
In this post I would like to bring together my thoughts, which I have made today during the whole day. Today I was thinking about how to improve the security of each user on Hive. Right now there are always ongoing phishing attacks here on Hive. So I am very sorry that a German speaking member of the community has become a victim of such a phishing/scam attack this morning.
Since many months it is always the same approach of the attacker. A website is set up, in front of you is pretended that you can quickly pick up your airdrop or something similar. A fake version of the HiveSigner tool is used, where the data is not compared with the blockchain in the background, but the entries end up in plain text in the attacker's database. Once you have entered your data there, things then move very quickly. The account is changed on the Steem Chain as well as in our case on Hive. In most cases, a new password is immediately set for the account, all liquid funds are sent out and a power-down is initiated. If you have "only" entered your active key, then at least something can still be saved. An account recovery is appropriate here. But if the victim still has his recovery account on "steem", it's over. As we know, Justin Sun or someone from Steem will not bother to perform an account recovery for Hive users.
All this is repeated because the attacker / phisher now has a larger collection of "real" accounts in his control. Conversely, this means that the attacker uses the newly gained accounts to write more phishing comments on the blockchain and thus the whole thing takes on ever greater proportions.
And this is where I started to think about how to provide at least a little more security for the Hive community.
My idea for more security
When the phisher / attacker uses his unauthorized obtained accounts to post comments, they are mostly posted under articles that are inside a community. As an administrator / moderator of a community, there is the possibility to manually put certain accounts on the "mute" list.
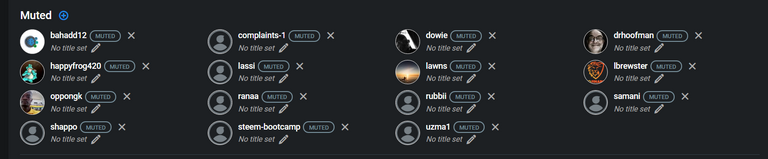
Current mute list of the german speaking community @hive-121566
This function is great for hiding troublemakers, inappropriate content or even phishing within the community. This is not censored, but simply hidden. And that's fine!
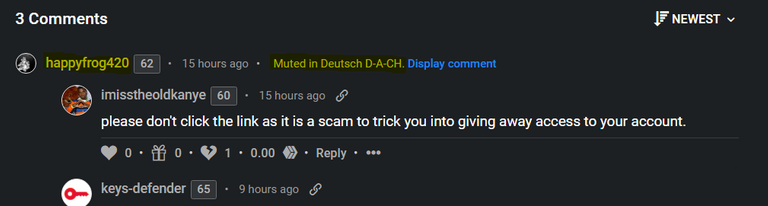
You always have the possibility to view the comment by clicking on "Display comment". The comment from @happyfrog420 was automatically hidden after I put the user on the mute list of our community.
The user who got hit this morning.... @drhoofman I have now also put on the "Mute" list as a precaution. I know that the attacker has full control over the account and will soon post more phishing comments with @drhoofman's account.
@keys-defender and lists of known phishing accounts.
There is a great effort thanks to @keys-defender and some other great people to act quickly and efficiently against such phishing attacks. On our Discord, where all necessary information about currently ongoing phishing attacks and new phishing waves are gathered, we coordinate together how to act efficiently and targeted against the phishing attacks. Questions will be answered very quickly!
And here comes a part of the solution to the problem we have.
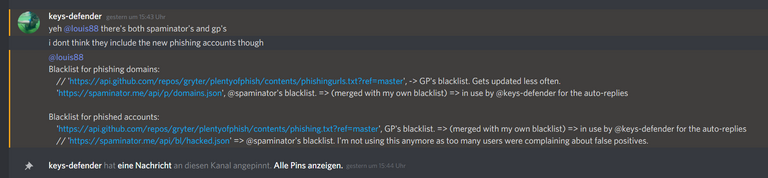
Thanks for the quick and detailed answer @keys-defender! For now, I am only interested in one specific list. And that is the list of account names that are potentially at risk of writing more phishing content to the blockchain. These are primarily the accounts that "stupidly" entered their passwords on the phishing site and then, as a potential phishing victim, spread the shit on the blockchain. I assume that this list is by far the most current list of such hive accounts:
https://raw.githubusercontent.com/gryter/plentyofphish/master/phishing.txt
A list - And the responsibility the own community - The solution?
Now that we have a very large list of Hive account names that are known to post malicious content to the communities, it's time to take a big step. Now I don't know much technically about the new blacklist and personal mute lists on Hive that are being developed (@blocktrades, @howo) but there must be a way to use this list for your own community. I don't want to manually add every single person on the list to my community, but I want the mute list to expand automatically as soon as "unfortunately" someone new falls for the phishing crap and presents as a clear danger to others.
Suggested solution 1
I, as the community leader and owner of the community's account with owner privileges, could give an account the Posting Permission or Active Permission to manage my community's "mute list" from the outside. Of course, this requires great trust in a service that handles this power very carefully and professionally. As an example, you could give the account "@keys-defender" the rights to manage the mute list within my community to make sure that new accounts distributing phishing are directly muted in the community.
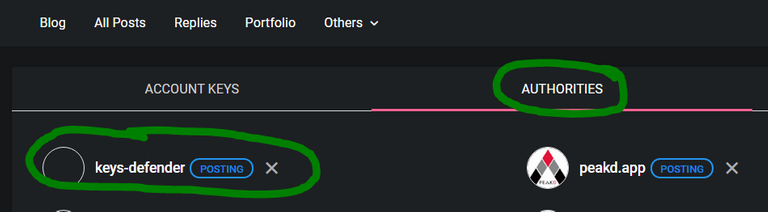
Proof of Concept
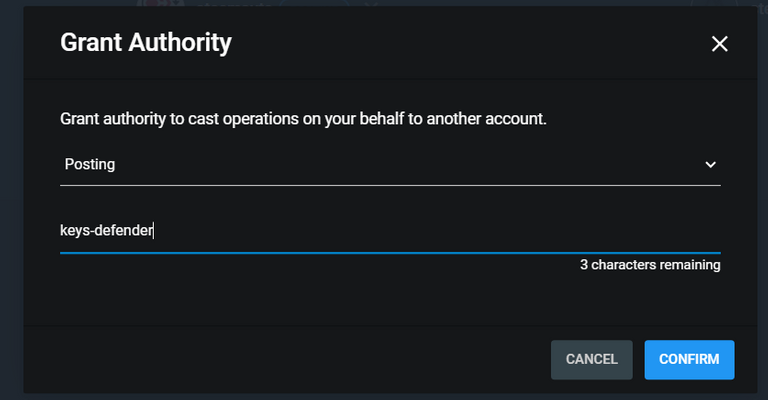
Proof of Concept
Suggested solution 2
In the settings e.g. at PeakD or Hive.Blog in the administration of the community there is a check box that the administrator of a community can activate and thus automatically set the list of known phishing accounts to mute.
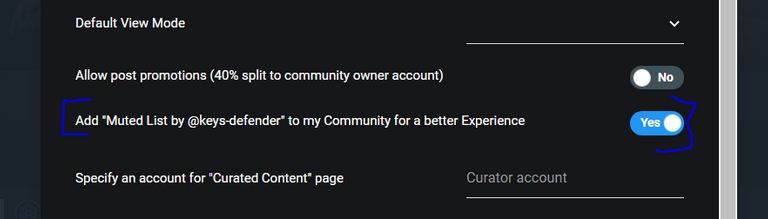
Proof of Concept
First and foremost, I want there to be a central place that each community can activate or not when needed. It is ultimately up to each community owner if they want to take this step. I think it only makes sense if there is such an extension for the experience within a community to a) make the user experience as good as possible b) improve the security of the users on Hive.
A call to the community leaders!
I'm calling you - community leaders of the most used communities on Hive! Do you want to fight phishing and scam? Please leave me your feedback in the comments on these suggested solutions and let's discuss if this is a way to stop the phishing shit on Hive.
Leofinance Community: @khaleelkazi @leofinance
Gems Community: @bluemist
HIVE CN 中文社区 Community: @sweetsssj
Foodies Bee Hive Community: @foodiesbeehive @foodiesunite
Hive Gaming Community: @hivegc @strawhat @acidyo
Haveyoubeenhere Community: @martibis
Photography Lovers Community: @derangedvisions
Nerday Community: @nerday.com @nerday
Project HOPE Community:@project.hope @juanmolina @crypto.piotr
OCD Community: @acidyo
Hive Book Club Community: @macchiata
OnChainArt Community: @midlet
DTube Community: @dtube
Actifit Community: @mcfarhat
Threespeak Community: @theycallmedan @starkerz @threespeak @sisygoboom
Cervantes Community: @cervantes
Thank you very much. I look forward to construtive feedback on those ideas I had.
Peace ✌️
louis
Thanks for giving this important issue a thought, Louis!
I already offered a solution that should quickly mitigate this issue: my universal script for hive frontends. It just needs a bit more work to use multiple banlists (easy) and to allow frontends to let their users remove one/all banlists so that they still have a choice (easy).
The same applies for phished users, as mentioned in my “universal script” post, I was already planning on allowing all hive frontends to block all links from users added to the phished accounts list or at least display a prompt/confirmation/warning).
I think that the problem we currently have is that phished accounts are not added quickly enough to spaminator (if they were, any comment of theirs would already get my dedicated auto-reply). Only one/two people have access to those blacklists. I was offered access but replied that I prefer having my own in order to improve decentralization and allow adoption/acceptance of my solution.
I was also thinking that I should start supporting a "!hacked" command (and its related list) to let trusted users put accounts into my own phished accounts list (and a "!recovered "command to remove them if necessary - important too for recoveries).
Phishing campaigns quite often are detected early by my bot (happened at least 3 times in the past couple months).
(Furthermore for this attacker I now have in place a way to detect waves even earlier. PS. this was effective in preventing last night's wave as soon as it started!)
What sometimes happen is that the attacker tests an automated comment on a previously phished user and that triggers an early notification into my discord server. In order to have someone react in a timely matter, more trusted users should be in my discord or more discord servers owners should allow my bot to post warnings in a dedicated channel in their discord server. In this way, the reputation of irremediably lost accounts controlled by the attacker could be nuked early so that all their messages would get hidden by default.
my universal script for hive frontends - unfortunately only adopted by 5 frontends so far..).blacklisting users: I could automate adding to my mute list any new user added to @spaminator’s list, if that helps. Maybe the !hacked command is a better approach though - my bot already replies to any comment (with at least one link) left by a user marked as hacked in @guiltyparties’s GitHub. I do not think that the approach you suggested is good enough because the attacker switches to a new phished account as soon as they notice it’s being counteracted. That still happens during phishing waves even though filling their database with fake credentials using a script (like I do during every wave) seems to slow them down a lot. Blacklisted users then also need to be removed if they recover. IMO blacklisting phishing domains is more effective (and that’s why I started with that in
I already have on my backlog to start supporting “!scam” commands -> my universal script for hive frontends will show an alert saying “the Hive community classified this link as SCAM, are you sure you want to proceed??” (works in any Hive frontend, it’s just a prompt() command supported in every browser).
( we should train new users with simple rules: never ever use your master key on a new website you just found out about. Leave your funds either powered up or in savings.)
“I want the mute list to expand automatically as soon as someone new falls for the phishing crap” - the issue is that if the account is then recovered it requires a manual removal. I think that at the moment only fully lost accounts indeed end up on @spaminator’s hacked accounts list and that makes my auto-replies less effective for that scenario.
Suggested solution 1 - “ give an account the Posting Permission or Active Permission to manage my community's mute list from the outside” - this could work and additions to each community mute list could be automated as soon as a new phishing link is detected by @k.d., but every existing and future community would have to do it and that's not guaranteed to happen, leaving some users still unprotected. +
Suggested solution 2 - all community leaders would have to do it (and maybe some changes are required by the core dev team too?) so same, it may not be effective.
--> Blocking all known phishing domains in all frontends (including Hive chat) with my universal script is more feasible and effective IMO.
In the meantime... the attacker is testing 2 new domains and my bot immediately detected them: https://hive.blog/@keys-defender/comments
Another improvement required: right after a phishing link is reported with the dedicated command, not only auto reply to new comments using it but also navigate back the blockchain to counteract previous comments (without having to re-run a script manually like i do now)
One important thing to add.
Lists being created by different projects should be named and separated
That would make us and our users more willing to use features like you proposed.. the big downfall of utility with many lists in the past is that the operators like @hivewatchers and @keys-defender and others seemingly put everyone onto one single jumbled up list instead of separating them... making their lists insanely less beneficial to other people and projects.
I will say this now I would not be happy with including features into peakd that use lists that are not specific in nature. If it's about fighting phishing make it that alone... if it's a list of spammers do that and see if users want to include that. If it's suspected reward pool abusers they need to not be in a list together with phishers.
But yes giving an automated account access to help a community with account moderation is a great idea we have thought the same thing to give community member labels or badges.
I’m already keeping lists separate. I currently have a phishing domains list and, as per comments on my “universal script” post, I will also offer a separate list for scam domains.
I also believe that banning domains rather than accounts is more effective. 1. Because phishers during their attacks create/steal/use multiple accounts and 2. because phished accounts can be recovered and would require removal from blacklists, phishing domains don't.
(I am in the middle of replying to this post too - long reply and it’s difficult to re-word on my phone [newborn asleeep])
Awesome very happy to hear this!!
Also you may be correct for phishing links however communities still do not want the offending spammy links inside of the communities so I assume they would love a sort of automated and trusted system they could choose to use to moderate them out of their communities
That's why in my Universal Script post I also mentioned that I would do something similar for phished accounts (ie. when users click a link in a comment from a known phished account, it will warn them with a prompt - in all Hive frontends that integrate my script).
FYI: I released them this week -> https://hive.blog/hive-169321/@keys-defender/new-commands-and-ban-lists
How about blacklisting the affected accounts via API? That should be a good way to contain the crap.
3speak has implemented the keys-defender script.
Good post, it's hard work, there is a lot of deception on the net and I think just as hackers get many ways to bypass controls, you can stay one step ahead of them with security.
It's a difficult problem and when there's a solution the hackers adjust. They will always do a few things because it's the same group: 1. use existing accounts to post comments or posts and trap more accounts 2. use links to phishing sites that work in a large number of ways (can be copy of condenser, can be submit info, can be hivesigner, etc).
The best response so far has been simply to call it "phishing" when it's seen and never call it anything else. Never call it spam or a scam. Clarity has been the most effective response because there's no maybe here. People know that phishing = never click. But where we have mixed terminology when warning users that's when we have problems as one person's scam is another person's business.
I think creating some sort of a centralized point of muting for all communities can make some sort of a dent in phishing. The problem is there are many non-community related posts/comments. I don't know if the amount of work this will require will necessarily get the results needed. So your idea can definitely help if implemented.
The hackers, like I said before, will adjust. Normally the hackers are well ahead of any company or responses. However, Hive is at the forefront of its tech segment itself and we can potentially neutralize most attacks by trying different options. One of our strongest cards is our flexibility.
Congratulations @louis88! You have completed the following achievement on the Hive blockchain and have been rewarded with new badge(s) :
Your next target is to reach 58000 upvotes.
You can view your badges on your board and compare yourself to others in the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPCheck out the last post from @hivebuzz:
Nice
From a users perspective... what if we just created an account recovery method that could quickly be implemented such as another key associated with the account that is ONLY used to recover an account once it’s lost? Seems to me that this might be a more direct way to nip this problem in the butt... but I also might be missing something as web security isn’t a specialty of mine. Still... I thought I would weigh in as the thought did occur to me. Thanks!
Thanks for posting. Critical thinking takes a moment to do but avoids a lot of pain into the future.
Wow exelente post. muy instructivo lo explayado, gracias por compartir.
👍👍