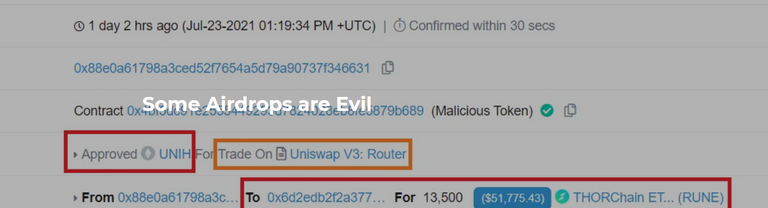
Not every token that makes it into your wallet is there to make you a bit more rich, in fact in some cases quite the opposite. This was literally the case during 23rd of July 2021 when thousands of Etherum Wallet addresses were airdropped with a brand new UNIH token which when attempted to be sold would've magically drained the wallet from another token, so lets dive in how the hell that even happened.
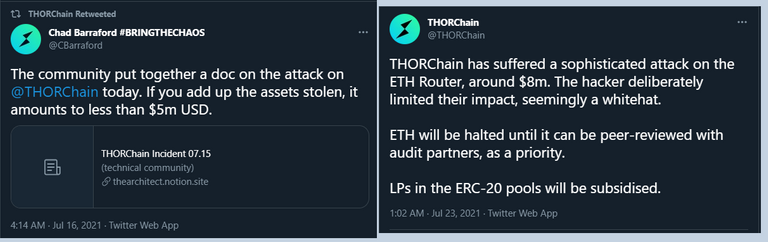
The story begins with a somewhat related streak of attacks on Thorchain in the last week with the attackers stealing about $13m due to protocol level vulnerabilities which most likely gained attention of other hackers seeking any other little or big exploitable opportunities in its protocol.
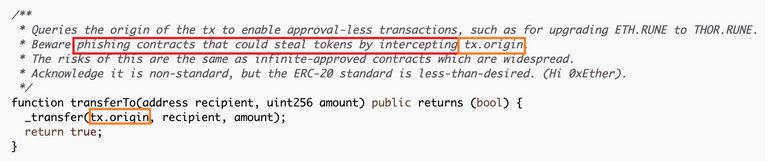
It hasn't took long for someone to find yet another vulnerability which has been there in the $RUNE contract since its creation affecting its transferTo function which does not follow the Solidity security considerations and to be fair is actually clearly noted in the comment of the vulnerable function, hence a design choice by the Thorchain team.
This design choice and the comment itself arguably was asking for some troubles, and consequently has resulted in an attacker launching a phishing airdrop of $UNIH token which was targeted and distributed to over 7,000 wallets which had big amounts of $RUNE tokens.
The reason the attacker had to distribute a fake token was due to the fact the vulnerability was not exploitable without user interaction with the malicious contract and by far the easiest interaction an attacker can achieve is to lure one to attempt sale of the airdropped token.
You may think that when selling a token you would typically only interact with a trusted protocol like Uniswap, however this is not exactly true as prior to the sale of the token the user has to allow it to be traded on Uniswap through the token's smart contract. Here is where the user is left at the mercy of the correctness and non maliciousness of the token's smart contract approve function.
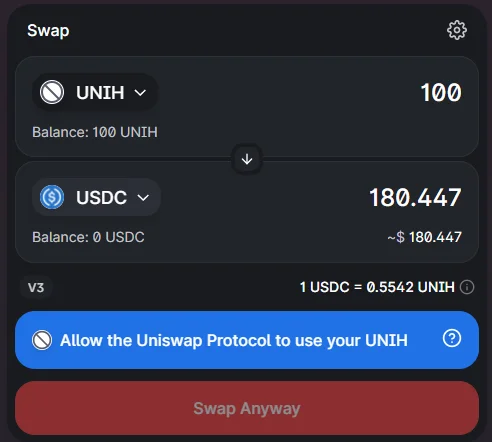
Since the ERC-20 standard does not enforce any strict checks on what is actually happening in the approve function the malicious smart contract has used it to its advantage and written logic that would perform a direct call to the $RUNE smart contract transferTo function on behalf of the user, hence exploiting its highlighted vulnerability and resulting in transfer of all $RUNE token funds to the attacker's wallet.
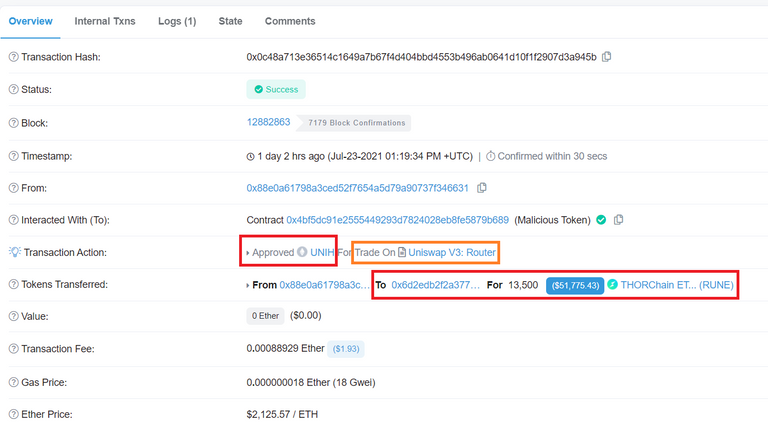
This has unfortunately resulted in at least $75k worth of $RUNE tokens being stolen with one user losing over $50k as a consequence of calling the approve function from within Uniswap.
Sources:
https://etherscan.io/address/0x4bf5dc91e2555449293d7824028eb8fe5879b689#code
https://etherscan.io/tx/0x0c48a713e36514c1649a7b67f4d404bbd4553b496ab0641d10f1f2907d3a945b
Originally posted on read.cash
Posted Using LeoFinance Beta
Makes me remember a certain coin called "Minereum" that steals ETH FROM users wallets
Interesting, was that in early days of ETH ?
Posted Using LeoFinance Beta
Nop, quite recent.
Thank you for telling us!
Posted Using LeoFinance Beta
You're welcome ! Thanks
Posted Using LeoFinance Beta
Congratulations @ir-crp! You have completed the following achievement on the Hive blockchain and have been rewarded with new badge(s) :
Your next target is to reach 60 posts.
You can view your badges on your board and compare yourself to others in the Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!