
Greetings
Today, I would like to share my current work in progress for the MonsterCards.store market with you.
I also want to address concerns about the security of my market and other markets, as well as share my experience with an unsuccessful marketing campaign I ran in the past.
Market status
Currently, I am working on the assets market, which will look like this:
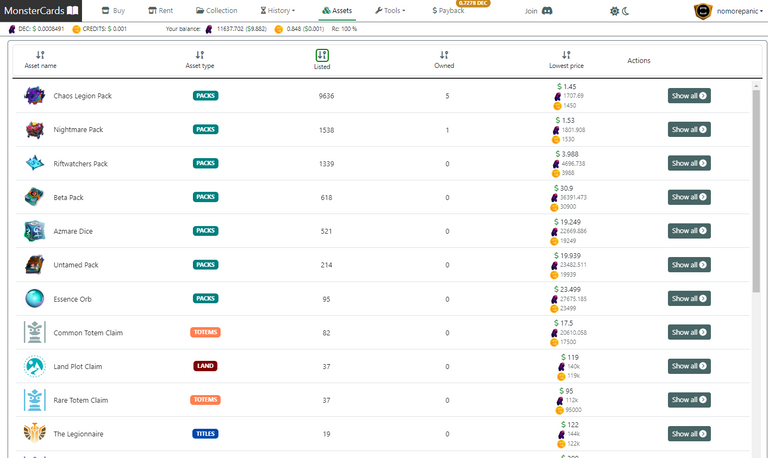
Assets will have their own purchase history and will be part of a 75% payback system.
Listing on Splinterlands.com
I'm excited to inform you that the monstercards.store market will be listed on Splinterlands.com in the near future. You can indirectly verify this information on the Splinterlands Discord:
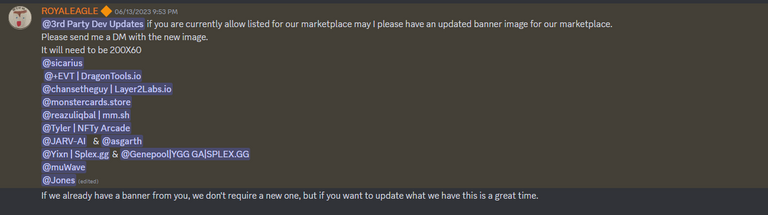
https://discord.com/channels/447924793048825866/567729128900526120/1118266815655714968
Please note that the listing process may take some time, so please be patient.
Few words about security and an unhappy marketing campaign
Before discussing security, I'd like to share a story about a marketing campaign I devised.
Marketing campaign
The main goal of this campaign was to attract new players to my market, as I believe it would be beneficial for them.
The challenge was how to reach them effectively. Traditional advertising campaigns on dedicated portals or Peaked could be expensive, and the conversion rates were uncertain.
So, I came up with an alternative approach: I developed a service on my backend site that would send a small portion of SPS (0.001 to be precise) to users.
The idea was that users would receive a message about the SPS transfer from the user "visit-slmc.store":
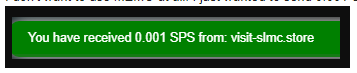
In this case, "visit-slmc.store" is a valid domain name that I own, and visiting that address redirects users to my market.
After analyzing the Terms of Service and confirming with support, I determined that this action was not prohibited.
This method only worked if users were active at the time the SPS transfer arrived (assuming most users do not analyze their SPS transfer history for no reason).
My service would grab the latest transaction block from the Splinterlands API (transactions/history?from_block=-1&limit=1) every few minutes (to conserve RC) and extract the player name from the last battle returned.
This way, I assumed that users had been active in the past few minutes and potentially still were.
Marketing campaign - results
The number of users visiting my market increased, but...
Almost all users were hesitant to use the market due to the unconventional nature of the marketing campaign and the prevalent occurrence of hacking attacks in the crypto world.
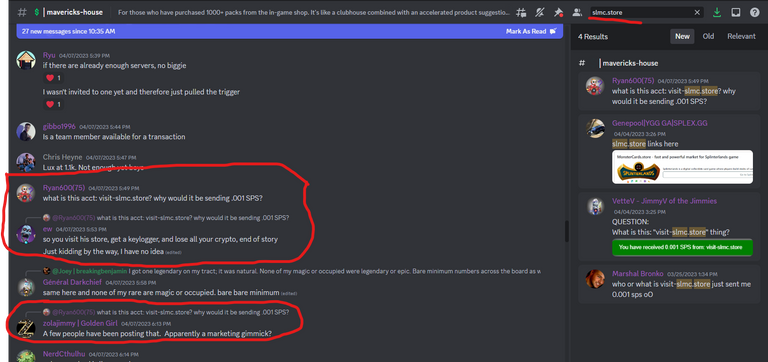
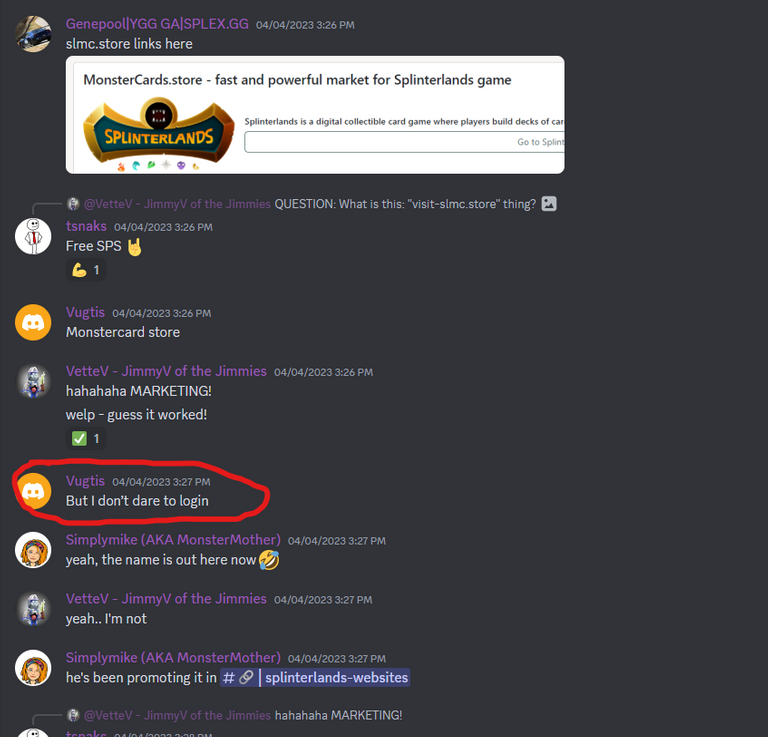
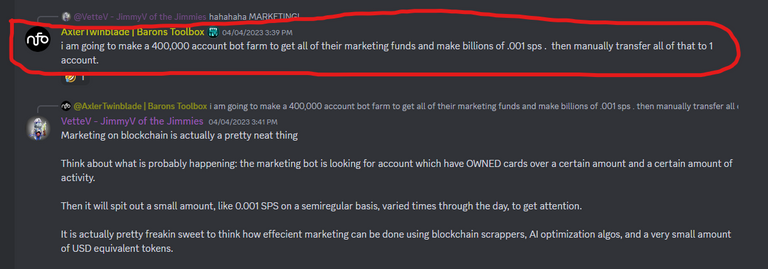
Sorry @axlertwinblade, that won't work because I sent transactions only every dozen minutes😉
Marketing campaign - conclusion
In conclusion, my marketing campaign created a lot of buzz in the community, but unfortunately, it turned out to be negative attention.
As someone who is not a marketer, I did not anticipate such a result. I implemented the marketing campaign because I was frustrated with the low traffic on the market, which was costing me significant time and money.
I acted impatiently and made a poor decision.
As a result, I have decided to suspend this marketing campaign for now.
Security concerns
The positive aspect is that many users, such as @vugtis from the Discord screen, are vigilant and cautious. That's commendable.
It is always better to avoid clicking on suspicious links if any doubts arise.
To redeem myself, I would like to discuss security in the context of the Splinterlands & Hive ecosystem.
Most common types of attacks in web applications
Phising - common case
Phishing is a cyber attack where individuals are tricked into revealing sensitive information or performing actions by impersonating a trusted entity.
Here's an example of how a phishing attack may appear:
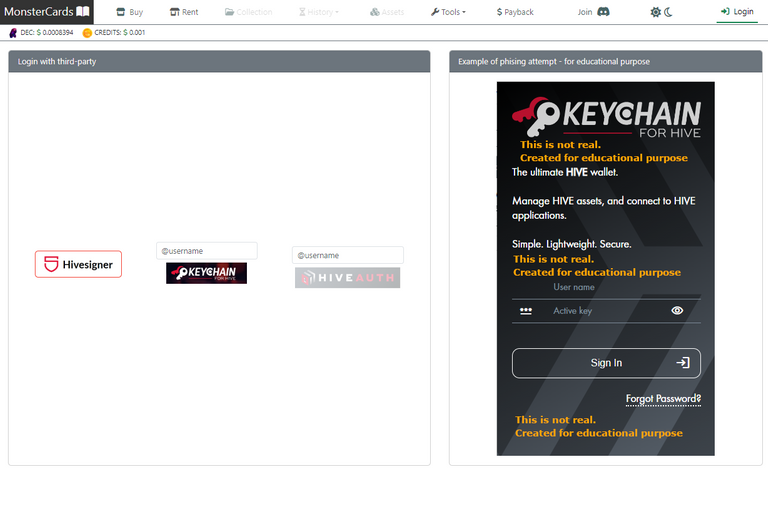
I created this example in just 5 minutes on my local machine during development, but it demonstrates the common sense behind a phishing attack.
Normally, when you log in to any website that uses Hive Keychain, the extension window appears for you to log in. In my example, I displayed a form that closely resembles the original extension and asks for the user's name and active key.
This is a basic example, and it took me longer to describe it than to prepare it. It is even possible to create an example where I open the exact same window as the Keychain browser extension in a separate window, but that would require more time.
If you have any doubts, it is advisable to check the source of a pop-up window by right-clicking it and selecting the "Inspect" option:
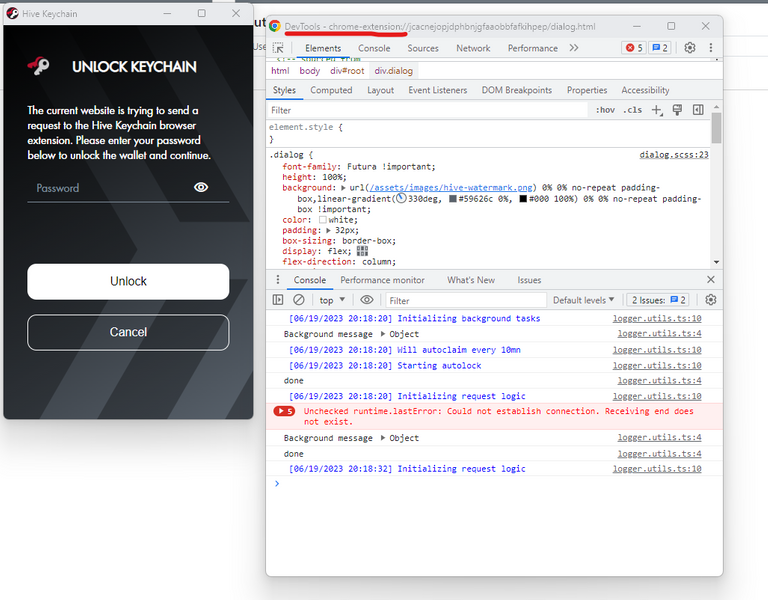
In this case, it comes from the Chrome extension, so it is legitimate. However, you must ensure that you have installed the browser extension from an official and legitimate source. If you see other domains, you should steer clear of them.
Phising - user input logging
Essentially, you should assume that developers (and hackers) can capture every input you make on websites they control. This includes every keypress, mouse movement, and mouse click.
You can try this out yourself with minimal technical skills. Go to any website that contains an input field, such as google.com, press F12 to open the developer tools, and switch to the "Console" tab. Type in the following code and press Enter:
document.addEventListener('keydown', function(event) {
console.log("Key pressed: " + event.key);
});
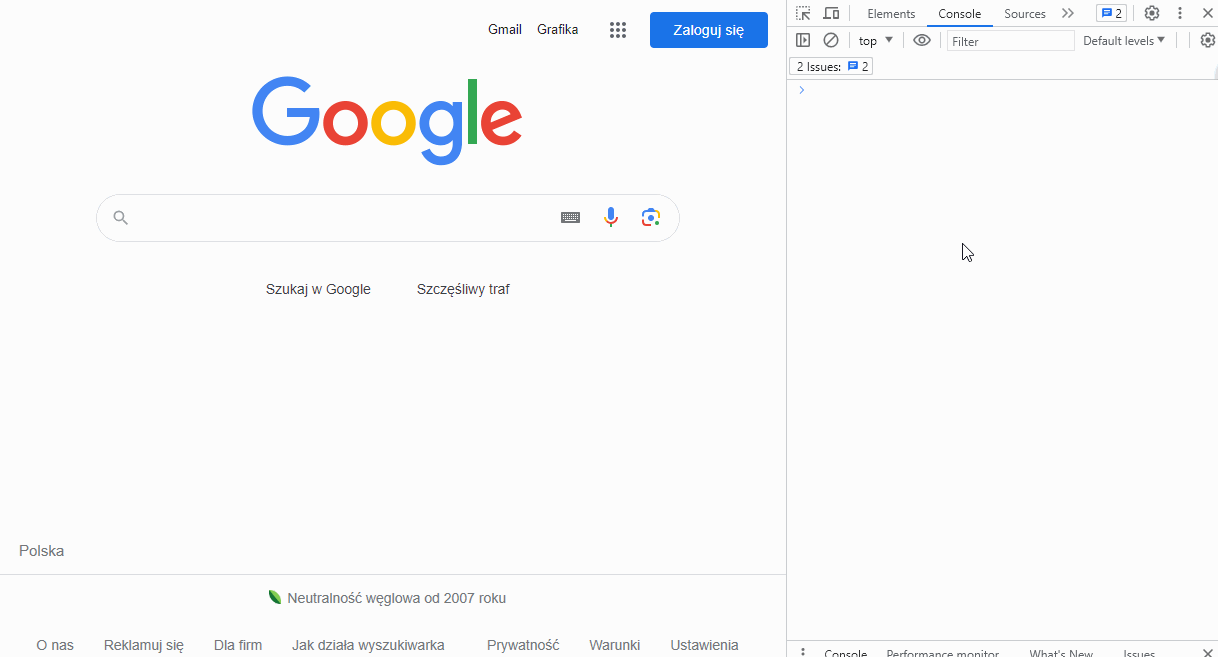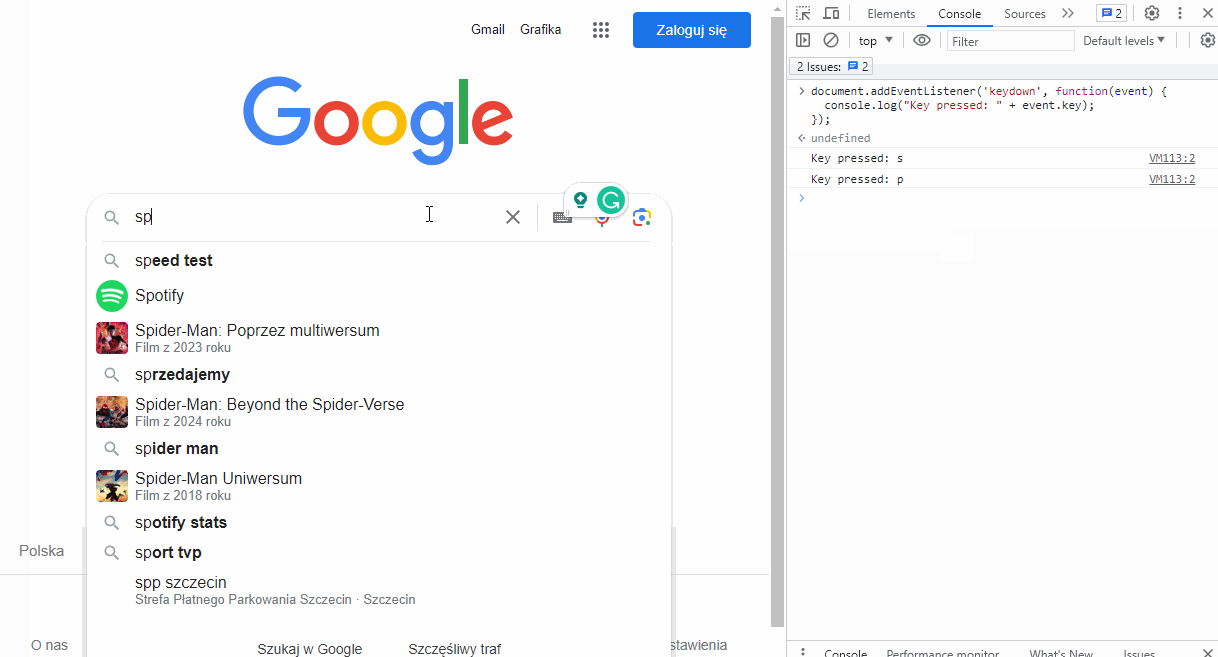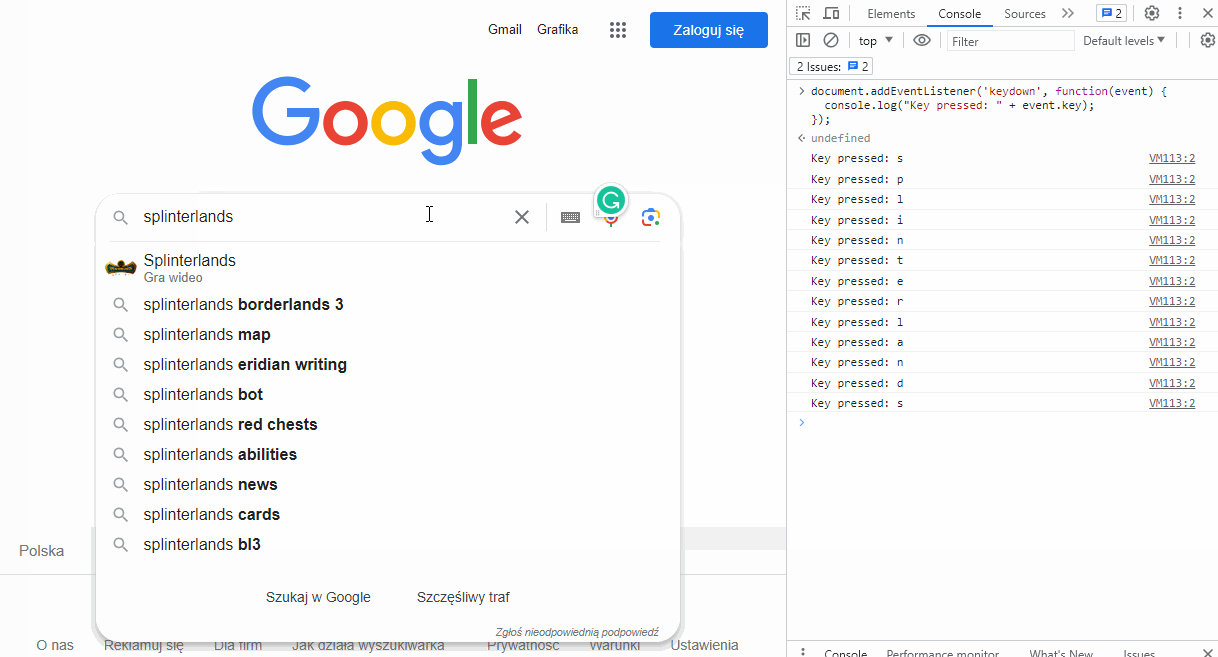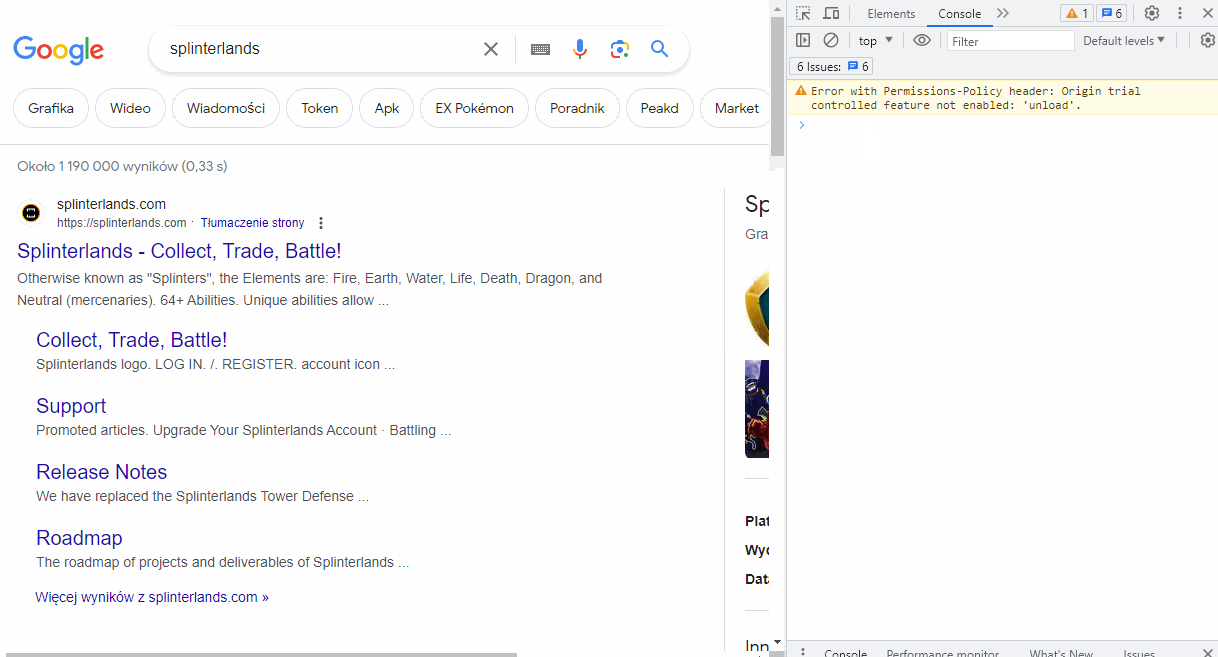
From now on, every key you press will be logged in the console. This example will only work for the lifetime of your open tab and only in your browser. However, any developer can implement the same code in an application script, making it work for all users of that application. This is how phishing pages can capture your logins and passwords.
It is especially dangerous if you use the same login/email and password on multiple websites. An attacker can write a script to attempt logging in with the same credentials on numerous websites or applications.
To ensure your security, always use different passwords for each website you need to log in to. I recommend using a password manager application for this purpose.
HiveKeychain, HiveAuth - how they protect users
Hive Keychain is a browser extension, and HiveAuth is a separate application. They are not part of any website. Websites can utilize them by implementing the methods defined by the developers of Hive Keychain and HiveAuth.
Importantly, websites do not receive information about every action performed by a user in the Hive Keychain browser extension or HiveAuth application.
You can verify this in the same way we did before. You can even go to MonsterCards.store market:
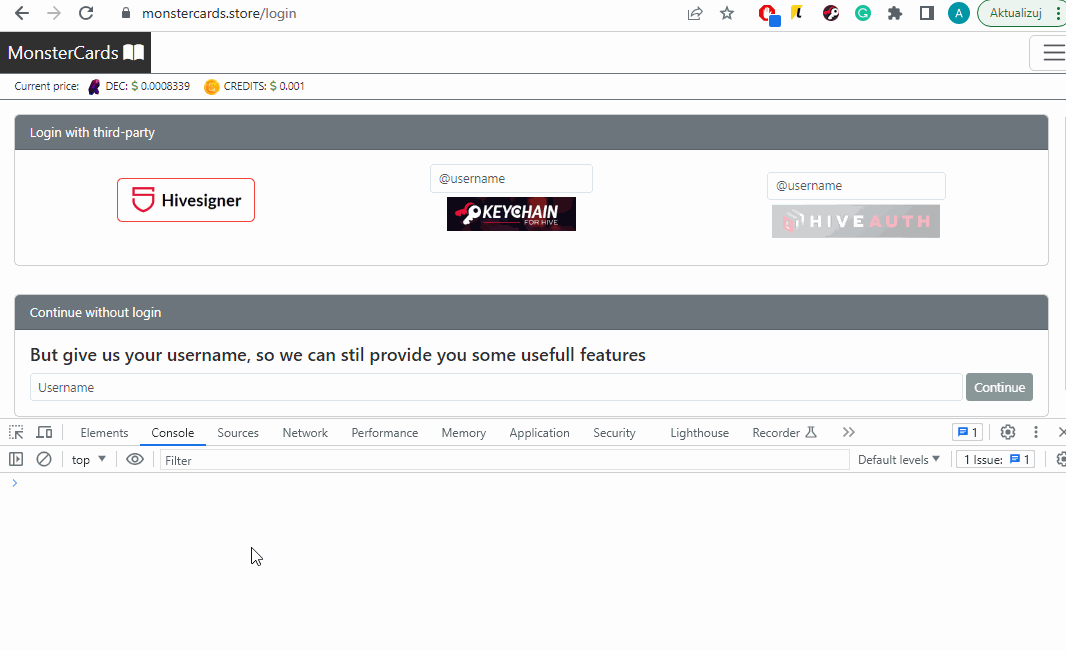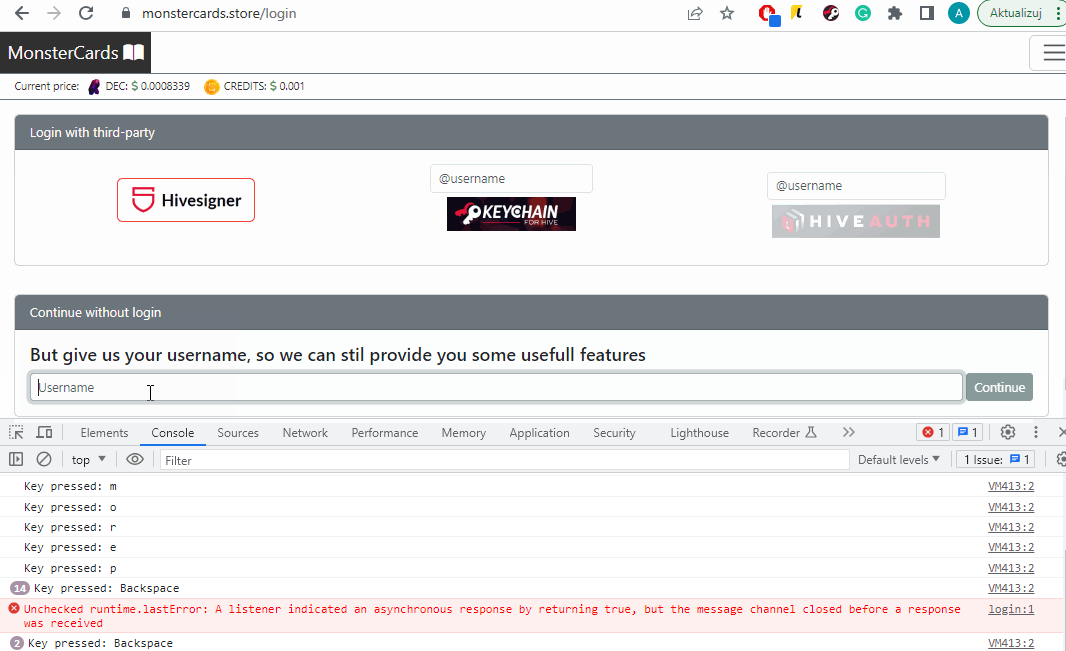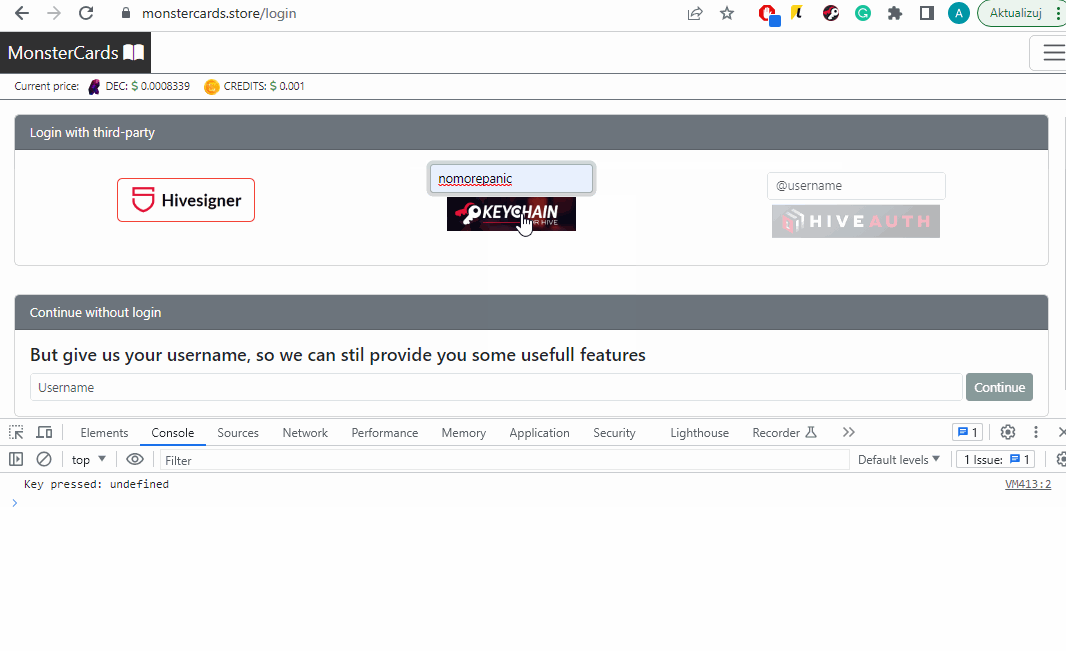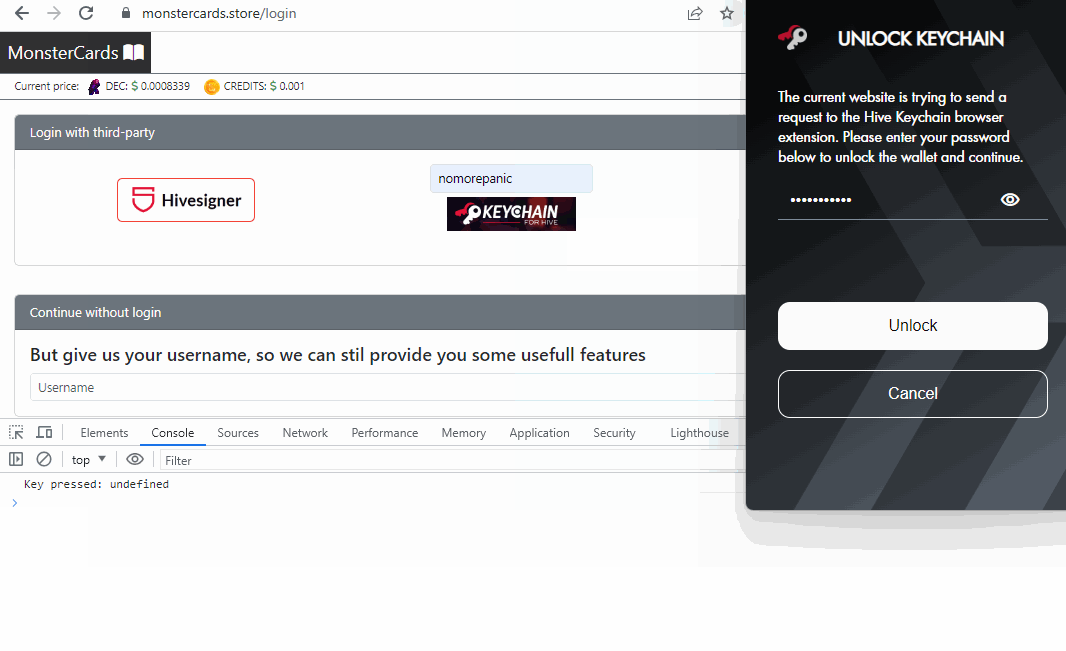
As you can see, when I type something into the inputs belonging to the browser extension, my application does not capture it.
A similar effect occurs with HiveAuth:
I only receive information about whether the requested username was authorized or not.
When you use the market, for example, when you want to buy a card, my application informs Hive Keychain or HiveAuth that a specific username wants to perform a specific transaction with specific items. The extension's role is to send the transaction to the Hive ecosystem. The extension will prompt the user with transaction details for permission. My market only receives information about whether the transaction was sent or not.
My market or any other application that uses Hive Keychain or HiveAuth does not have access to your Hive keys, and you should never provide your keys to any website unless you are absolutely certain you know what you are doing.
Drive-by-download attack
A drive-by-download attack is a type of cyber attack that automatically downloads malicious software onto a victim's device when they visit a compromised website, often without their knowledge or consent.
Attackers exploit well-known vulnerabilities or discover new ones in browsers or operating systems. That's why it's important to always update your system and applications (including browsers) because as soon as any exploit or potential security flaw is discovered, it is patched to prevent such attacks.
This type of attack is less common than phishing because it requires greater technical skills and is more time-dependent.
However, it's still important to stay vigilant when encountering websites that offer applications promising amazing boosts or rewards if you download and run their suspicious executable files, such as "superMegaSplinterlandsBooster.exe."
Data leaks
Even when using legitimate applications, it's important to recognize that no system is completely immune to data leaks. Major players in the industry have experienced instances where user information, such as emails, logins, or even passwords stored in plaintext, have been compromised.
I strongly recommend monitoring your email addresses using the website https://haveibeenpwned.com/ to check if your information has been involved in any data breaches.
MonsterCards.store is safe in this area, because I store only the usernames, which are already publically well known.
Conclusion
It's important to note that this discussion doesn't cover all possible security issues, as the topic is extensive and complex. However, I hope to have provided you with some essential insights.
Remember, most of the time, the weakest link in security is the human factor. Stay cautious, follow best practices, and remain informed about the latest threats.
If you found this topic interesting, I encourage you to reblog this post if possible. If you have any questions or need further explanations, feel free to leave a comment.
Sorry the marketing campaign didn't work out. I notice your payback is 75% of market fee. That's a lot better than everyone else, I think.
It was my fault. I was too impatient. As far as I know, my payback is the greatest one at the moment.
Remember that a referral program also allows you to earn an extra 5% of referred users.
Feel free to visit monstercards.store