A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.
In addition, the writing is excellent, although some of the depictions of Evil Corp employees, especially Tyrell Wellick, are a bit two dimensional and cliché. Overall, though, this is one of the best TV shows since Breaking Bad!
As the plot unfolds, it becomes clear that Elliot hacks and doxes the people in his life (including himself), then stores the information he finds onto CDs. He then labels them with some classic band label.

Many have wondered why he'd be doing that and how safe would that be?The answer is that Eliot is hiding the data on those CDs. He is actually copying music to those CDs, then embedding encrypted information on them that only he can recover. So anyone who finds them will see and hear only audio and will be unable to find or retrieve the hidden information. In this way, Elliot's data on his friends and acquaintances is safe from the prying eyes of law enforcement, or for that matter, anyone else.
What Elliot is doing is known as steganography, the practice of hiding information within another digital medium (audio, video, or graphic files).For instance, if I wanted to send someone else a secret message, I could place the message within a picture, audio, or video file and send it via email or allow them to download the file from my website. With the proper key and algorithm, they—and only they—could read the secret message. Everyone else would only see the innocuous picture or hear the audio file.Espionage and terrorist organizations have been using these techniques for many years (reportedly, Al Qaeda used these techniques to hide messages on their website to their followers in the 1990s and 2000s).In these episodes of Mr. Robot, Elliot appears to be using a software package named "DeepSound" for hiding information within his audio files, but there are numerous software packages for steganography available, including, but not limited to:
- QuickStego
- AudioStegano
- BitCrypt
- MP3Stego
- Steghide
- AudioStego
Although, in general, hackers use Linux to hack for many good reasons, DeepSound was developed for Windows. In this case, we will be using it on a Windows 7 system, but it can be used on just about any Windows OS.
Step 1Download & Install Deep Sound
To begin, we need to navigate to the DeepSound website and download the software.
Go ahead and download and install it to your system. Your AV software might balk, identifying it as a virus, but go ahead and allow its installation.
Step 2Deep Sound Interface
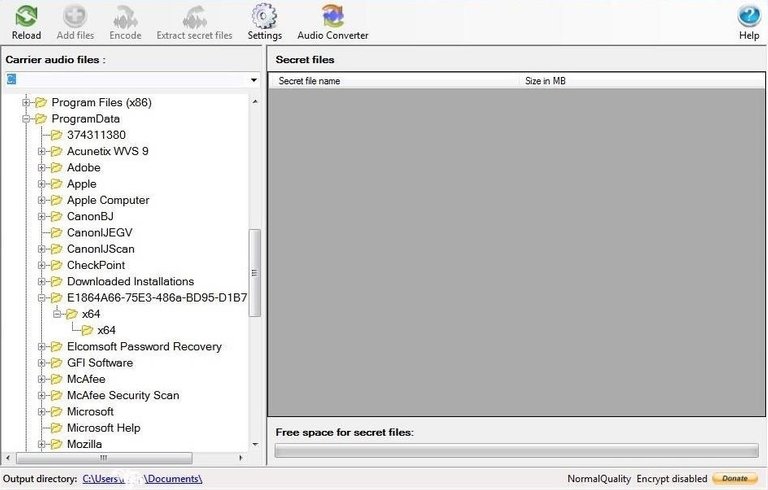
Once you have completed the installation, you should be greeted by a screen like the one below. Notice that on the left hand side of the screen it is displaying the directory structure of my C: drive. By clicking on the down arrow next to the C: drive above my directory structure, I can browse to other drives or USB devices on my system.
The files to the left will be my "carrier" audio files. In other words, these are the files I will use to hide my data in.
Step 3Settings
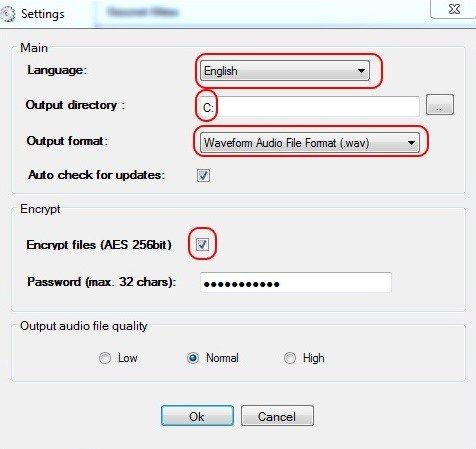
If I click on the Settings icon on the top bar, it will bring up a window like that below. I should set my default language (the only other choice besides English is Slovak), my output directory, and my output format. This software package only works with .flac or .wav files. This means that you can't use .mp3 files. This is presumably because .mp3s are compressed and the other two formats are not.
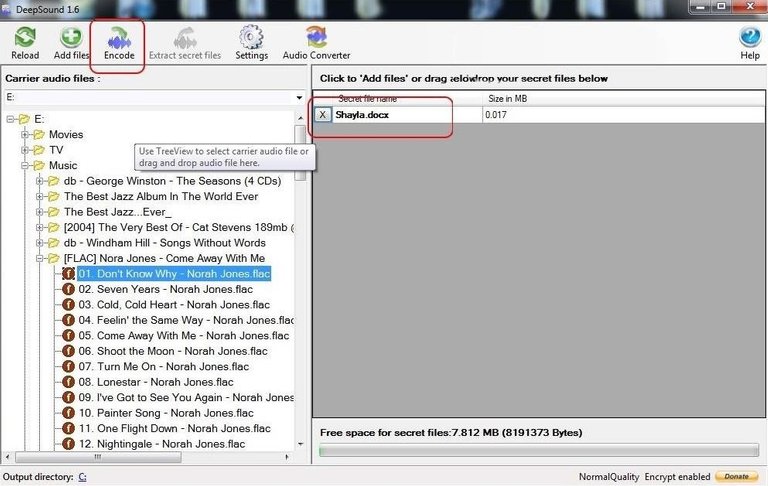
Also, make sure you click on the "Encrypt files" check box. This will make certain that your hidden files are encrypted with 256-bit AES encryption, among the strongest encryption algorithms available. Finally, add a password that will be used to lock and then unlock the encryption when you or the target of these files wants to recover them. The longer this password, the stronger the encryption.
Step 4Select Audio Files
Next, we need to select audio files to hide the data in. As most of my music, probably like yours, is in .mp3 format, those won't work. Notice that I have some Nora Jones in .flac format that I will use here. (Generally, audiophiles prefer .flac as its quality is superior, but the size is much greater as it is uncompressed. That's why most mobile audio devices use .mp3, they are much smaller files.)I double-click on the audio file and it prepares it for use to hide my files in.
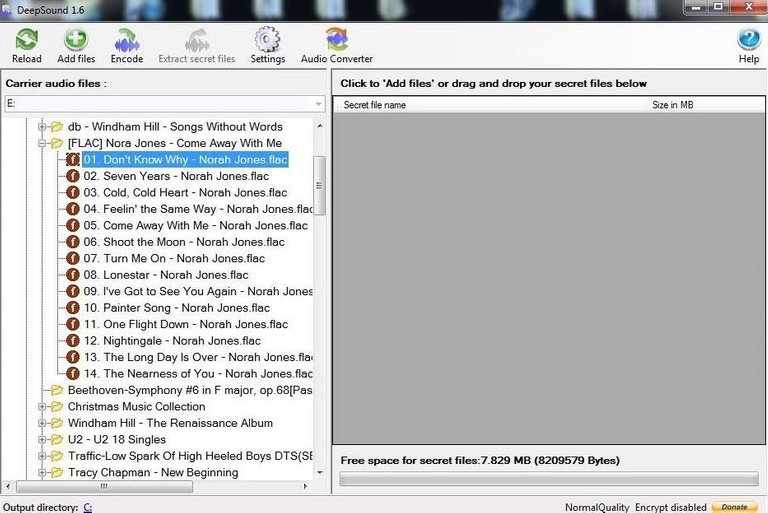
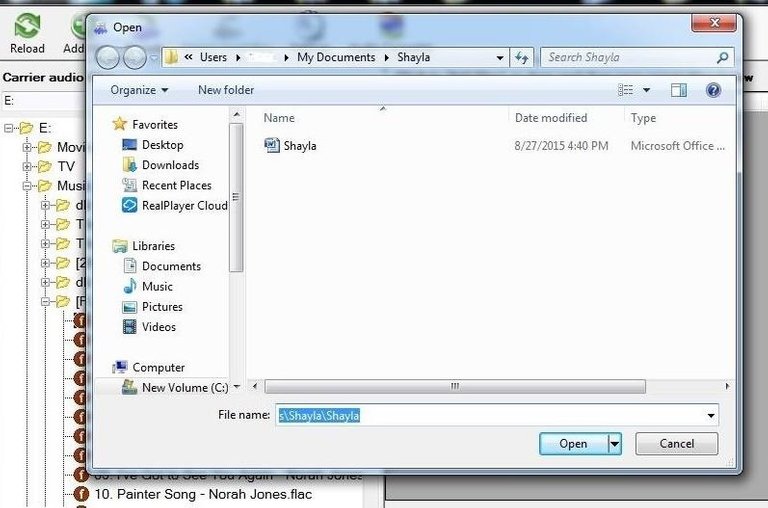
Next, click on the "Add files" icon on the top bar. This will prompt you to add the files you want to hide within the audio file. Here, I have a file named Shayla.docthat I want to hide within the Nora Jones audio file.
Step 5Encode
When I click on Shayla.doc, it adds it to the right window. Now, I need click on the "Encode" icon on the top icon bar.
My Shayla.doc file is now encrypted and hidden with my audio file! Not only with this file look and sound like a normal audio file, but if anyone wants the information hidden in it, they will need to decrypt it with the password known only to me.In the case of Elliot in Mr. Robot, he now took these audio files and burned them to a CD, but that isn't necessary. Presumably, he is doing that to take another step to secure these files in the case that his computer is ever confiscated and investigated. Any investigation is unlikely to listen to his music CDs.
Step 6Decode
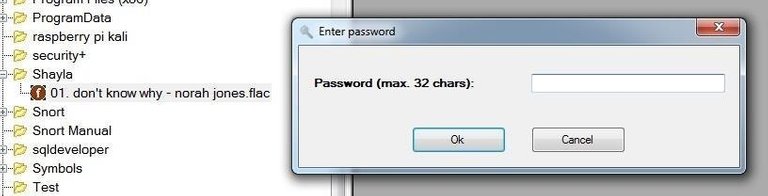
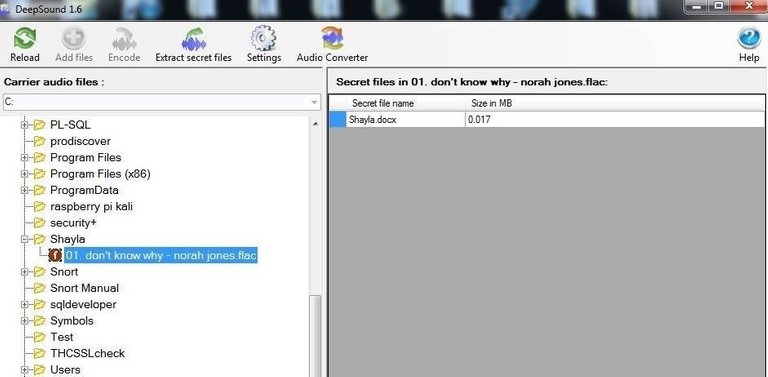
Eventually, Elliot, or the person the information is intended for, will need to decode the hidden information. Simply click on the audio file and then the "Extract secret files" icon. When you do, it will prompt you for a password. Enter the password you created in Step #3, hit "OK," and the hidden file will appear in the right hand window.
Now, you can read the hidden, secret message using the appropriate software that the message was created in. In this case, it would be Microsoft Word or any other software capable of opening a .doc file.
Keep coming back, my hacker apprentices, as we continue to explore the hacks of Mr. Robot and just about every other conceivable hack on the planet!
awesome
thanks buddy
Nice
Nice
Nice
Nice