This solution doesn’t seem to be very well documented and I finally got around to testing it myself, so I’m dropping a quick demo.
Reverse meterpreter connections require port forwarding, which isn’t possible over tor (inside whonix). This is a simple solution for establishing reverse HTTP connections in msf:
Create A Hidden Server
Setup an onion as we normally would:
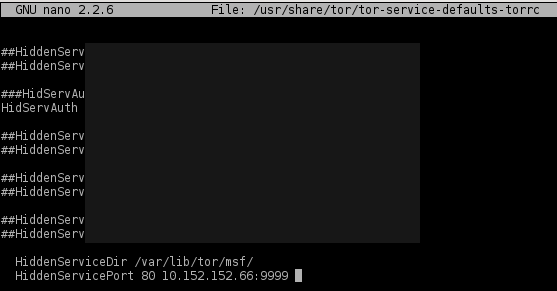
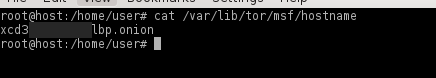
The onion MUST be listening on port 80 for this to work. The forwarding port (9999) can be anything you want. Restart tor, and take note of your new onion address:
Create payload
I created a simple (non-obfuscated) msfvenom executable for this demo but you should obviously encrypt your payload in a real scenario.
Set the payload type to reverse_http and the LHOST to your onion address but append .link to the URL. This will allow your payload to proxy between a tor2web clearnet domain and the tor network.
Configure msf
When configuring metasploit, set a reverse_http payload and set the LHOST to your local IP address with LPORT on 9999.

That’s about it. Feed the payload to your target and a session should be established in msf. I haven’t tested yet with the new .rtf CVE or MS Word macros, but I imagine it should work.
Also plan on looking at socat soon, it seems like it’ll handle such connections more elegantly.
Welcome to the platform, I wish everything work out for you. It’s not easy here but not difficult neither but just ask an extra effort, engagement is the key good luck I’m @goodaytraders Start by following people and they will do the same.
This guide was really missing, thanks!
Have you tried the port_bind? is a cheap way to avoid having to give an ip if you can avoid the firewall
Super post
Congratulations @shitcoinloard! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!