"Ransomware" threat is on the rise, and cyber criminals are making millions of dollars by victimizing as many people as they can—with WannaCry, NotPetya and LeakerLocker being the ransomware threats that made headlines recently.
What's BAD? Hacker even started selling ransomware-as-a-service (RaaS) kits in an attempt to spread this creepy threat more easily, so that even a non-tech user can create their own ransomware and distribute the threat to a wider audience.
The WORSE—You could see a massive increase in the number of ransomware campaigns during the next several months—thanks to new Android apps available for anyone to download that let them quickly and easily create Android ransomware with their own devices.
Security researchers at Antivirus firm Symantec have spotted some Android apps available on hacking forums and through advertisements on a social networking messaging service popular in China, which let any wannabe hacker download and use Trojan Development Kits (TDKs).
How to Create Your Own Android Ransomware
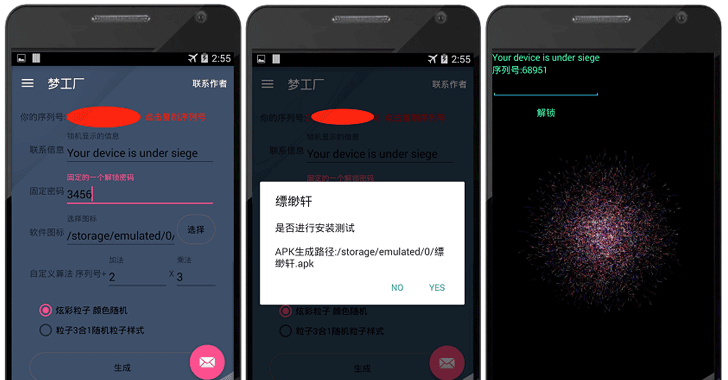
With an easy-to-use interface, these apps are no different from any other Android app apart from the fact that it allows users to create their custom mobile malware with little to no programming knowledge.
To create customized ransomware, users can download one such app (for an obvious reason we are not sharing the links), install and open it, where it offers to choose from the following options, which are displayed on the app's on-screen form:
The message that is to be shown on the locked screen of the infected device
- The key to be used to unlock that infected device
- The icon to be used by their malware
- Custom mathematical operations to randomize the code
- Type of animation to be displayed on the infected device
Once all of the information has been filled in, users just require hitting the "Create" button.
If the user hasn't before, the app will prompt him/her to subscribe to the service before proceeding. The app allows the user to start an online chat with its developer where he/she can arrange a one-time payment.
After the payment has been made, the "malware is created and stored in the external storage in ready-to-ship condition," and then the user can continue with the process, making as many as victims as the user can.
"Anyone unlucky enough to be tricked into installing the malware will end up with a locked device held to ransom," Symantec researchers
"The malware created using this automation process follows the typical Lockdroid behavior of locking the device’s screen with a SYSTEM_ALERT_WINDOW and displaying a text field for the victim to enter the unlock code."
The Lockdroid ransomware has the ability to lock the infected device, change the device PIN, and delete all of its user data through a factory reset, and even prevent the user from uninstalling the malware.
Such apps allow anyone interested in hacking and criminal activities to develop a ready-to-use piece of ransomware malware just by using their smartphones without any need to write a single line of code.
"However, these apps are not just useful for aspiring and inexperienced cyber criminals as even hardened malware authors could find these easy-to-use kits an efficient alternative to putting the work in themselves," the researchers say.
So, get ready to expect an increase in mobile ransomware variants in coming months.
How to Protect Your Android Devices from Ransomware Attacks
In order to protect against such threats on mobile devices, you are recommended to:
- Always keep regular backups of your important data.
- Make sure that you run an active anti-virus security suite of tools on your machine.
- Avoid downloading apps from unknown sites and third-party app stores.
- Always pay close attention to the permissions requested by an app, even if it is downloaded from an official app store.
- Do not open any email attachments from unknown sources.
- Finally, browse the Internet safely.