What is an Information Security Assurance?

Information security assurance is the management and protection of knowledge, information, and data.Components Information Security Assurance?
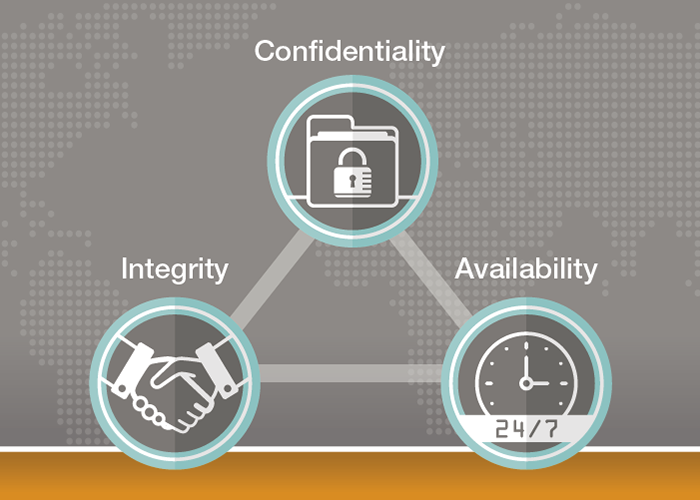
The basic components of information security are most often summed up by the so-called CIA triad: confidentiality, integrity, and availability. Confidentiality is perhaps the element of the triad that most immediately comes to mind when you think of information security.Differentiate the certification programs to Common body language?
Certification programs
are designed to give students mastery over a narrow subject area or topic. These programs are offered in many trades, professional fields, and academic areas and are available at both the undergraduate and graduate levels.
Common body language

is the gestures, movements, and mannerisms by which a person or animal communicates with others.
4.Differentiate the Governance and Risk management?
Governance

is concerned with structure and processes for decision making, accountability, control and behavior at the top of an entity.
Risk management

allows organizations to attempt to prepare for the unexpected by minimizing risks and extra costs before they happen.
5.Different between Security Architecture to Design?
Security architecture
is a unified security design that addresses the necessities and potential risks involved in a certain scenario or environment.
Design

is a visual look or a shape given to a certain object, in order to make it more attractive, make it more comfortable or to improve another characteristic.
6.Different between Business Continuity Planning to D-i-s-a-s-t-e-r Recovery Planning?
Business Continuity Planning

is the process involved in creating a system of prevention and recovery from potential threats to a company.
Disaster Recovery Planning
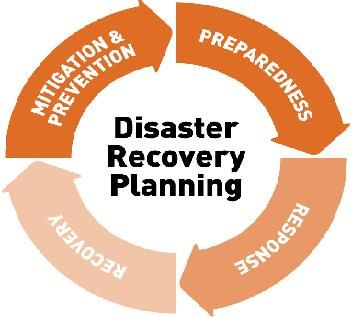
is a formal document created by an organization that contains detailed instructions on how to respond to unplanned incidents.
7.What is Physical Security Control?

Physical security is the protection of personnel, hardware, software, networks and data from physical actions and events that could cause serious loss or damage.
Examples of physical controls are: Closed-circuit surveillance cameras. Motion or thermal alarm systems. Security guards. Picture IDs. Locked and dead-bolted steel doors. Biometrics (includes fingerprint, voice, face, iris, handwriting, and other automated methods used to recognize individuals)
8.What is Operations Security?

Operations security concerns the security of systems and data while being actively used in a production environment.
9.What is Law?

Law is a rule of conduct developed by the government or society over a certain territory. Law follows certain practices and customs in order to deal with crime, business, social relationships, property, finance, etc. The Law is controlled and enforced by the controlling authority.
10.What is Investigation?

The idea of an active effort to find out something. An investigation is a systematic, minute, and thorough attempt to learn the facts about something complex or hidden.
11.What is Ethics?

Ethics is a system of moral principles. Ethics is concerned with what is good for individuals and society and is also described as moral philosophy.
12.What is Information Security?

(Technical controls) use software and data to monitor and control access to information and computing systems. Passwords, network and host-based firewalls, network intrusion detection systems, access control lists, and data encryption are examples of logical controls.
(photos are not mine, and some thoughts and idea shown are base and from google)
Hello, @francisd2nd
Keeping Up With the Buzz – My Introduction to the Hive Community.This is @fionasfavourites from the @ocd (Original Content Decentralized) curation team. We noticed you shared your first post here on Hive - congratulations and welcome! It would also be awesome if you could do an introduction post, so our community can get to know you better. For an example of what an intro post is like, you can check out this one by my friend & curation team member -
Speaking of community, we have many different ones here on the blockchain, devoted to all kinds of interests. Here's a link so you can check them all out – Hive Communities.
Also since you're new, you may run into an RC (Resource Credits) error when trying to comment/post because you don't yet have enough Hive in your account yet. For assistance with a temporary delegation to get you started, be sure to check out the Gift Giver site.
Also, as this the hive can be quite confusing, the newly launched Newbies Guide is a growing repository of useful – easy to understand – posts about how the Hive ecosystem works.
OCD Discord server if you have any questions!For now, @lovesniper will follow your account and we are looking forward to seeing your intro post. Also, you are welcome to tag me (@fionasfavourites) and please mention @lovesniper in your intro post in order for us to be notified, so we can consider your post for OCD curation. Feel free to hop into the