Since the dawn of the World Wide Web, attackers have been involved in discovering techniques to compromise systems. Likewise security experts have devised methods to prevent attackers from breaching into systems. Such a system is two factor authentication. Two factor authentication is a method of utilizing a handheld device as an authenticator for online portals. While most organizations consider it a secure means of authenticating their users into their portals, there are methods using which two factor authentication can be bypassed. The techniques for bypassing 2fa are based on abusing the design and implementation which are often not looked at by web application administrators providing a leverage for attackers to compromise user data.
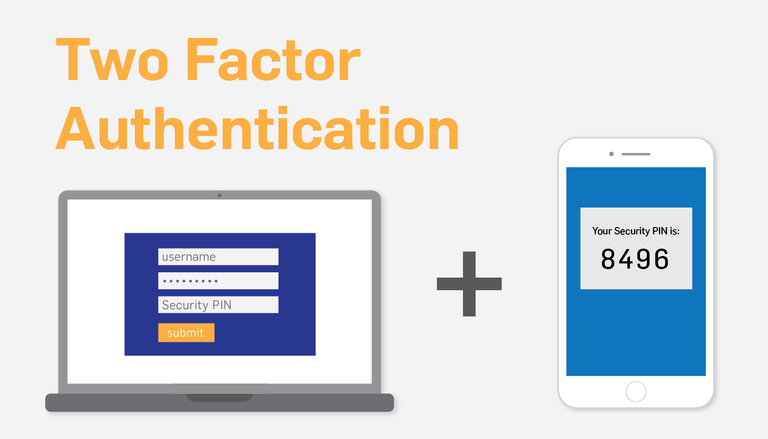
Working mechanism of two factor authentication:
Two-factor authentication (2FA) adds an extra layer of security to your online accounts by asking for a verification code after you sign in with your email address and password.
The verification code is generated by an application on your smartphone. To gain access to your account a potential attacker would need your email address, your password, as well as your phone. Two factor authentication works on the principle of “Something you have” which in most cases is your handheld phone (Shier, 2014). There are two method using which the one time code is delivered to your phone.
a. Using a text message
b. Using a third party software (Authy, Google Authenticator)
Using a text message

Web application vendors by using public SMS APIs can devise their own code generation algorithm to send the 2fa codes via SMS to the users. This method does not require any sort of internet access on the mobile phone rather it utilizes GSM to send out the one time codes.
Using third party software
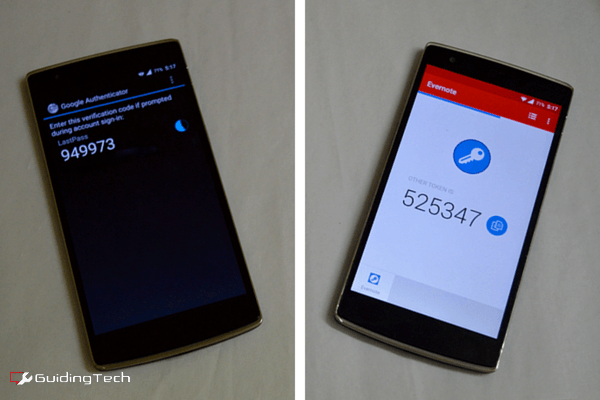
One time codes can also be sent by integrating the web application’s login mechanism with a third party software such as authy or google authenticator. This method required the phone to have internet access however using which the app communicates with its cloud interface which communicates with the web application’s login function to generate and synchronize timings with the login panel
There are basically 4 steps involved in the working of 2fa
Application authentication
Standard Login
OTP generation
OTP delivery
Types of Authentication Tokens:
Currently, there are three different OATH OTP types that are the most widely used: event-based tokens, time-based tokens, and challenge-based tokens.
Event-Based Token (HOTP): An OTP system generates event-based tokens on demand using a combination of a static random key value (HMAC; the H in HOTP) and a dynamic value, such as a counter (IETF, 2005). The event-based token is usually valid for a variable amount of time, but could be valid for an unlimited amount of time.
Time-Based Token (TOTP): An OTP system generates time-based tokens automatically every so often based on a static random key value and a dynamic time value (such as currently time of day). The time-based token is only valid for a certain amount of time, such as 30 or 60 seconds (IETF, TOTP: Time-Based One-Time Password Algorithm, 2011). TOTP is a subset of HOTP.
Challenge-Based Token (OCRA): An OTP system generates challenge-based tokens on demand (IETF, OCRA: OATH Challenge-Response Algorithm, 2011), using a random challenge key that is provided by the authentication server at each unique user log-in. The challenge-based token is valid for a certain amount of time such as several minutes.
Gaps in current two factor authentication mechanism:
The current two factor authentication mechanism is flawed from the aspect of its design to its implementation. The two factor authentication system was designed originally to strengthen the security of customers and users of online platforms. It was never taken into account that such a system should be secure on its own, due to this very fact there are a number of workarounds discussed further in the paper which can be used to bypass 2fa under various circumstances (Etay, 2014). However the prime focus here is towards identification of flaws in the 2fa implementation and design.
Bypassing two factor authentication:
In this paper, there will four methods of bypassing two factor authentication mechanisms in web based systems.
Bypassing 2fa using conventional session management
This method is about bypassing the two factor authentication mechanism using password reset functions. In almost all web applications the password reset function automatically logs the user into the application after the reset procedure is completed (Securityweek, 2016). Most of the time, the 2fa system is not implemented on the login function after the password reset. The process flow works in the following way
To Change Password > Request Password Reset Token > Use Password Reset token > Login to the web application
Using this technique the attacker can bypass the two factor authentication in online platforms. Basically the password reset token maintains a session with the application just after the reset has token place, which leads to the bypass.
Bypassing 2fa Via Oauth mechanism
A Oauth integration is a third party login mechanism that allows a user to login using a third party account. This is normally of a renowned web application such as facebook or google. A typical Oauth request works in the following way
Site.com requests facebook for auth token > facebook verifies user account > Facebook send callback code > Site.com logs user in
As it is observed that in this process flow there is no intervention of 2fa. An attacker can potentially abuse this mechanism and utilize a Oauth integration to log into the web application rather than using the username and password to do so (Shah, 2014). For this bypass to work the attacker must have access to the Oauth integration account to login on behalf of the user
Bypassing 2fa via brute force
Web developers leave a very disdinctive flaw when they forget to put rate limitation on the input fields, in case of 2fa if the field is not rate limited there is a possibility of brute force attacks using which the attacker can brute force the 2fa code sent to the device (Bullock, 2016). Usually the length of the 2fa code is 4 to 6 characters which often is numbers, and that makes to a possibility 151,800 which in real world scenario is easily brute forceable using a normal computer
Bypassing 2fa using race conditions
A race condition is termed as utilization of a previously known value recurrsively. It is an attack that takes advantage of application’s ability to utilize previously used or un used tokens at a later point in time. Considering that from 2fa prespective (Hoffmen, 2015), An attacker can utilize previously used or un used values of tokens to verify the device. However this technique requires the attacker to have access to the previous generated values, which can be done via reversing the algorithm of the code generation app or intercepting a previously known code.
Future Recommendations in 2fa security
2fa should itself have guidelines and briefings using which its implementation can be done securely, most organizations perform default implementation of 2fa due to which such vulnerabilities continue to arise and thus the security of their users is put at risk. 2fa is evolving into MFA (Multi factor authentication) which follows the same architecture as 2fa, meaning that the vulnerabilities are also similar.

MFA however utilizes not just the handheld device as point of authentication but multiple devices involving the Internet of things, MFA also has the same working principle as described earlier but instead of just a single point of authentication, it utilizes every and any device in the internet of things network. It generates the code upon based on that device. MFA will also be subjected to the same conventional bypasses as 2fa so its required that its architecture be manipulated to make it more secure
Conclusion
Two factor authentication in spite of all its vulnerabilities still remains the best approach to secure user accounts in conventional web applications. However that is not to say that the bypasses discussed should not be taken into account. Web developers should carefully review two factor authentication mechanisms in their website to ensure that common bypass techniques are dormant. However two factor authentication bypasses may emerge from time to time and different techniques may be involved in such attacks, the only way is keep iterating one’s own approach to test two factor authentication, that way it is easy predict the attacker’s methodology
Citation
For more information visit
https://shahmeeramir.com/4-methods-to-bypass-two-factor-authentication-2b0075d9eb5f
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://shahmeeramir.com/4-methods-to-bypass-two-factor-authentication-2b0075d9eb5f
Yup I give in citation
Cheetah where is your upvote WTF
Using an app on your On-Premise Platform is the most popular type of 2FA. It’s also very user-friendly and secure, since you can use dynamically generated passcodes. The only downside is that your phone’s microphone may be tapped by a criminal to obtain your passcode.