
How Scammers Are Targeting Non-Custodial Wallets and How to Protect Yourself
Cryptocurrencies have revolutionized the financial world, offering decentralization, transparency, and financial sovereignty. However, with the rise of digital assets, the threat of scams and theft has also grown exponentially. Non-custodial wallets, which give users full control over their private keys, are increasingly becoming a prime target for scammers. Every year, millions of dollars are lost to these sophisticated scams, leaving victims devastated. This article explores how scammers are stealing cryptocurrencies from non-custodial wallets, the scale of the losses, their tactics, and how you can safeguard your digital assets.
**The Scale of the Problem: How Much Money Is Being Lost? ****
The cryptocurrency industry has become a lucrative hunting ground for scammers. According to a 2023 report by Chainalysis, a block chain analytic platform, over $3.8 billion was lost to cryptocurrency scams and thefts in 2022 alone. A significant portion of these losses stemmed from attacks on non-custodial wallets, where users hold their private keys. Unlike centralized exchanges, non-custodial wallets are not managed by third parties, making them inherently secure but also more vulnerable to user error and sophisticated scams.
The decentralized nature of these wallets means that once funds are stolen, they are nearly impossible to recover. Scammers exploit this by using a variety of tactics to trick users into surrendering their private keys or sending funds to fraudulent addresses.
Common Scammer Tactics Targeting Non-Custodial Wallets
**1. Phishing Attacks **

Phishing is one of the most common tactics used by scammers. They create fake websites, emails, or social media profiles that mimic legitimate wallet providers or cryptocurrency services. Unsuspecting users are tricked into entering their private keys or seed phrases on these fraudulent platforms, giving scammers full access to their wallets.
**2. Fake Wallet Apps **

**3. Impersonation and Social Engineering **

Scammers impersonate customer support representatives, influencers, or even friends to gain trust. They may contact victims through social media, email, or messaging apps, claiming there is an issue with their wallet and requesting their private keys or seed phrases to "resolve" the problem.
**4. Malware and Key loggers **

5. Fake Airdrops and Giveaways
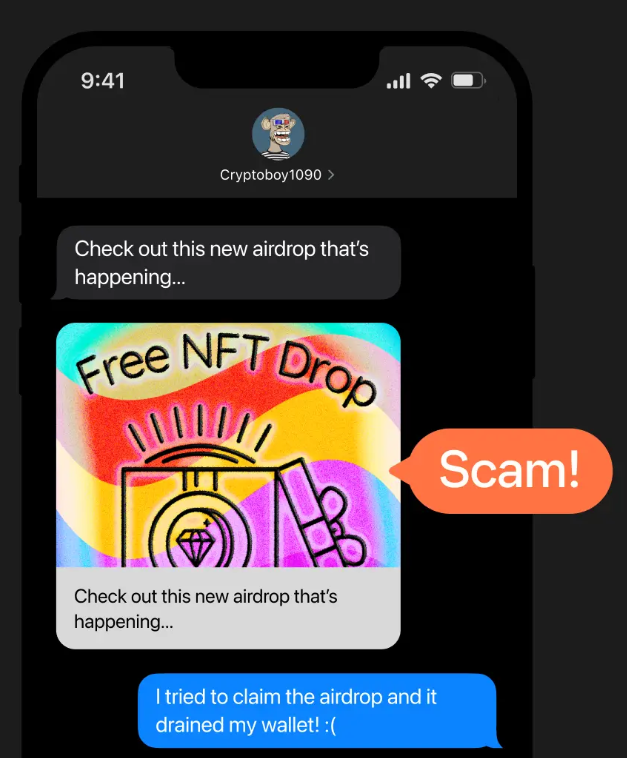
Scammers promote fake airdrops or giveaways, requiring users to connect their wallets to a malicious website or send a small amount of cryptocurrency to participate. Once the wallet is connected, the scammer can drain its contents.
**6. Address Poisoning **

In this tactic, scammers send tiny amounts of cryptocurrency to a victim's wallet from an address that looks similar to the victim's own address. The victim may accidentally copy the scammer's address when sending funds, resulting in the loss of their assets.
(To be continued…..)
Posted Using INLEO