 source
source
Hello splinterlords and splinterladies, how are you today. Hacker are everywhere around the the world. They are looking for account to hack. We are the one that will prevent our blog, or any of our social media to be hacked by ensuring maximum security. Do whatever it takes to prevent your account from being hacked.i experienced it 2 years ago. It is painful and horrible experience.
In 2019, my Facebook account was hacked. I did not visit my Facebook for three days because of my tight activities and schedule. After three days that I have completed my work; I decided to visit my Facebook and it said, "you can no longer login" I contacted facebook help and followed all the procedures. I uploaded my ID and my picture. The account was recovered after 2 days. I was very happy despite that my Facebook account doesn't earn anything.
Today, I make sure that I activated two-way authentication; which will send otp to my phone number before login in to my email because I don't want to make the same mistake again, i don't want to experience such again.
The Following can prevent your account from being hacked
• Do not disclose your keys to anyone: your hive account 'master key' can do whatever private posting, memo, and active key can do. You should never give your master, posting and active key to any one to help you log in. Hive account is one of the most secured account I ever know. Therefore, if the attacker does not have access to your email, it will be very hard to bridges your account. That is the reason your email account has to be:
a. Multifactor authentication: this will enable you to enter certain code the moment you want to log in to your email. Multifactor authentication is One of the app that is very easy to use. Certain code will be generating which you will need to open your email. The only way someone can log in to your account is for that person to have your phone, password, username, and authentication app.two-factor authentication is highly secured and good.
b. Provide complex answers to security questions: Don't be surprised, attackers has knowledge of likely answers to some of the questions. You need to provide complex answers to some of the security questions which will make it difficult for attackers to guess easily. If you have been using one password for most of the account you have, you need to change some of it because there are apps that generating password to the owners, of which they used to hack other accounts.
c. Use Strong Password: I also a victim of this sometimes ago, I used my surname as the password. That was the password I used for my Facebook account before it was hacked. The attacker log into my account, change my email and continued using it for few days before I got it back. Therefore, make sure to provide strong password, let you password contain letters, numbers and special characters. This will make it difficult for attackers to attack easily.
Be sensitive while login your account in someone else PC or phones: I will advice you not to login to someone PC or phones. A friend of mine made mistake because he was in haste to get the information sent to him by the company. He logged in into another person phone because his android phone was down. After he finished, he logged out but yet the phone stored the password. After few hours, he received a debit alert from his bank. he contacted the bank customer service and they said he's the one that make a transaction. He later remembered that he stored his credit card number in his email and used someone phone to access his email. 90% of his money were withdrawn.
No matter how urgency it may be, don't use someone PC or phones to access your hive account. Once someone have access to your hive account, such person can download other keys. As you know that your Hive key also access your splinterlands account; such attacker will have Opportunity to everything in your hive account.
OPPORTUNITY MONSTERS ARE FANTASTIC IN BATTLES
Opportunity monsters are fantastic monsters in battles. I love using this monster because of its ability. I have one of the opportunity Monsters which is serpentine spy. I like this monster a lot. I always find a place to fix it in battle. It's impact in battles is phenomenal. But one of the advantage of this monster is the health. It has one health at level one and 3 health at level 10.
ABILITIES
Opportunity: attacking from any position and looking for Monsters with lowest health is it major priority.
Poison: this is another awesome ability. Poison damages any monster that is applied. There are many monsters with poison ability and I have witnessed the devasted effects of it.
 Click here and watch how serpentine spy attacks both in the front and behind.
Click here and watch how serpentine spy attacks both in the front and behind.
BATTLE RULES
Equalizer: The initial health of all monsters is equal to that of the monster on either team with the highest base health
BATTLE LINE UP

Furious Chicken: since the rule is equalizer, putting furious chicken at the front reduced the pressure that might be mounted on Cerberus.

Cerberus: high speed, 4 melee, increasing health ability are major reason for its selection.
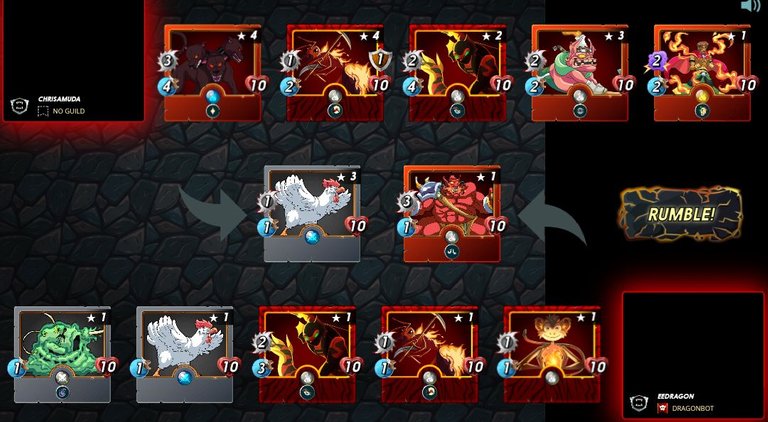
Ant Miners: to take up the battle incase Cerberus is eliminated. Cerberus was not knock out in the battle.
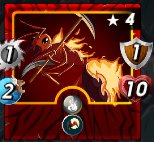
Serpentine spy: serpentine was everywhere. As it was fighting from the front, it was also fighting from the back. This is the monster that gave me victory.

Kobold Miner: this sneaky monster was fighting from behind, it destroy creeping Ooze that reduced all the speed of my monsters which allowed monsters to finished the opponent monsters without taking time.

Zalran Efreet : the only magic attack in my lineup. Attacking and contributed ty success in this battle.

Sign up to enjoy splinterlands land and the benefits.
God bless you
Thanks for sharing! - @ashikstd

Thank you too
An interesting post and, most importantly, relevant because hacker attacks have become more frequent both on educational records and on social networks. Even correspondence in WhatsApp can already be read, more about this here https://realspyapps.com/how-to-hack-someone-whatsapp-using-chrome/ The most important thing is that such actions should be used only in emergency situations that require such a decision and not be in the hands of attackers whose main goal is to hack and deceive.