
When you hear cryptocurrency, a word comes quickly to a question in the minds of people: security!
And no wonder, many news of embezzlement have gone around the world, The most famous of these attacks occurred in June 2011. A hacker (or group of hackers) allegedly accessed a computer that belonged to one of the auditors , and exploited a security vulnerability to access the servers. The hackers changed the nominal value of Bitcoin to 1 cent.
Then they proceeded to divert around 2,000 BTC. Some customers unknowingly bought 650 BTC, when the price was artificially deflated. Despite the fact that the trick was news throughout the world, none of the coins was returned.
In 2016, Bitfinex was the largest Bitcoin Exchange in the world, until it was surpassed by ANX. On August 4, they stole approximately 119,756 Bitcoins from customer accounts. The thieves took coins from clients' portfolios, despite the presence of multiple levels of security. This was another of the biggest cryptocurrency hacks.
The violation occurred through a multiple signature procedure, which allowed a transfer of funds. This is how things were configured: Bitfinex would contain 2 keys, while another blockchain company, BitGo, would keep a third key. Together, these keys would allow BTC (and other cryptocurrencies) to transfer them.
AND BECAUSE THIS HAPPENS?
These and other platforms use online hot purses (which are vulnerable to hackers, denial-of-service attacks and the disappearance of the company in charge of custody). Without a secure, scalable and secure cryptocurrency key escrow solution, institutions and individuals will continue to suffer frequent financial losses due to mishandling of their codes.Hot storage solutions are inadequate for key custody. Simply, anything connected to the Internet can be hacked. If we take into account the 4 billion records filtered in the last two years, with the consequent impact for email providers, banks and credit card accounts, and that over the same period of time more than 1.2 billion dollars have been stolen. USD in cryptocurrencies, it is clear that the traditional digital asset storage sector is affected.
WHY NOT USE A PHYSICAL DEVICE?
Before Hardware Wallets existed, Paper Wallets were the major security system used to store Bitcoin. Basically, a Paper Wallet is an impression with the address of Bitcoin and the QR. That is, it contains the basic information to send and receive Bitcoins. The great advantage of this is that, since the Bitcoin wallet is printed on paper, it is impossible for hackers to access a device and try to steal it, as there is no digital copy.
The disadvantage of paper comes with the characteristics of it. The paper can break, it can get wet, burn or wear out over time, and the information eventually gets lost. That is why some people choose to laminate them and even print their Paper Wallets on metal plates.
Digital wallets have also been developed and it is like carrying a pendrive with all the necessary information for your transactions, but in reality who has not lost a pendrive in your life? Many are sensitive to heat, so if we keep in locked places and "safe" to return for them to use them we can find the unpleasant surprise that this no longer works
The cold storage encryption solutions offered by groups such as Xapo or Coinbase have a very limited accessibility that does not meet most of the custody needs of the institutions. Storing an encrypted key in an inaccessible chamber of a bank can be a viable security solution for a person or an institution that do not want to make purchase transactions, but getting access to the USB memory takes days and is not practical for the active management of assets.

THE GOLDILOCK SOLUTION
If we currently have two ways to safeguard keys and digital assets, it is logical to think of designing a platform that adds the advantages of these two modes of cold and hot storage) and thus be able to create a unique tool that guarantees the protection of investment and information of all
To achieve the union of these two Goldilock systems, you create 3 referents that should not be missing from your platform:
The wallet is stored offline through a physical "air gap" mechanism, and the wallet can not be accessed from the Internet.
With a mechanism without IP, the user activates his wallet so that it is accessible through the Internet.
The user can securely access their wallet through an encrypted connection with a URL destined for this and access credentials.
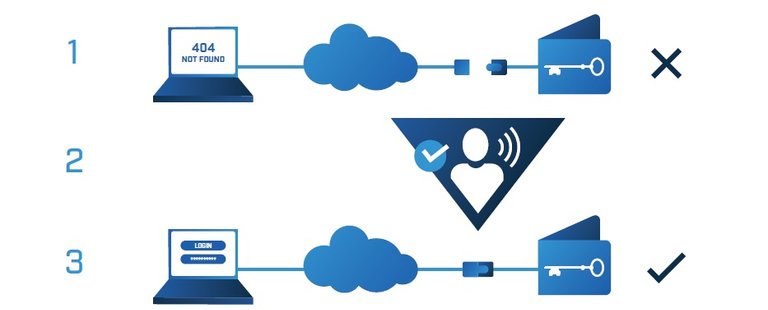
In this way the platform provides excellent security with a safeguard of cold assets but with the ease of user access to their assets as if using a hot storage
The system can be used to store private keys for cryptocurrencies, banking and credit information, personal identities, health data, digital media and signing or approval codes. Through the standard functionality of cryptocurrency purses, funds can be associated with a consumer's public key address without the need for your Goldilock wallet to be online. The Goldilock wallet of each consumer only has to be online to make withdrawals or outgoing transfers.

Goldilock offers a key protection and data storage which includes the following:
Disconnection «air gap» physical electronic networks:
The users need to access their personal data in a fast and safe way but in very short periods of time, if these data after their use are online can be a victim of hackers, so after using the data the platform performs the physical disconnection of the electronic network containing the information
Hardware for each user for the processing of encrypted data storage:
The hardware is the physical device where the information is stored, each user will have a hardware for their personal information
Regressive connectivity and signal processing:
computer science and statistics in the development of techniques that allow machines to "learn". It is present in applications that detect fraud in credit cards, elaborate medical diagnoses and recognize voice
Biometric gateways
Biometric authentication or computer biometrics is the application of mathematical and statistical techniques on the behavior traits of an individual, for their authentication, that is, verifies their identity.
Device recognition
This creates a record of common devices used by the user to improve the speed of entry and security
Personally generated codes
Without any type of repetitive pattern that damages the level of security of the user
Scalable physical segregated connectivity solutions
To generate market innovations without scalability problems in the future
Two-phase authentication
Using the NAO blockchain technology and the Goldilock ecosystem blockchain
Optional multifirm security
For accounts of associations multinational companies or any other that require it
Physical cameras protected
The protection of information is guaranteed in the most appropriate and safe way
Encrypted multi-site data backup
Guaranteed to have a backup at the time of any problem that affects the integrity of user data
Goldilock fully guarantees the extraction and delivery of data to the owners when they request it or in case of cessation of commercial operations

APPLICATIONS IN THE GOLDILOCK ECOSYSTEM:
Offering an innovative service that adds the best security features of the various methods of safeguarding information and digital assets also provides the need for methods and applications necessary to link this technology with existing systems to create a tool with high availability in the market
Goldilock coin purse for cryptocurrencies
Goldilock's central development team will develop Goldilock's purse with the initial objective of storing NEO, GAS and NEP-5 tokens and of transacting with these cryptoactives, which will make NEO the safest cryptocurrency in the market.
The Goldilock wallet will run in an authenticated web browser through SSL.
Because the use of SSL:
SSL (Secure Sockets Layer) is a global security standard that allows the transfer of encrypted data between a browser and a web server. It is used by millions of companies and individuals online to reduce the risk of theft and manipulation of confidential information (such as credit card numbers, user names, passwords, emails, etc.) by hackers and thieves. identities. Basically, the SSL layer allows two parties to have a private "conversation".
Using the technology of SSL and the Goldilock platform, the purse will have a high level of security that is difficult to match in the current market, generating virtues such as:
The keys of each purse will be in a unique hardware device, segmented and encrypted disconnected from the Internet.
The wallet will be connected by means of a command without IP and a verification by PIN or voice through the telephone network (RTC) without IP.
After closing the wallet, the single hardware wallet device will be disconnected from the Internet.
Each purse will be assigned an exclusive personal URL.
Each signed transaction will require authentication in two phases.
Goldilock API Services (what is API)
Examples of use of web APIs
• Developers of any program for Windows that connects to the Internet do not need to include in their code the functions necessary to recognize the network card, for example: a 'call' is enough to the corresponding API of the operating system.
• Twitter-related platforms, such as search and filtering of mentions such as Topsy, or those of tweet management such as Hootsuite, can make use of the processing capacity of Twitter servers.
• Webmasters can automatically include Amazon or eBay products on their websites, allowing them to start the purchase process from their website. Or perhaps they allow you to identify yourself with Facebook Connect, saving you the complex process of user management (and avoiding the Internet user having to register in one more website). Likewise, the "+1" buttons on blogs are
calls to the Google API.
In short, we can see the use of APIs as a 'subcontracting' of functions. Of course, this subcontracting imposes conditions on the subcontractor: some sites such as Twitter or eBay limit the number of calls that a certain software or web can make to its API in a certain period of time (per minute, hour or day) before having to pay a license.

The Goldilock team will generate its own API services:
Goldilock's core development team will develop the Goldilock API services after the Goldilock wallet. The main objective of API services will be to allow institutions that already have purse solutions to use our patent pending solution with their solutions that require improved security.
Goldilock's API services will be executed on-site, in Goldilock's housing facilities and in the cloud. These services will make it easier for companies and associates to create applications focused on privacy and based on consent. The APIs can be integrated into decentralized applications or independent applications.
Thanks to its architecture, after the initial implementation of the wallet for users focused on NEO, Goldilock will be able to serve other important cryptocurrencies in a matter of weeks.
IN DEFINITIVE APPLYING THE APPLICATION TECHNOLOGY API IS LOOKING TO GENERATE THE CONNECTION BETWEEN EXTERNAL PLATFORMS AND GOLDILOCK TECHNOLOGY TO BE ABLE TO PROVIDE THIS SERVICE TO ORGANIZATIONS ALREADY EXISTING WITH VERY SHORT PERIODS OF ADAPTATION
TOKEN LOCK:
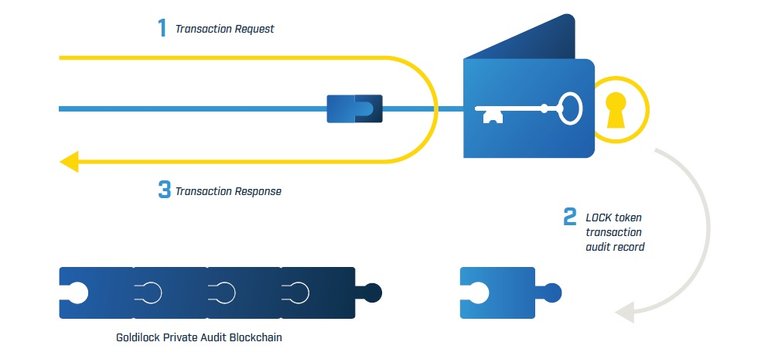
Goldilock will register its "LOCK" digital token as an asset of NEP-5 in the NEO blockchain. ¿ BUT THAT IS NEO AND HOW HELPS TOKEN OF GOLDILOCK?
NEO called the Chinese Etherium and formerly called with the official name of AntShares is a cryptocurrency based on the chain technology, it is the first of Chinese technology, which is decentralized and protected using digital certificates, has the purpose of creating intelligent contracts and a decentralized commerce.
USING THIS TYPE OF INTELLIGENT CONTRACTS OF THE NEO PLATFORM THE CALL IS MADE TO THE TOKEN LOCK
The LOCK token is necessary to access the Goldilock wallet. When the user logs into the Goldilock wallet, the wallet makes a query in the public blockchain of NEO to confirm that the public key address of that user has a LOCK token. If the user's public key address has a LOCK token, the Goldilock wallet opens in that user's browser. When the user is granted access, the wallet writes the audit information in our own private audit blockchain. These audit entries ensure that each time your private key is connected, this access will be written to an immutable storage where queries can be made from the Goldilock wallet.
Users will purchase LOCK tokens that, combined with the logic of Goldilock's intelligent contract, will allow the storage of cryptocurrency and other digital assets private keys, as well as constituting an immutable audit mechanism for all individual nodes with default tolerance to Byzantine failure (DBFT, a type of participation test [PoS]).
Our intention is to initially support NEO, GAS and the NEP-5 tokens in an effort to convert the NEO cryptocurrency into the safest available today. This step will precede the expansion of the platform with the inclusion of other popular and alternative cryptocurrencies.
You can find more information about our token economy at www.goldilock.com.

THE GOLDILOCK ECOSYSTEM OFFERS A COMPLETE SERVICE FOR USERS AS WELL AS FOR COMPANIES OR INSTITUTIONS
USERS:
To individual consumers, Goldilock offers an encrypted storage device, which is stored in a secure data center camera. The device is always physically disconnected from the Internet until the client decides to access it. Through an authorized command without IP that the client emits through the switched telephone network (RTC), the storage device is prepared remotely and is made accessible online through a secure web session initiation. Then, customers can access their data instantly to perform transactions through encrypted channels. When the client has completed the desired transactions, the device that manages the private keys securely is physically disconnected from the Internet. Goldilock does not have access to the keys or data stored on the client's encrypted storage device.
Cryptocurrency operators
The centralized public cryptocurrency operators often act as custodians of keys. Only in the last year, their dependence on current security methods has been the cause of the theft of billions of US dollars in cryptocurrencies. Every day there are thousands of attacks on the web against this type of platform, we know that very few attacks have a positive term, but risking our assets even in a small percentage is not an option
Instead of storing customers' passwords in online hot purses or keeping them offline and inaccessible in deep cold storage, Goldilock offers cryptocurrency operators their on-demand online environment, which reduces processing times for customers. transactions and allows better manage the periods of more traffic during the inevitable peaks of demand. The objective is to become an essential option both for operators who already offer custody and for those who wish to improve their offer by including custody for their clients.
Companies and their valuable data:
Clinical, financial and legal records are essential for the personal and legal well-being of the client. Goldilock offers an ideal form of storage with accessibility to the letter for this type of information. Goldilock, in partnership with banks, credit agencies, insurers, documentary management operators and data storage operators, will offer solutions for these markets. Thanks to its ability to support platform-as-a-service models and on-site deployment models, Goldilock allows data center operators, data repositories and document management, or even government entities, to establish a Goldilock instance for users

Cases where Goldilock would be important ally:
Personal use:
Marta has managed to realize her dream of being a travel consultant, studying English for several years and her university career ended recently, now Marta is hired by a transnational to practice her profession guiding tourists in many cities around the world, she knows that you should not just focus on the fun, she even knows that there are cities that are not very safe
Other things that marten is worried about is her payment, since it is in a currency that is not accepted in all the countries she visits, she will have travel expenses paid by the company but with only that money marta does not feel safe, she wants to have her portfolio of cryptocurrency that is being accepted worldwide, so she arrives at her job the first day with a more than reasonable concern
His teammate, Luis, tells marta that he should not worry about that issue anymore, because with a year of experience he already knows the solution to his worries, he tells him about Goldilock and the possibilities of safely saving his data of cryptocurrencies and valuable documents that you should not lose at any airport or hotel, Marta now flies happily with the Goldilock platform's backing
Commercial use:
An important record label is about to launch the new album of the most famous singer who is in his custody, they have been collaborating with artists around the world for more than six months, each artist arranges separately in his private studio or his home , then each artist sends his track and arrangement to the label's platform to assemble the themes, millions of dollars are at stake, and just before the scheduled date, all the album is pirated and placed on various social networks, the company loses millions and nobody is happy
The producer and head of the record label is desperate, it is not the first time it happens, and although he has increased the security levels of his platform and is tired of always the same, then he looks for information and sees a video of @aerossone that is hanging in https://www.youtube.com and decide to visit the Goldilock website
Since that day the producer's life is different, now he makes his collaborations worldwide without concern, all the invited artists follow the steps of his producer and safeguard the data of his collaborations in the multiuser account that the producer has in the Goldilock platform
video of @aerossone posted on youtube about Goldilock


THE SOLUTION FOR ALL
The benefits of the blockchain is indisputable, it is a historical evolution that is already changing the world in a positive way but there is a problem that comes to the minds of people when it comes to listening to blockchain and it is SAFETY, because the bad news is It expands more than the good ones and the issues of lost account theft and lost cryptocurrencies have inundated the web, the people who study this new financial world are sure that it is only a matter of time to solve this kind of problems and it is nice to see a solution really Serious and responsible with the Goldilock platform
The storage of data is a serious issue and more in this world, accounts are vulnerable to being connected to the web, thousands of pirates daily try to do damage and wreak havoc on the network, so there is only one way available and is to remove from the web important data and thus away from the bad hand, but there is a problem, availability for users, we all want to have our wallets available, data may be required at any time, so Goldilock creates this system which through security measures the data is uploaded to the web only when the user needs it, then the valuable data is taken from the web away from the pirates and steals accounts
Goldilock is revolutionizing the way data is stored on the Internet by creating an ecosystem to protect cryptocurrencies and digital assets for individuals and institutions and without a doubt it is the evolution in the area of data security needed by the blockchain to move on !!
For more information, see this brief Goldilock introduction
More Information & Resources:
Goldilock Website
Goldilock WhitePaper
Goldilock Tokenomics
Goldilock Telegram
Goldilock Discord
Goldilock Linkedin
Goldilock Facebook
Goldilock Twitter
Goldilock Reddit
Goldilock Github

GOLDILOCK TEAM


article by @aerossone for the @originalworks writing contest which is sponsored byGoldilock
to know more about the contest between here

goldilocktwitter
goldilock2018



)



This post has been submitted for the @OriginalWorks Sponsored Writing Contest!
You can also follow @contestbot to be notified of future contests!
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by aerossone from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.