
Lazarus Group Behind the $1.46B Heist from Bybit
The North Korean-linked hacking collective Lazarus has drained $1.46 billion in staked ETH and ERC-20 tokens from the cryptocurrency exchange Bybit. The breach, which sent shockwaves yesterday through the crypto-sphere, eclipsed previous attacks and now stands as the largest crypto hack in history unless you consider today’s BTC prices for the Mt Gox exchange hack.
Masterclass in Deception
Lazarus Group’s operation was a sophisticated social engineering scheme. The attackers targeted Bybit’s multisig cold wallet, a system that typically requires multiple sign-offs for transactions. By deploying a counterfeit interface, designed to mirror Safe Wallet’s legitimate UI, the hackers deceived signers into approving what appeared to be routine transfers. Lazarus has been linked to previous similar exploits, including the $625 million Axie Infinity (Ronin Bridge) hack, the Harmony Bridge, Atomic Wallet, WazirX hack, and Stake among others.

Who is Park Jin Hyok
At the center of this, stands Park Jin Hyok, a figure whose name has become synonymous with high-stakes crypto attacks. Wanted by the FBI, he is linked to other breaches such as the WannaCry and the Sony Pictures attacks, and the Bangladeshi Central Bank theft. Per international law agencies, Park is one of the most dangerous figures in cybercrime.
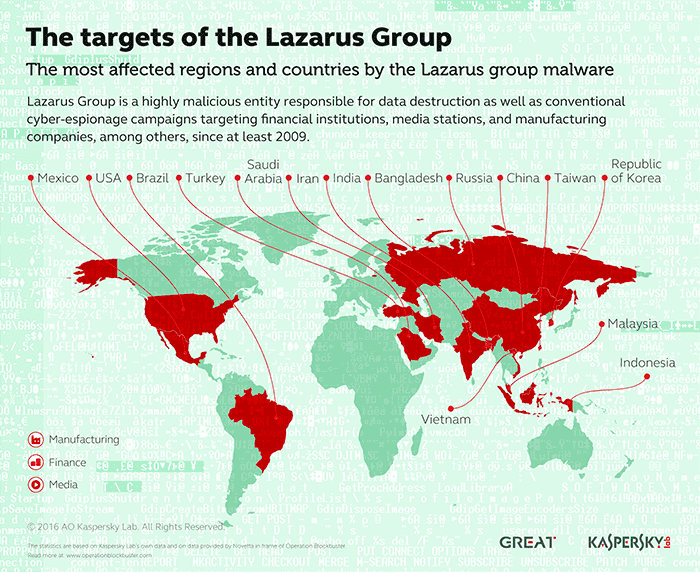
State-Sponsored Operations
Lazarus isn’t a typical group of cybercriminals. Operating under the protection of North Korean state, their hacks have long served as a covert funding mechanism for the nation’s military and nuclear financing. With over $3 billion siphoned from crypto ecosystems worldwide, their operations are part of the cyber warfare doctrine employed by North Korea and require long-term strategic planning. The group’s modus operandi often involves infiltrating companies through tactics such as impersonating recruiters or business partners, only to exploit vulnerabilities with precision-targeted malware, phishing, and DeFi security vulnerabilities.
Crypto Laundering
Once stolen, Lazarus' focus will shift to creating the perfect environment to mask the funds. Rather than cashing out immediately, Lazarus is known for holding their stolen crypto for long periods, sometimes years. When they do decide to launder the assets, they’ll turn to DeFi platforms and crypto mixers that don’t require KYC/AML to facilitate token swaps without the constraints.
Posted Using INLEO
Congratulations @ceekz! You received a personal badge!
You can view your badges on your board and compare yourself to others in the Ranking