.jpg)
What dose MITM stands for?
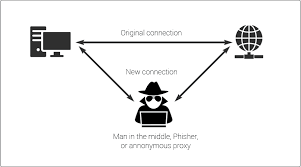
we can say that Man-in-the-Middle, or, in Russian, a person in the middle.
In simple terms, it is an attack when a person interferes with the connection between two people or a person and the Internet (browser, programs, etc.). In this case, it can either just "eavesdrop on traffic", or change it, and for both sides. The parties at the same time think that they communicate directly with each other and no third parties are watching them) Although in fact their communication (conversation with a friend, surfing the Internet through a browser, etc.) is completely controlled.
Schematically it looks like this:
The purpose of such an attack, as well as most computer attacks - is certain information and the ability to substitute it for their own purposes. Information can be very different, from the history of visiting the browser (yes, you can find out who looks at porn), to passwords from online banking.
Well, you can change the message in a correspondence with a friend, a girl, a boss, etc., thereby quarreling people, get secret information in the form of an answer to a spoofed message, and much more)
Domain spoofing is also often used. By simply eavesdropping traffic, you can not intercept encrypted traffic when using HTTPS, but you can redirect the user to a fake site, or make the user forcefully send HTTP to the site version, if that is in parallel with HTTPS)
What are the possible MITM attack options?
The most common MITM attacks using the Wi-FI router as a tool to conduct their attack. In this case, a fake router is used and the network is replaced. Errors in setting up and / or protecting the network can also be used, which allow you to connect to it and intercept traffic.
In the first case, the attacker distributes the wifai and calls it the same way as the public open network of the Waifai is called. At the same time, it can use deauthentication of users of this network. Roughly speaking, all throw out from the network, so that users reconnect to his network) And then he already quietly listens to traffic and intercepts what he needs.
The plus is that it's easier. Plus and minus simultaneously - many users, whose traffic can be intercepted, but you can get confused in it. The downside of this method is that people do not really trust open networks, and they rarely go there for online banking and such things. But here in the social network there often sit)
In the second case, a private private network is opened and an attack is performed. Also, all traffic is intercepted and intercepted.
The downside is that it's more difficult. Plus and minus simultaneously - users are few, but you will not get confused. But the plus is that most often the victim thinks that she is completely safe, so you can sit and catch traffic for a long time and most likely catch a large fish.
That's how friends are, be careful, especially in open Wi-Fi networks. Take care of your data.