What happened?
Sophos received a report on April 22, 2020, at 20:29 UTC regarding an XG Firewall with a suspicious field value visible in the management interface. Sophos commenced an investigation and the incident was determined to be an attack against physical and virtual XG Firewall units. The attack affected systems configured with either the administration interface (HTTPS admin service) or the user portal exposed on the WAN zone. In addition, firewalls manually configured to expose a firewall service (e.g. SSL VPN, SPX Portal) to the WAN zone that shares the same port as the admin or User Portal were also affected. For reference, the default configuration of XG Firewall is that all services operate on unique ports.
The attack used a previously unknown pre-auth SQL injection vulnerability to gain access to exposed XG devices. It was designed to exfiltrate XG Firewall-resident data. Customers with impacted firewalls should remediate to avoid the possibility that any data was compromised. The data exfiltrated for any impacted firewall includes all local usernames and hashed passwords of any local user accounts. For example, this includes local device admins, user portal accounts, and accounts used for remote access. Passwords associated with external authentication systems such as Active Directory (AD) or LDAP were not compromised.
How did Sophos respond?
Sophos immediately began an investigation that included retrieving and analyzing the artifacts associated with the attack. After determining the components and impact of the attack, Sophos deployed a hotfix to all supported XG Firewall/SFOS versions. This hotfix eliminated the SQL injection vulnerability which prevented further exploitation, stopped the XG Firewall from accessing any attacker infrastructure, and cleaned up any remnants from the attack.
After analyzing the components and intent of the attack, Sophos published a SophosLabs Uncut article, “Asnarok” Trojan targets firewalls, to share its current understanding of the malware.
Was my XG Firewall compromised?
The XG Firewall hotfix that Sophos deployed includes a message on the XG management interface to indicate whether or not a given XG Firewall was affected by this attack.
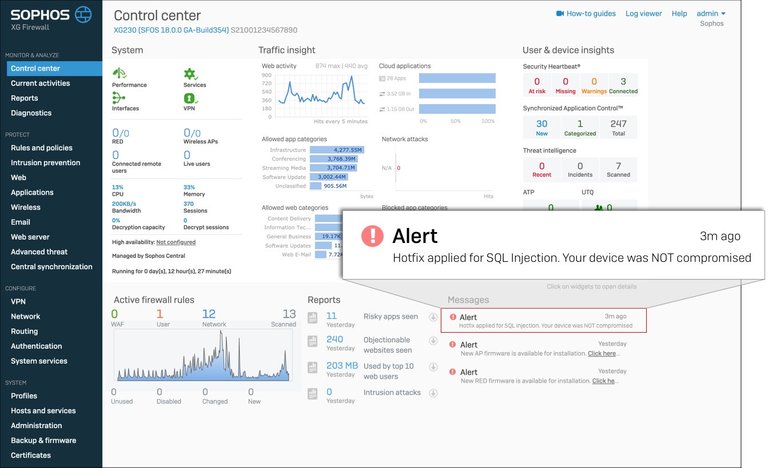
Scenario 1 (Uncompromised):
Hotfix applied to an uncompromised firewall
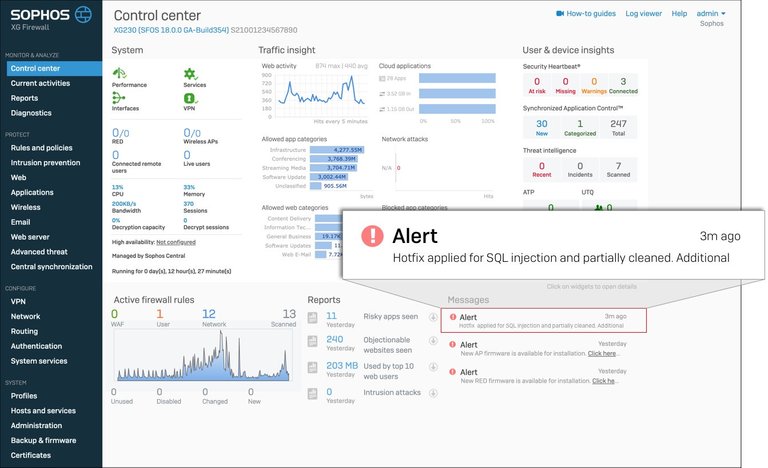
Scenario 2 (Compromised):
Hotfix applied and successfully remediated a compromised firewall
How can I ensure that I receive the hotfix?
If you have disabled “Allow automatic installation of hotfixes”, please reference the following KBA for instructions on how to apply the required hotfix: https://community.sophos.com/kb/en-us/135415
Note: Customers managing XG Firewalls with either Sophos Firewall Manager (SFM) or Central Firewall Manager (CFM) need to verify each firewall has an active connection with firewall management to receive critical updates. These steps are not required for Sophos Central managed devices.
Do customers need to do anything after the hotfix is applied?
For uncompromised XG Firewall devices, no additional steps are required.
For compromised XG Firewall devices that have received the hotfix, we strongly recommend the following additional steps to fully remediate the issue:
- Reset device administrator accounts
See: https://community.sophos.com/kb/en-us/123732 - Reset passwords for all local user accounts
See: https://community.sophos.com/kb/en-us/135419 - Although the passwords were hashed, it is recommended that passwords are reset for any accounts where the XG credentials might have been reused.
Note:
The hotfix alert message does not disappear once the hotfix is applied. The full alert will remain visible in the XG management interface, even after the hotfix has been successfully applied and even after any additional remediation steps have been completed.
While customers should always conduct their own internal investigation, at this point Sophos is not aware of any subsequent remote access attempts to impacted XG devices using the stolen credentials.
As a general best security practice to reduce attack surface wherever possible, Sophos recommends disabling HTTPS admin services on the WAN interface. If the User Portal is not being used, Sophos also recommends deactivating this service on the WAN as well. See: https://community.sophos.com/kb/en-us/135414
For recommended remote administration options, please consider the following:
Administering your firewall via Sophos Central
Administering your firewall via Remote Access VPN
Are there any additional steps I should take to secure my environment?
The following steps are recommended to further secure your environment:
- Do not expose any service on the WAN interface, unless necessary
- Ensure that you have enabled the automatic installation of hotfixes. See https://community.sophos.com/kb/en-us/135415
- Enable Multi-Factor Authentication or One Time Password (OTP) where possible:
- One Time Password: https://docs.sophos.com/nsg/sophos-firewall/18.0/Help/en-us/webhelp/onlinehelp/nsg/concepts/OTPTokenManage.html
- Multi-Factor Authentication: https://docs.sophos.com/nsg/sophos-firewall/18.0/Help/en-us/webhelp/onlinehelp/nsg/sfos/learningContents/ConfiguringTwoFactorAuthentication.html
What firmware versions of XG Firewall (SFOS) were impacted?
The vulnerability affected all versions of XG Firewall firmware on both physical and virtual firewalls. All supported versions of the XG Firewall firmware / SFOS received the hotfix (SFOS 17.0, 17.1, 17.5, 18.0). Customers using older versions of SFOS can protect themselves by upgrading to a supported version immediately.
Source
Plagiarism is the copying & pasting of others work without giving credit to the original author or artist. Plagiarized posts are considered fraud and violate the intellectual property rights of the original creator.
Fraud is discouraged by the community and may result in the account being Blacklisted.
If you believe this comment is in error, please contact us in #appeals in Discord.