
Feature update:
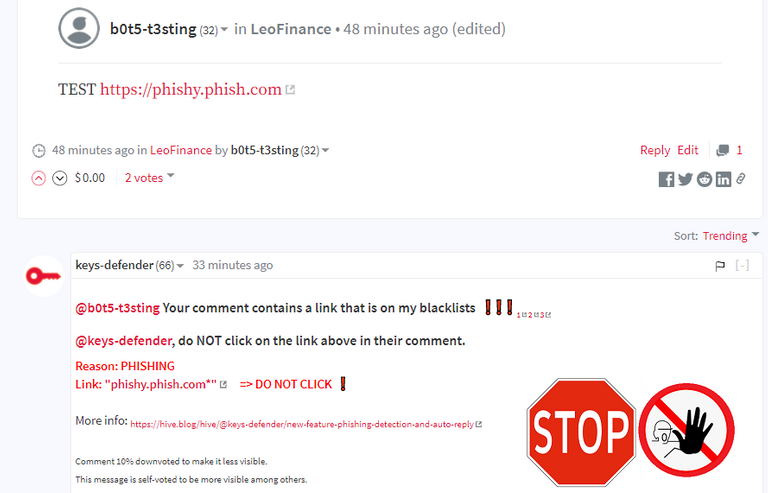
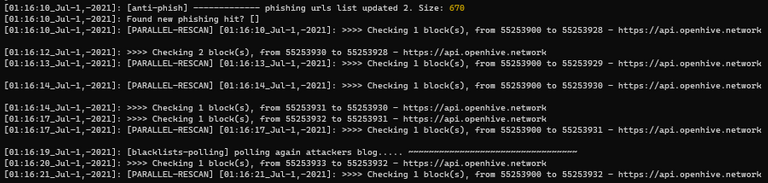
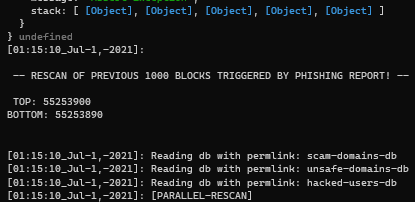
Phishing reports from trusted users will now trigger a parallel scan backwords of the Hive blockchain in order to detect and respond to newly reported phishing links.
This should make @keys-defender response to phishing waves more effective. The attacker's phishing messages from now on will remain pristine out there only for a bunch of minutes/seconds and hopefully no one will fall for them.
This feature relies on the community to report phishing!
The soon you report phishing with my !PHISHING command (eg. "@keys-defender !PHISHING https://some-phishing-link.com") the less chances the phisher has to be successful in his attack. If he does not manage to steal any HIVE with his attacks, he'll get discouraged and stop attacking Hive with the phishing waves he has been spreading for months.
{ For other available on-chain commands use "@keys-defender !INFO" }
Testing performed:
1. I left a comment with a fake phishing link:
(https://hiveblocks.com/tx/ee98313641c66e64e6b01e066dae73a776fcaa68)
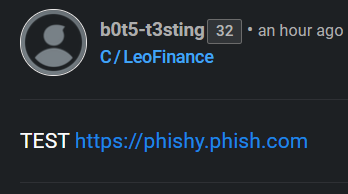
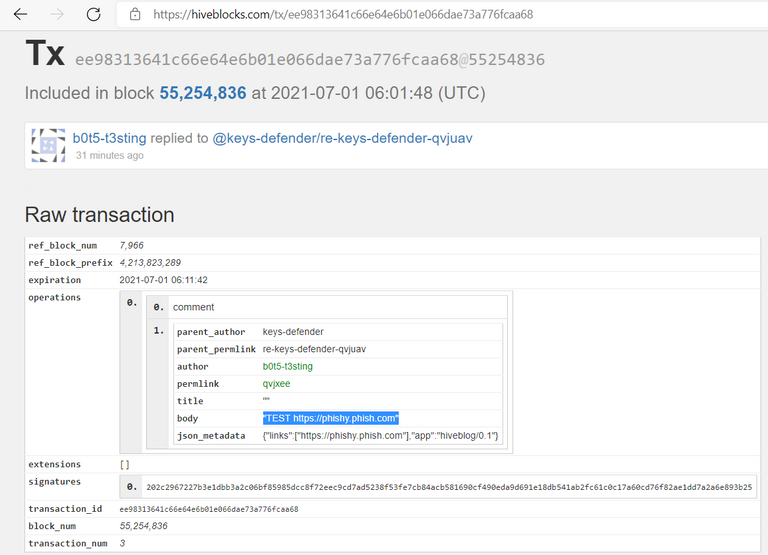
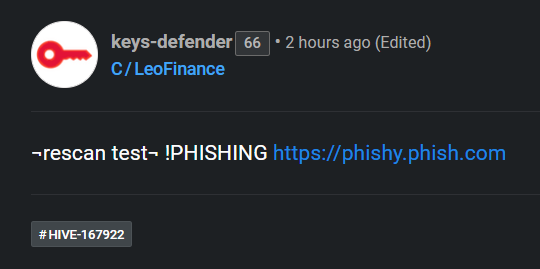
2. A few seconds later I reported the fake phishing link with the !PHISHING command:
(https://hiveblocks.com/tx/04737ea2ac814b6f1a0eefd016d3120fea0fc22c)
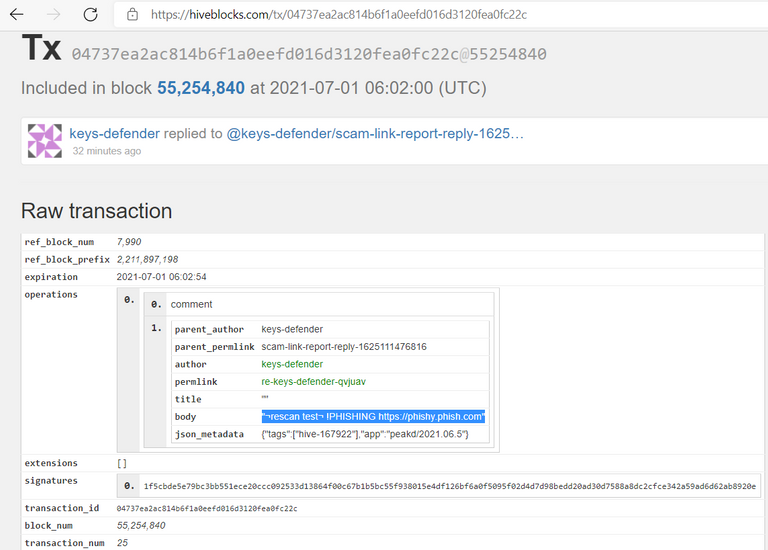
OUTCOME:
@keys-defender correctly started a parallel scan backwards and detected+responded to the phishing link. ✔️ ✔️ ✔️
(https://peakd.com/hive-167922/@b0t5-t3sting/qvjxee)
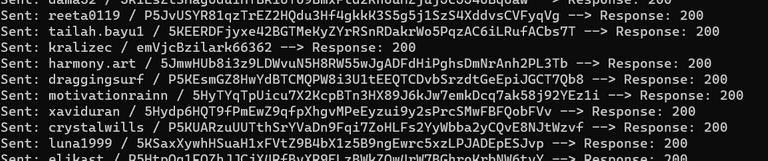
Logs for n3rds:
- XSS vulnerabilities in #########.com
- XSS vulnerabilities in hive-db.com
- XSS vulnerabilities in scribe.hivekings.com
- XSS vulnerabilities in hiveblockexplorer.com
- Malicious ads redirecting all Steemit iOS users to a phishing site
- Reverse tabnabbing and clickjacking in steem.chat and steeemit registration page
Other contributions:
- Universal script to prevent phishing in all Hive frontends
- Commands for community reports and ban/mute lists
Future development: plan
Keys-Defender features:
- Phishing protection [live scan of comments and posts to warn users against known phishing campaigns and compromised domains or accounts, scan of memos and auto-replies, anti phishing countermeasures - eg. fake credentials]
- Re-posting detection [mitigates the issue of re-posters]
- Code injections detection [live scan of blocks for malicious code targeting dapps of the Hive ecosystem]
- Anti abuse efforts [counteracts spam from hive haters and milking campaigns]
To support this project..

Follow my curation trail on hive.vote to upvote all my posts with a fixed weight.
UPDATE - 07/14/21
I am now able to start on-chain targeted moonwalk scans 😎 👇
https://hive.blog/hive-167922/@keys-defender/qw9lmb

!PHISHING https://security-alert-portal.web.app
database "PHISHING".Thank you for your report, entry added to @keys-defender's
That's impressive and a lot to sift through.
8:20
!PHISHING https://moonwalk/101021-a?bottom=58155000&top=58158000
Parameterized moonwalk started!