Good day good folks. i've been discussing #CommunityGovernance with @valued-customer (in this thread) and thought i would some questions from an #AI model (https://deepai.org/chat) re. anonymous onboarding for a #governance system.
My questions are the screenshots.
AI responses are the text.
80% of author rewards on this post are burned (sent to @null, i think that is burning).
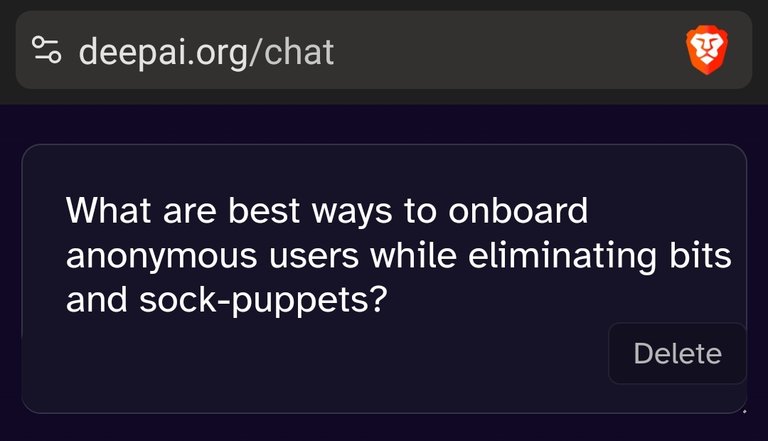
Onboarding anonymous users while minimizing the risk of bots and sockpuppets (fake accounts created by individuals to deceive) requires a strategic approach that combines technology, user experience design, and community management. Here are some effective methods to achieve this:
1. Implement Captcha Systems
- Use advanced CAPTCHA systems that are difficult for bots to solve, such as reCAPTCHA v3, which uses a risk analysis engine to differentiate between humans and automated systems without interrupting the user experience.
2. Email Verification
- Require users to verify their email addresses during onboarding. This adds a hurdle for bots and ensures that users are somewhat established in the real world.
3. Phone Number Verification
- Similar to email verification, requiring users to provide a phone number and send them a verification code can help ensure that users are genuine. Consider using various methods like SMS or voice calls.
4. Behavioral Analysis
- Monitor user behavior during onboarding and after sign-up. Anomalous behavior (e.g., repetitive actions or unusually fast input) can be tagged for further review.
5. Device Fingerprinting
- Use device fingerprinting techniques to track unique devices and identify patterns that may indicate bot activity or duplicate accounts.
6. Rate Limiting
- Apply thresholds on how frequently a user can interact with the onboarding process. This can help deter automated systems from trying to create multiple accounts in a short period.
7. IP Address Monitoring
- Monitor IP addresses for suspicious activity. Block or flag overly repetitive sign-up attempts from the same IP, which might be indicative of a sockpuppet or bot attack.
8. Content Moderation
- Implement AI-powered tools that analyze user-generated content for indicators of inauthentic behavior or spammy content, helping spot potential sockpuppets.
9. Community Engagement
- Encourage community involvement where users can flag suspicious accounts or behavior. A well-engaged user base can help identify and report anomalies that automated systems might miss.
10. Progressive Onboarding
- Instead of a strict single-step sign-up process, use a gradual onboarding experience where features unlock progressively. This can deter bots while providing a more engaging and human-like experience for genuine users.
11. Limit Anonymous Features Initially
- Offer certain features only to verified or longer-term users to encourage genuine interaction and connections rather than facilitating spammy or fake use cases.
12. Feature Request and Feedback Mechanism
- Create a space within the platform for users to give feedback or request features, which can promote genuine engagement and help vet accounts that might otherwise seem suspicious.
13. Transparent Policies and Reporting Mechanisms
- Communicate clearly about the platform's policies regarding fake accounts and harassment. Establish a straightforward method for users to report suspicious behavior.
14. Advanced User Profiles
- Encourage users to build profiles by adding elements such as profile pictures, bio information, or linking to other social media accounts. An empty profile often indicates a sockpuppet, while genuine users tend to provide information about themselves.
Each of these methods has its strengths and weaknesses, so a combination of them will often yield the best results. Balancing security measures with user experience is crucial to ensuring genuine users feel welcome while minimizing the risks associated with anonymous accounts.
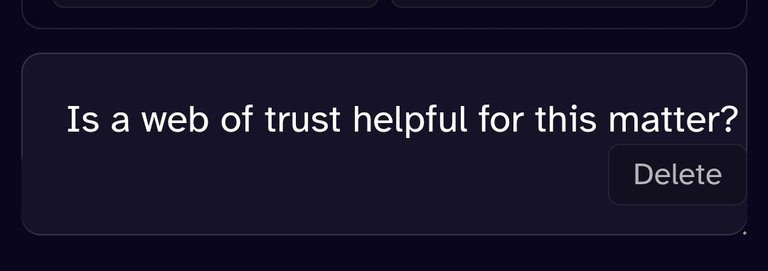
Yes, a web of trust can be quite helpful in onboarding anonymous users while minimizing the impact of bots and sockpuppets. A web of trust is a decentralized trust model where users assess and endorse each other's credibility, creating a network of trust relationships. Here’s how a web of trust can contribute to this effort:
Benefits of a Web of Trust
Peer Validation:
- Users can vouch for each other, which can help establish credibility. When a new user is endorsed by several trusted members, it reduces the likelihood that they are a bot or sockpuppet.
Gradual Trust Building:
- New users can start with limited privileges and gain access to more features as their trust score increases through endorsements and positive interactions within the community.
Community Accountability:
- A web of trust encourages users to take ownership of the community norms and standards, leading to a culture where users are more likely to report suspicious behavior or accounts.
Reduced Centralization of Trust:
- Unlike conventional systems that rely on a central authority for verification (like email or phone number checks), a web of trust leverages the collective judgment of the community, making it harder for bots to infiltrate.
Enhanced Privacy:
- Users can remain anonymous while still being able to establish or assess trustworthiness based on community endorsements, creating a balance between anonymity and accountability.
Deterrence of Malicious Behavior:
- Knowing that their actions are being monitored and can impact their trust score may deter some potential sockpuppet behavior or malicious activities.
Challenges and Considerations
While a web of trust offers many advantages, there are also challenges:
Initial Trust Distribution:
- New users might have a harder time gaining initial trust. Developing mechanisms to help new users receive early endorsements from existing community members is crucial.
Potential for Abuse:
- Groups of users could collude to falsely endorse each other, creating an artificial network of trust. This underscores the need for robust monitoring and mechanisms to detect abuse.
Complex User Experience:
- If not designed well, the onboarding process could become overly complicated as users navigate endorsements and trust levels.
Dependence on Community Engagement:
- The success of a web of trust depends on an active and engaged community. If users are inactive or unwilling to participate in trust-building, the system can stagnate.
Implementation Strategies
To effectively implement a web of trust in the onboarding process, consider the following strategies:
- Incentivize Endorsements: Encourage users to endorse others through rewards, badges, or enhanced features.
- Visibility of Trust Levels: Make trust scores or badges visible, so users can see the endorsements a new user has received.
- Encourage Verification: Prompt trusted users to verify new members through a simple process, aiding in the trust-building.
- Combining Approaches: Use a web of trust in combination with traditional methods (like email verification or CAPTCHA) to create a more robust onboarding process.
In summary, a web of trust can significantly enhance the onboarding process for anonymous users, fostering genuine interactions while reducing the risks of bots and sockpuppets, provided its implementation is well-considered and carefully managed.
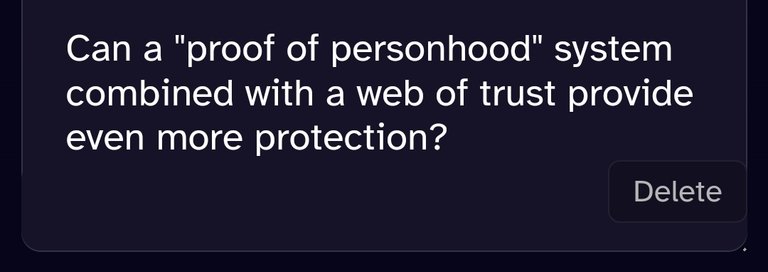
Yes, combining a proof of personhood system with a web of trust can enhance security and protect against bots and sockpuppets while still allowing for a degree of anonymity. Here’s a breakdown of how each component works together and the benefits that such a hybrid approach can provide:
What is Proof of Personhood?
Proof of personhood refers to methods used to establish that a user is a real individual rather than a bot or fake account. Techniques employed might include biometric verification (like facial recognition), confirmation of human behavior, or more decentralized approaches such as using social verifications via trusted acquaintances.
Benefits of Combining Proof of Personhood with a Web of Trust
Enhanced Authenticity:
- Proof of personhood helps establish that users are genuine humans, reducing the likelihood of automated bots or impersonators entering the system. This foundation fosters trust in the web of trust.
Strengthened Community Engagement:
- With confirmed identities, users may feel more secure interacting, knowing that other users are real people. This can promote more genuine engagement and community-building.
Reduction of Malicious Actors:
- By having to provide proof of personhood, it becomes more difficult for malicious actors to create multiple fake accounts. Those that do remain will likely be isolated and quickly reported by the community.
Informed Trust Building:
- The web of trust can operate on a more accurate foundation of verified users. When individuals can see endorsements from people who have also proven their personhood, trust can be more reliable.
Dynamic Trust Mechanism:
- A combined approach allows a responsive framework where users can start accumulating trust through endorsements after proving their personhood. This dynamic process encourages real human interaction while gradually building reputational capital.
Privacy Preservation:
- While proving identity, user anonymity can still be preserved through pseudonymous identifiers that link to their endorsements and trust levels in the web of trust, allowing users to participate without exposing personal data unnecessarily.
Implementation Considerations
While the combined system can offer substantial benefits, careful design and implementation are essential to overcome potential challenges:
User Experience:
- Striking a balance between the security processes and ease of onboarding is critical. Overly complex or invasive verification mechanisms could deter genuine users.
Accessibility:
- Consider implementing various proof methods to ensure inclusivity, allowing users from different backgrounds and with varying access to technology to prove their personhood without barriers.
Data Privacy:
- Any system that collects personal verification data must prioritize user privacy and comply with relevant data protection regulations (e.g., GDPR). Users should be aware of how their data will be used and protected.
Fraud Detection:
- Robust mechanisms should be built to monitor for fraud attempts, such as collusion among users to falsely endorse one another.
Community Education:
- Educating the user community about the importance of proof of personhood and the benefits of the web of trust is crucial to garnering participation and engagement.
Conclusion
A combined proof of personhood and web of trust system can greatly enhance the security and authenticity of online communities. By confirming the identity of users while facilitating community-driven trust mechanisms, this approach may significantly reduce the presence of bots and sockpuppets while promoting genuine interactions. With thoughtful implementation, it is possible to create a safe and engaging environment for both anonymous and identifiable users.
Yes, integrating knowledge tests as a mechanism for granting progressive access to different areas of governance can significantly enhance the robustness of a community or platform, thereby reducing abuse. Here’s how this approach could work and how it can contribute to maintaining a healthier and more accountable environment:
Benefits of Progressive Access through Knowledge Tests
Informed Participation:
- Knowledge tests can ensure that users have a clear understanding of community rules, governance structures, and relevant processes before they engage in decision-making. This helps to empower users with the information they need to contribute meaningfully.
Gradual Trust Building:
- By requiring users to demonstrate knowledge before gaining access to advanced governance features, the system ensures that only those who are truly invested in understanding the community can influence its direction. This gradual approach can help establish trust over time.
Deterrence of Malicious Behavior:
- Requiring knowledge tests acts as a barrier to entry for potential malicious actors who might be less willing to invest the time and effort to learn the community’s workings. This can deter users who are not genuinely committed to the community.
Identification of Engaged Users:
- Users who pass the knowledge tests demonstrate their engagement and commitment to the community, making it easier to identify those who are likely to act in its best interest.
Tailored Learning and Development:
- By providing users with materials or resources to study before taking knowledge tests, the community can promote ongoing education and understanding of governance, fostering a culture of continuous learning.
Feedback Mechanism:
- Knowledge tests can provide insights into common misunderstandings or gaps in knowledge within the community, allowing for targeted educational initiatives or improvements to community governance policies.
Considerations for Implementation
While knowledge tests can enhance governance structures, there are several key considerations for implementing this system effectively:
Test Design:
- Tests should be well-designed, fair, and reflective of the knowledge necessary for participating in governance. They should avoid being overly difficult or obscure so as not to discourage genuine users.
Accessibility and Inclusivity:
- Ensure tests are designed to be inclusive, considering users from diverse backgrounds and varying levels of familiarity with the community. Offering tests in multiple languages and formats can help reach a broader audience.
Continual Assessment:
- Users might need to refresh their knowledge periodically, especially as community policies or governance procedures evolve. Implementing ongoing assessments or updates can help keep users informed.
Transparency in Process:
- The criteria for passing knowledge tests and the levels of access granted should be transparent to all users to foster trust in the system.
Balancing Rigidity and Flexibility:
- While knowledge tests should enforce a level of competence, it’s also essential to maintain flexibility for users who may have practical experience but limited formal knowledge. Systems for alternative assessments or practical contributions could alleviate this issue.
Monitoring and Evaluation:
- Regularly evaluate the effectiveness of knowledge tests and adjust as necessary based on community feedback and metrics (like participation rates and quality of governance outcomes).
Conclusion
Incorporating knowledge tests as a mechanism for granting progressive access to governance areas is a promising approach to reduce abuse and enhance the quality of community engagement. By ensuring users possess the requisite understanding of community rules and governance, this strategy fosters a more informed, responsible, and dedicated user base. When implemented thoughtfully and transparently, it can significantly contribute to building a trusting and vibrant community while effectively mitigating the risks associated with abuse and malicious behavior.
Yes, adding a reputation system can provide several substantial benefits to a community or platform, particularly when combined with other mechanisms like proof of personhood, a web of trust, and knowledge tests. A reputation system can enhance user engagement, trust, and accountability while discouraging abuse. Here’s how it can be beneficial:
Benefits of a Reputation System
Encourages Positive Behavior:
- Users are motivated to engage positively within the community to improve their reputation scores. A well-structured reputation system can incentivize constructive contributions, such as providing helpful feedback, participating in discussions, or helping others.
Rewarding Expertise:
- Users who demonstrate knowledge and experience in specific areas can build their reputation over time. This helps establish recognized authorities or experts within the community, which can be beneficial for peer-to-peer decisions and governance.
Trustworthiness Indicator:
- A user’s reputation serves as a quick reference for others when considering interactions. High-reputation users might be viewed as more trustworthy, while low-reputation users could face scrutiny, reducing the influence of malicious actors.
Accountability Mechanism:
- Users can be held accountable for their actions within the community. Negative behaviors (such as trolling, spamming, or misinformation) can lead to a lower reputation, which may limit their access to certain features or influence.
Community Governance:
- Reputation can determine voting power or governance authority within community decision-making processes. This can lead to a more informed and engaged governance structure since users with higher reputations are more likely to be knowledgeable and invested.
Facilitates User Recognition:
- Recognition through a reputation system can enhance user satisfaction and loyalty. Members may feel more valued for their contributions, leading to higher retention rates and overall community health.
Dynamic Feedback Loop:
- A reputation system can include mechanisms for users to give feedback on each other, providing a dynamic interaction that encourages continuous improvement. Users can receive constructive criticism alongside positive reinforcement.
Differentiation of Roles:
- The system can create different tiers or roles based on reputation, allowing users to take on more responsibility or specialized roles as they prove their reliability and expertise. This can help streamline governance roles and contributions.
Considerations for Implementation
To maximize the effectiveness of a reputation system, careful planning and design are essential. Here are key considerations:
Transparency:
- Clearly define what actions contribute to reputation, how it is calculated, and the potential consequences of reputation changes. Transparency fosters trust in the system.
Preventing Abuse:
- Implement measures to prevent manipulation of the reputation system, such as collusion among users or retaliatory rating practices. Algorithms can be designed to detect unusual patterns and flag them for review.
Flexibility and Adaptability:
- Ensure the reputation system can adapt to changing community norms or goals. Regularly review and adjust reputation criteria to reflect evolving community values and practices.
Inclusivity:
- Consider how the reputation system will affect diverse user populations. Ensure it is designed to avoid bias and accommodate users from different backgrounds to promote an inclusive environment.
Balancing Quantity and Quality:
- Striking a balance between contributions and their quality is vital. A reputation system should not solely reward quantity of participation but also the importance and impact of contributions.
Integration with Other Systems:
- Ensure that the reputation system integrates seamlessly with the proof of personhood, knowledge tests, and web of trust elements. This holistic approach can offer a more secure and engaging experience.
User Education:
- Educate users on how the reputation system works and its importance to the community. This can help foster a culture of positive engagement and awareness.
Conclusion
Incorporating a reputation system can significantly enhance community dynamics by encouraging positive behavior, fostering trust among users, and promoting accountability. When aligned with other systems such as proof of personhood, a web of trust, and knowledge tests, a reputation system can create a robust framework for community engagement and governance. The key to effective implementation lies in transparency, adaptability, and inclusivity, ensuring that the system serves as a fair and motivating force within the community.
Yes, the Hats Protocol can be a valuable component in creating a robust governance and reputation system. It is designed to facilitate reputation management and identity verification in decentralized environments. Here’s how the Hats Protocol could enhance the proposed system, especially in the context of promoting positive behavior, trust, and accountability within a community or platform:
Benefits of Using Hats Protocol
Decentralized Identity Verification:
- The Hats Protocol allows users to establish verified identities without centrally managing that data. This decentralized approach can enhance user privacy while ensuring that participation is tied to verified accounts, reducing the risk of fraudulent or malicious behavior.
Reputation Tiers:
- With the Hats Protocol, users can earn “hats” that signify their reputation or expertise in different areas. This can be visually appealing and immediately recognizable, making it easier for community members to understand each other's contributions and areas of authority at a glance.
Dynamic Role Assignment:
- The protocol allows users to gain or lose hats based on their actions within the community. This dynamic aspect of role assignment can encourage ongoing positive behavior, as users will strive to maintain or improve their reputation over time.
Integration with Other Systems:
- The Hats Protocol can be integrated with knowledge tests, governance participation, and user feedback to create a comprehensive reputation and governance system. It provides a mechanism for users to earn hats through involvement in knowledge tests, contributions to governance discussions, or helping others.
Flexibility and Customization:
- The Hats Protocol allows for customization based on community needs. Different communities can create their own hats to signify various roles or contributions, making it adaptable to varied governance structures and norms.
Transparency and Trust:
- Since contributions and hats are publicly verifiable on the blockchain (or underlying technology), this transparency fosters trust within the community. Users can see how reputation is built and maintained, reducing the potential for disputes over reputation.
Feedback Mechanism:
- The protocol can incorporate feedback loops, allowing users to provide input on each other's behavior based on established criteria. This can be integrated into reputation calculations, contributing to a more engaging and responsive governance environment.
Building a Web of Trust:
- The Hats Protocol supports the development of social trust networks. Users could earn reputation by interacting positively within their network, which can amplify their credibility across the larger community.
Considerations for Implementation
While the Hats Protocol presents numerous benefits, there are important considerations for its implementation:
User Education:
- Educate users on how the Hats Protocol works, the significance of the hats system, and the nature of its impact on reputation and governance. Clear guidelines will foster acceptance and engagement.
Preventing Hat Abuse:
- Implement measures to prevent users from undermining the system through collusion or by gaming the reputation. Robust algorithms should be in place to detect unusual behavior patterns.
Balancing Autonomy and Accountability:
- Allow users the autonomy to engage with the hat system but balance it with accountability mechanisms that ensure responsible behavior.
Inclusivity and Accessibility:
- Ensure that the Hats Protocol is designed to be inclusive, considering diverse user backgrounds and accessibility needs. This can help create an environment where every voice is valued.
Integration with Existing Systems:
- If the community already has a governance or reputation framework, ensure the Hats Protocol complements or enhances existing structures, rather than creating fragmentation or confusion.
Conclusion
The Hats Protocol can play a pivotal role in building a reputation and governance system that enhances community engagement, trust, and accountability. By leveraging its decentralized identity capabilities and customizable reputation elements, communities can cultivate a vibrant and responsible environment. Careful planning and consideration of user needs are essential to effectively implement the Hats Protocol in conjunction with other mechanisms like knowledge tests and feedback systems, resulting in a comprehensive and dynamic governance framework.
i'll leave it at that for now as this post has become quite long, to say the least. Please feel free to comment / ask questions below.
Sat Nam
Atma

Something else occurred to me. Cryptocurrencies like Dero and Monero are able to maintain an accounting ledger without revealing the accounting data. This mechanism is called Zero Knowledge Proofs. What occurred to me is that PII like biometric data can be used to create a hash of that data, and be used by the Human verification system to confirm an actual and unique human being is using a specific account. This hash can be stored on a decentralized blockchain and can prevent that specific unique human from creating new accounts. By this means both bots and socks can be excludedd.
Thanks!
Indeed. i prefer Zano to both of those though, with perhaps #Firo and #EpicCash as close runners up.
https://peakd.com/@atma.love/re-peaksnaps-so1n3x