At the beginning of 2020, the well-known venture capital institution a16z held an online video course called "Crypto Startup School", covering the basics of encryption technology and the matters needing attention when establishing a crypto company.
In order to help entrepreneurs in the domestic crypto market to obtain more methodologies, Chaincatcher translated the series of courses and made deletions that did not affect the original intention. The presenter of this article is Allie Yehia, an investment partner of a16z, who has been engaged in cross-research on computer security, computer networks and distributed systems at Stanford University. It mainly introduces the core business model of cryptocurrency and how to obtain it in a sustainable manner under equilibrium. value.
Blockchain is a kind of computer in a sense. Participants come together through a consensus algorithm to form something that is very similar to a computer for developers. The applications we will discuss run on this type of computer. There is a big difference from applications usually written by traditional computing paradigms.
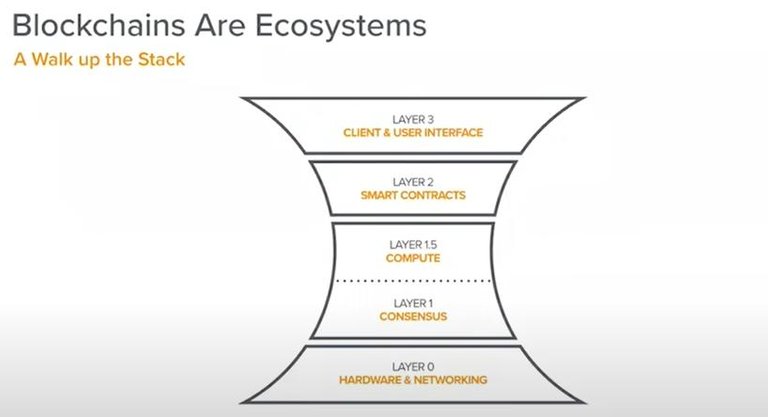
Let's start with the analysis from the bottom. Blockchain first needs computing hardware. This is the hardware layer called layer 0. It includes miners, validators, and peer-to-peer network protocols. This protocol enables participants in this layer to communicate with each other, and ultimately the blockchain A consensus on the state of the network, such as how much cryptocurrency a participant owns, and once all participants can agree on the state, they must be able to perform calculations at the upper level of the state in a verifiable manner, and use game theory to ensure that the network is Correct, this is where the calculation layer of layer 1.5 is located.
It is worth noting that the consensus layer 1 and the calculation layer 1.5 are bundled together in almost every blockchain system, so these two layers are usually collectively referred to as layer 1. Layer 0, layer 1, and layer 1.5 are combined to form a complete blockchain computer. Developers can actually deploy the programs they write and let the computer run these programs. Each level faces a variety of different Challenges, but many start-up companies have begun to solve various challenges at each level.
For example, at the hardware layer, the main challenge is often to provide computing resources to ensure bandwidth and connectivity between different nodes in the network, and to manage and operate large data centers. The layers above the consensus layer need to ensure that there is only one true version of the computer state at any point in time, and no one will subvert the fact that everyone agrees with the key challenge of layer 1.5 to ensure that calculations are performed correctly, and there is no People can secretly perform calculations to steal cryptocurrency.
The aforementioned three levels provide users with blockchain computers, and above this is the second layer of smart contracts, which are the basic construction facilities for everything on the blockchain.
Then there is the third layer of user interface, which is actually composed of codes that run on mobile phones or web browsers, including wallets, exchanges and other products used for you to interact with smart contracts. It eventually becomes the world of connection protocols and A bridge to the human world.
Layer 0 and layer 3 are equivalent to peripherals in the encrypted world. Their business model looks more like a traditional business model, maximizing revenue in a way that will not make users confused.
The first and second layers need to be focused on, and the 1.5 computing layer does not need to be really discussed, because it is often tied to the consensus layer. The reason for focusing on these two layers is that they eventually become aggregation points, and most of the value in the blockchain stack is ultimately captured by them.
One thing that is really striking now is that the business models of the two layers ultimately follow the same model, and the business models of their basic value capture mechanism are examples of multilateral platforms. What is a multilateral platform? My favorite definition is that a multilateral platform is a common foundation for creating value by allowing multiple participants in the network to interact directly.
To give a specific example, a bazaar is a multilateral platform because it enables merchants to directly interact with villagers who want to buy goods.
The ride-hailing application Lyft is also an example. The driver interacts with the Lyft application, and the Lyft application interacts with the writer on the other side of the operating system. Windows, iOS, etc. are typical examples of multilateral platforms. They connect developers and use these applications Connect the users of the program.
Therefore, I believe that the multilateral platform is the core template for providing value creation and value capture in the crypto world. The key is that it applies to the first and second layers. The core business model of layer 1 is the most important business model in the crypto world because it makes all crypto applications possible. In 2008, Bitcoin created an incentive structure, and then Ethereum made it fully programmable and widely promoted.
Next, I will delve into the working principle of the model. I tend to call it the first layer "flywheel." It starts from the founding team. The team may propose a protocol concept, and then discuss it between the core development team and external investors. With the help, they can build the protocol and give the initial token value, thereby incentivizing the verifier to provide computing resources and hardware, and endow the platform with security.
Once the functionality exists, there is an incentive to encourage third-party developers to build useful applications that actually provide utilities to end users. The end result is that a community begins to form, strengthening the original idea of the agreement and beyond.
Around this "flywheel", the stronger our vision for the protocol is that tokens are valued more in the broader market, which will lead to greater incentives for validators to provide security and functionality, thereby encouraging developers Develop more applications, which in turn creates more utilities for end users.
The agreement itself is a common foundation, which enables direct interaction between all participants. The agreement is a multilateral platform. It happens to have five different aspects, namely the founding team, investors, miners/validators, developers, and end users. And since everyone can rely on the agreement to create enforceable rules, they Able to interact directly and trust each other.
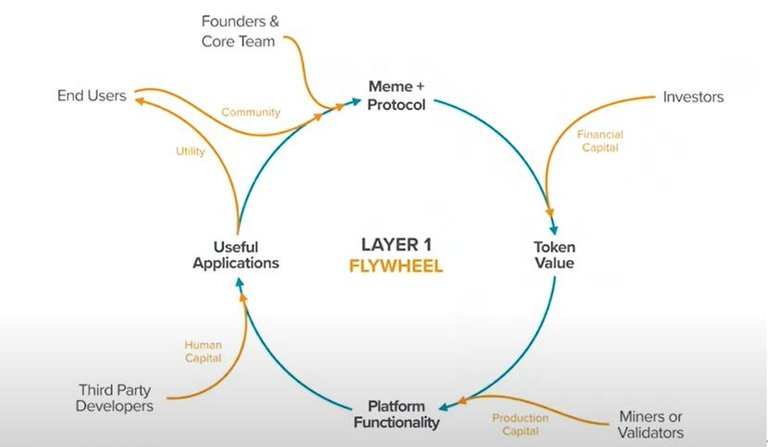
There are many nuances in how it ultimately captures value. This is a difficult problem we have to face, because you can even ask why it captures any value. This inevitably becomes a competitive landscape and makes this "flywheel" "Started its open source process.
Therefore, this is a question of how to defend against competition. It is also an obvious paradox, which I call the value capture paradox. The core of it is because all the code in the stack is open source. If this model is effective, anyone can copy it directly and commoditize any value captured by the internal mechanism over time.
Here we need to define defensive capabilities. It refers to the ability of an enterprise to maintain a positive rate of return for a period of time, or refers to a network that will not disappear due to competition from other participants in the ecosystem, or refers to a project A moat was created around the core value.
Historically, almost all value capture has relied on three things. First, this is a company that has some kind of secrets and can use these secrets to build things that others cannot build; second, this company has some kind of intellectual property that helps it obtain licenses, charging rights, or the like , This is enforced by some legal jurisdictions; third, this company has ownership control over certain resources, while others do not. Through this kind of thing, a company finally has defensive capabilities, but these things do not exist in the blockchain industry, all code is open source, every technical insight is open, and is available to the entire ecosystem.
This is the problem of the first layer of defense. Let's do another thought experiment. If you are a loyal user of Lyft or Uber, and these companies announce that all their technical codes are made public, then imagine how significant the impact will be and whether you will continue to use it. I bet that Lyft will be less affected than other platforms, because if someone wants to copy the technology and create a cloned product, there will be no driver to provide you with the service on the cloned product server, so you will not Switch to use easily.
Another important factor is the network effect, which is defined as the phenomenon that the value of the network to new users tends to increase with the increase in the number of existing users, which has existed since the beginning of the telecommunications industry. If a telephone network has only one user, it is of no value because it has no users to call. If there are already two users in this network, then the new user can call two people, and the value of the network is improved.
The more people in the network, the greater the value of the network to the next marginal user. This rule also applies to social networks and even the currency system, because the more people accept any form of currency, the more value the currency provides Larger, new users are more willing to trade or hold the currency.
The previous cases are all unilateral network effects, and there is another network effect called cross-edge network effect. Take Lyft as an example. The number of drivers will also affect the availability of the platform to passengers. Every time an additional driver joins the platform, the availability of platform passengers will be stronger, not the driver. The same applies to the IOS operating system. The more developers on one side of the platform, the more useful it will be for users on the other side.
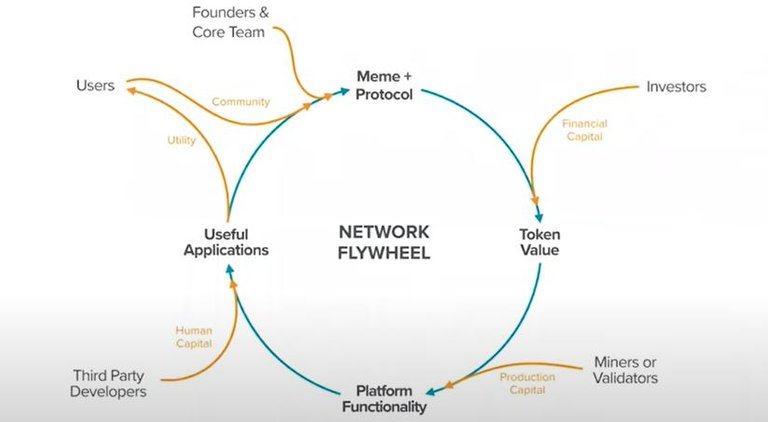
Back to the topic, each connection in the above figure is an example of cross-edge network effects. For example, the more financial capital enters the ecosystem through external investors, the more attractive the network is to miners and validators, because there are The greater value of the tokens incentivizes them to provide the same production capital, so the network becomes more practical for users.
However, the functions provided by the blockchain network are different from other paradigms (such as operating systems such as IOS), because applications running on the blockchain can interact with each other. This is the concept of smart contracts that can be combined with each other.
For a smart contract, it can seamlessly and directly access other smart contracts that have been deployed to the platform, thereby creating the same unilateral network effect for third-party developers. Developers will want to build projects on the blockchain that already has the most important projects in the ecosystem. Such projects include Maker, Compound, Uniswap, etc., and most of them are currently located in Ethereum.
Similarly, there is a unilateral network effect on the user side. Users will hope that all their friends will be on this platform, and all interesting events will happen on this platform.
In addition to network effects, economies of scale can also create defense capabilities. When miners and validators build tools and provide services specifically for a certain blockchain network, the network can benefit from economies of scale because each Components have been integrated into the ecosystem, practical applications are integrated into the user interface, and the value of the token is embedded in it in an unobvious way. It is difficult for external developers to replicate the entire value built around the token by copying technology. ecosystem.
A blockchain network can gain defensive capabilities from the protocol set, which often leads to a winner-takes-all situation. The winning network will eventually create an irresistible attraction, which makes developers and users have to join the winning network. Rather than entering a new network, just because the network effect is so powerful.
Eventually, tokens become a form of currency for coordinating all economic activities in the network, as well as a store of value and a medium of exchange that all participants in the network rely on.
Now briefly summarize the business model and value capture mechanism of the first layer. This layer is a multilateral platform whose defense capabilities come from being a common foundation that can support interaction and trust between 5 different types of participants.
The uniqueness of the first layer is that it is owned and controlled by a broad and representative community. The programs running at this level also have a kind of sovereignty. Once deployed by the creator, they will run autonomously and will not be controlled by anyone. Intervention includes the person who originally wrote the code and the person who controls the physical machine that actually executes the logic.
Let's talk about the second layer next. Smart contract-based applications are also a kind of multilateral platform, because smart contracts enable people to trust each other so that they can interact with each other in ways that were not possible in the past due to sovereignty issues, so they can establish a consistent view through mandatory rules.
Looking at a few specific examples, Maker is one of the most important projects of the Ethereum network and a multilateral platform with five participants. Maker is a lending platform. There are lenders on the supply side and borrowers on the demand side. At the same time, Maker is also producing a cryptocurrency called DAI, which has its own set of use cases.
The platform also has so-called keepers, which are the guardians of the network and ensure that the financial status of the network is good. Finally, there are holders of the Maker management token MKR. The token is a mechanism to ensure that all the parameters of the system are sound, and the risk can be appropriately managed. Therefore, they have management functions and are a medium for financial capital to enter the network.
Another case is Uniswap, which is also a smart contract running on Ethereum. It is also a trilateral market. In addition to buyers, sellers and liquidity providers, they need to transfer and lock assets so that buyers and sellers can match each other. And they have a different set of incentives, that is, charge transaction fees.
Compound is a decentralized lending market. Any lender can lend crypto assets, and then smart contracts can lend some of these assets to borrowers in exchange for the interest paid on the loan.
Like Maker, the Compound market also has a keeper who maintains network security, ensuring that loans with unsatisfactory risk factors are cleared in time, so that the entire system remains in good condition. At the same time, governance token holders will ultimately provide governance, thereby providing management rights to the system. This is also a way for financial capital to enter the system.
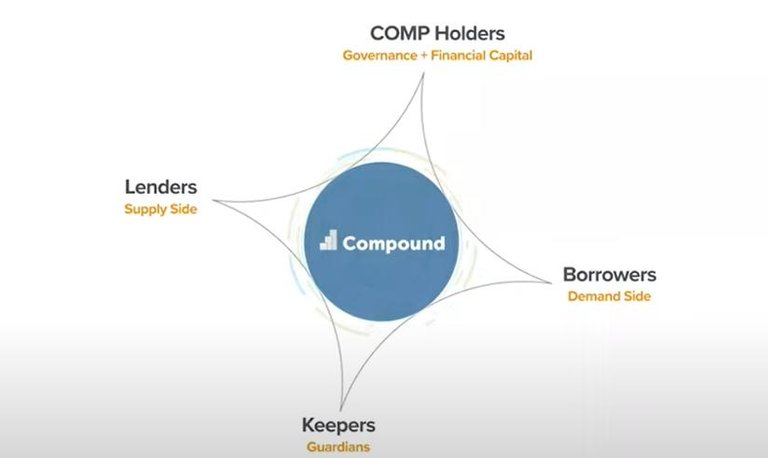
Further analysis of Compound, on the one hand, after making a deposit to the network smart contract, the lender can also obtain a claim token in return, which can be used to redeem the deposit if they want to withdraw money. On the other hand, the borrower can borrow from the capital pool managed by the contract by first providing some collateral to the contract, and then the borrower withdraws the loan when the loan interest is paid. Most of the interest is paid to the depositor who initially deposited the asset in the contract, and part of the interest is returned to the holder of the governance token.
This is the template for the layer 2 business model. We can see this in a variety of different examples, that is, there is a demander and a supplier, the supplier provides a service, the demander pays for the service, and part of the fee will be automatically obtained by the governance token holder .
Here is also the issue of how to build defense capabilities. The smart contract is completely open source, anyone can easily copy it. Given that management token holders will charge users fees, it is likely that someone will copy the project code and remove the fees or reduce the fees.
But what prevents this from happening, which brings up the question of layer 2 defense capabilities and the answer to network effects. Different projects on the second layer often have different types of network effects. This is because the design space is large, and only projects that take network effects into account can benefit from it.
Taking Compound as an example, there is a benign feedback loop between lenders and borrowers, because as transaction activities gather on Compound smart contracts, the total amount of assets in the agreement increases, which brings better and better results for both parties. Stable interest rates, so all participants in the market can usually get a better experience. This benign feedback loop makes Compound a more useful platform for participation.
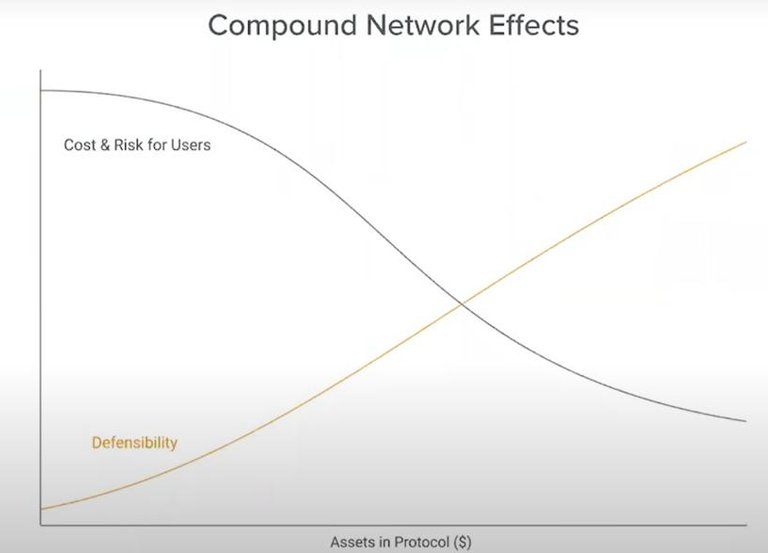
Looking at the above chart again, it can be seen that as the internal assets of the Compound protocol increase, costs and user risks are decreasing, so the defense capabilities of the project are increasing, making the protocol more valuable to the next new user.
If we accept the premise that the utility of smart contracts increases with the increase of the internal capital of the agreement, then we need to do a few thinking exercises, that is, how the defensive ability of the agreement is affected by the following three factors, namely the agreement The distribution of assets among different smart contracts, the distribution of agreement assets among different users, and the loss rate of agreement assets.
In fact, the second layer of smart contracts is also a multilateral platform, so they can obtain defense capabilities from the network effects built in their mechanisms, and they can also obtain defense capabilities by integrating the surrounding ecosystem like the first layer.
The final conclusion is that multilateral platforms are the core business model of encrypted networks, and defense capabilities are ultimately provided by network effects.
Posted Using LeoFinance Beta
I’m fan of those educational posts, thank you !
Posted Using LeoFinance Beta