Top 10 FREE HACKING SOFTWARES
10.Nmap

Nmap is a free and open-source and very versatile network scanner software created by Gordon Lyon.Nmap provides so many features in computer networks, including host discovery and service & operating system detection.
Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses and acknowledgement
Nmap is used for exploring networks, perform security scans, network audit and finding open ports on remote machine.
The first version was released in the year September 1997.
Latest version is released in the year 13 Aug 2019.
The procedure that is to be followed by Nmap software.
Step-1:Create a complete computer network map.
Step-2:Find remote IP addresses of any hosts.
Step-3:Get the OS system and software details.
Step-4:Detect open ports on local and remote systems.
Step-5:Audit server security standards.
Step-6:Find vulnerabilities on remote and local hosts
9.SQLMAP
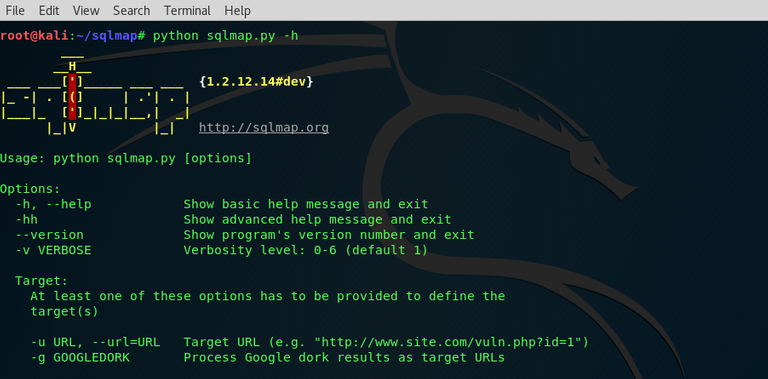
sqlmap is an open source used for penetration testing. It automates the process of detecting database vulnerabilities and provides options for injecting malicious codes into them and also exploiting SQL injection flaws providing its user interface in the terminal.
Discovery of hidden sensitive data such as the last four digits of a social security number hidden in another user id as part of a data masking also called as de-identification of project.
The procedure that is to be followed by Nmap software.
.Step-1: Get a Linux based Operating System
Step-2: SQLmap Installation
Step-3:Simple HTTP GET based test
Step-4:Getting blocked by the Web Application Firewall - WAF
Step-5:Dump the data
8.Reaver
Reaver implements a brute force attack against protected Wifi Setup (WPS) registrar PINs in order to recover WPA/WPA2, as described in this paper.
Reaver is efficient in WEP encryption is for securing a wireless network, showing that the Pwn Plug R3 can easily break into a WEP network in less than one minute
Reaver has been designed to be a very robust and practical attack against WPS, and has been tested against a wide variety of access points and WPS implementations.
The procedure that is to be followed by Reaver software.
Step-1:Boot into BackTrack
Step-2:Install Reaver
Step-3: Gather Your Device Information, Prep Your Crackin'
Step-4: Crack a Network's WPA Password with Reaver
7.TrueCrack
TrueCrack is a brute-force password cracker for TrueCrypt high and large Volumes of data. It can even work on Hidden volumes and Backup headers too.It works on Linux and it is optimized for Nvidia Cuda technology. .
It works very efficient manner in penetration testing.
TrueCrack works on the algorithm:PBKDF2 (defined in PKCS5 v2.0) is based on RIPEMD160 Key derivation function.
Method-1:Dictionary attack works efficiently to crack the passwords:It reads the passwords from a file of only words (one password for line).
Method-2:Charset attack:It can also generates the passwords from a set of symbols defined from the user (for example: all possible strings of n characters from the charset “abc” ).
6.HexInject

HexInject is a very versatile packet injector and sniffer, that provide a command-line framework for raw network access.
It's especially designed to work together with others command-line utilities, the utilities you usually use for processing for text output from executables or scripts (replace, sed, awk). This “compatibility” facilitates the creation of powerful of shell scripts, in a very little time, capable of reading,and also intercepting and modifying network traffic.
The procedure that is to be followed by HexInject software:
Step-1:Installation of Kali Linux
Step-2:Software upgrades & Configuring Kali Linux
Step-3: Building Penetration Testing Lab
Step-4:Exploitation &Scanning Networks
Step-5:Maintaining access
5.MITMf
MITMf literally stands for "Man In The Middle framework." It includes many, many different tools to help you with MitM attacks like ARP poisoning attack,stealing data and many more.
In this method hacker will be the mediator in between the sender and receiver.So whatever information shared by sender,hacker will receive the data and he gains access and steals information from user’s personal data like banking details and personal files.
Some of the famous methods of MITMF:
Method-1: SSL Hijacking
Method-2: IP Spoofing
Method-3:Stealing cookies of browsers(Static Data)
Method-4:Email Hijacking
Method-5:DNS Hijacking
4.Coockie Cadger

Cookie Cadger is a tool that can easily identify information leakage from applications that utilize insecure HTTP GET requests on Wi-Fi or wired Ethernet connections and networks.
It works on Windows, Linux, or Mac, and requires Java 7. Using Cookie Cadger requires having “tshark” – a utility which is part of the Wireshark suite. It has optional support for saving data to a MySQL database. A MySQL installation is required for this feature.
Some of the famous methods of MITMF:
Method-1: Modification of request before replay into the browser
Method-2: Fireheep intercepting and replaying a valid Facebook session cookie
Method-3:Intercepted session cookie loaded into Internet Explorer
Method-4:Modifying Internet Explorer Cookie data with IECookies View
3.AirCrack-ng

Aircrack-ng is a network software suite consisting of a detector, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs.
It focuses on different areas of WiFi security: Monitoring: Packet capture
It is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured.
The procedure that is to be followed by AirCracke software.
Step-1:First Download and install the latest aircrack-ng software
Step-2:After installation use airmon-ng monitor mode and Start the wireless interface
Step-3:Start the airodump-ng on AP channel with filter for BSSID to collect authentication handshake
Step-4: Use the aireplay-ng to deauthenticate the wireless client
(Which does’nt need any authentication or verification)
Step-5: Run the aircrack-ng to hack the WiFi password by cracking the authentication handshake
2.Burpsuite
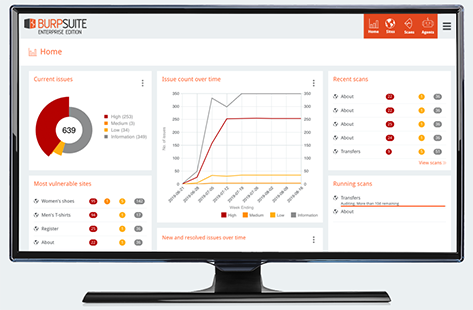
Burp Suite is a graphical or visual tool.Mostly used for testing Web application security.
It works seamlessly together to support the entire testing process, from initial mapping and analysis of an applications
This tool is written in Java and developed by PortSwigger Web Security.
To perform advanced security operations Pro version also available for this software with the cost of 339$/year.
It helps to identify vulnerabilities and verify attack vectors that are affecting web applications.
It is basically designed to be used by security testers, and to fit in closely with your existing techniques and methodologies for performing manual and semi-automated penetration tests of web applications.
The procedure that is to be followed by Burpsuite software:
Step-1:Enable the Burp’s Proxy listener
Step-2.To make sure that whether Burp’s Proxy Listener is in active or not go to “127.0.0.1:8080” local server and it will show checkbox is enabled and running in the interface column.
Step-3:Configure the browser to use proxy listener as its HTTP proxy server.
Step-4:Once the Burp is running go to Proxy Intercept tab and ensure that whether interception is turned on or not.
Step-5:If Burp is running then go to the browser and visit any URL.
Step-6.Each HTTP request made by the browser is displayed in the intercept tab.
Step-7:We can view each message, and edit if any required.
1.Metasploit
The Metasploit Project is a computer security software that provides information about security vulnerabilities and used to create security testing tools and exploit modules and also as a penetration testing system and also IDS signature development.Metasploit is commonly used to break into remote systems or test for a computer system vulnerability. It is owned by Boston, Massachusetts-based security company Rapid7
This software also provides pro version to perform advanced security operations like automated exploits and manual exploits.
.
The procedure that is to be followed by Burpsuite software:
Step-1: Reconaissance-Find Victim’s IP address
Step-2:Scan with Nmap & find running services
Step-3: Exploit a service to get a shell
Step-4:Attach a meterpreter payload to our exploit
Step-5:Add a PowerShell payload instead of a meterpreter payload to our exploit
Step-6:Spawn a Windows Command Line by executing shell and check with net users if our exploit worked.
