID terminal, and Sara clicked on it. It gave her the option of joining a conversation with Kate and others. She accepted the invitation and a video chat window opened with Kate and three more of their friends. Sara immediately added Doug, Vic, and Ashton to her contacts.
"Hiya Sarita!" said Vic.
"Yo!" said Ashton.
"She's one of us!" shouted Kate.
"Sara's on the blockchain," said Doug.
"Hi guys!" said Sara.
"Install Bevy," said Kate.
"Alright," Sara opened up the search console and found the Bevy app, "I'm installing it now. Is this conversation being written to our chains?" asked Sara.
"Yup," Ashton replied.
Doug continued, "Every conversation we initiate from ID through our contacts is stored on our chains."
"This conversation is being recorded," said Ashton in a robotic feminine voice.
Doug explained, "After you hang up you'll see the file listed with tags for the time and contacts. You can add any other tags you want whenever you want."
"If we say something memorable," said Ashton, "you can tag it and quote me in the comments."
"Bevy will help you sort through it all," said Doug, "ID and Bevy will sync your contacts, and then you can organize people into multiple groups. Bevy also works with most social media applications so you'll sign into your social media accounts from Bevy and then you can manage all your messages and the blockchain content you want to share."
"You'll get it quick," said Kate.
"Will Bevy let me talk with people who aren't ID'd yet?" asked Sara.
"Yeah," everyone answered.
"That's how I set up the event, that's how I was chatting with you earlier. I had you as a contact in Bevy and linked it to your Facebook and phone number. I never log into Facebook anymore, and I don't even have a text plan, just data."
"It's all you'll ever need," said Ashton.
"It takes some getting used to," said Vic, "but it's pretty much a universal solution to social media."
Doug explained, "Bevy works with ID to get your authorization for content you want to share and write to your blockchain. Bevy gives you the option of writing a conversation to your blockchain after you hang up, it's like using a regular social media network but with more options. The only drawback is that Bevy can't import your data from Facebook, or Instagram, or Twitter, or any of the social media platforms that aren't written in ID's open protocol. But you can use Bevy to post data to those dinosaurs if you want to. One day the compatibility won't even be necessary, but it's a convenience while people come around."
"See you all at the party! I'm heading over," said Ashton.
The rest said their farewells and hung up. They'd all see each other at Kate's house soon.
Sara walked to the store to catch her ride. She could see the driver en route from the Passenger app. She had just enough time to pick up some beers before the driver arrived. He stopped, and Sara opened the door, "Hi," she said.
"First time huh?" asked the driver.
"Yeah," answered Sara.
When they arrived at Kate's house, Sara's phone buzzed.
"transaction complete," said the Passenger app.
"Thanks for the lift!" said Sara climbing out of the car.
"Thanks for being my passenger!" said the driver.
As soon as he drove away Sara's phone buzzed again, "Rate your driver," it said, she gave him five stars and added no comments. Her profile now had a five-star rating with one driver. "Welcome to Passenger!" read the comments. Nice.
What if this story goes from being a sci-fi blurb to becoming an account of a regular day for someone once ID, in whatever form it will take, comes into being?
It's possible that the way we use the internet on our computers and our phones will transform and improve wildly. I think someday storage space won't be an issue and we'll have so much space for data that running out of it will never come into our mind. But the way that data is logged into the internet right now is redundant and we often don't own our own content once we author posts on social media platforms. And don't we all despise having to be part of multiple social networks that are designed to take ownership of our content when we use them? What if an open protocol platform like ID came into existence? A platform with an interface that allowed each of us to author our own blockchain containing any information about ourselves that we wish to write to it, and not even necessarily to share it with anyone else. There's a lot of exciting questions about this future world.
I think that an identity chain is a fantastic notion but at the same time, as with everything else so transformative, it comes with so many issues.
How would an identity blockchain be used in court?
What about identity blockchains containing evidence of illegal activity, crimes being committed, or people being abused?
There are cases in which a person needs a new identity for their protection. There are cases in which a person wants a new identity as a fresh slate, a way to start over. Shouldn't people have the ability to create as many identity chains as they desire? But then, if these identity chains are truly secure, truly encrypted as well as BitCoin, then we'd never need a new identity chain for protection from anything but ourselves.
If the password is always a fingerprint or an ear scan or an eye scan then a password can never be forgotten and an identity can be better protected. But it could not be duplicated, could it? Could you change your password? Could you upgrade from a token to a fingerprint, to an eye scan, to an ear scan?
If multiple identity chains can exist for a single person, which they undoubtedly can, then identity chains can also be designed with token passwords, as they are now, bypassing the need for a scan to authorize writing and accessing.
This means that identity chains could be created by criminals to allow transactions of their illegal activity. And these would always be encrypted. In any case, any person could upload illegal content and that content could never be deleted. That leads to the benefits of decryption technology. That too will undoubtedly be created and it would be vital to catching criminals. And then the decryption technology could also be abused and lead to terrible trespasses of privacy.
Beep! Beep!Ooh-Rah!
Comment by @inthenow. This is a opt-in bot. @shadow3scalpel at your service. I am here to assist all military members on Steemit. This HumVee will be scouting posts from a list of Veterans that is maintained by @chairborne. If you are a Veteran and new to Steemit, and you have questions or want to join the Veterans community, reply to this comment. We got your six, unless you are in the rear with the gear.