Seele has been hit by some bad press in recent weeks, not exactly great when trying to market your ICO. The issue is in the crypto space it seems like almost everything is labelled a scam first and then has to prove it’s not a scam, the reverse of the usual innocent before guilt verdict. We’ve seen this with most projects such as the recent Fusion ICO which copped a massive FUD campaign with baseless and misinformed points raised and repeated on multiple forums and sites. Qtum, Icon and Walton are also a few other ICOs that were labelled a scam during ICO. Goes to show you that people are quick to label everything a scam, I guess this is due to the unknown new and emerging state of blockchain and crypto. It’s probably also the case because this market is actually ripe with scammers and some ICOs have done quick exits leaving investors out of pocket.
I will start off by saying the Seele domain and email associated with the domain registration “[email protected]” has been flagged as being associated with multiple scams. This is true but shows the lack of understanding and quick to judge nature of these people. The above email address and domain registrar contact is a domain privacy service for Chinese domains. So yes it is used on multiple sites, some of which are scams and some of which are normal businesses that would like to protect their privacy. For instance Walton also uses this service. This is not a worthy claim to say Seele is a scam.
The biggest thing most people point to is the potential “inside job” hack which stole $2 million from investors. Not great publicity when trying to run an ICO, my opinion is that it most definitely was not an inside job. It is hard to understand why a member of the team would do such a thing especially the user in question Dr Nick Smith. I have read the articles and watched the analysis from all sides for my own due diligence and have come to the conclusion it was a well orchestrated and lucky case of social engineering.
To explain how this is easily possible without any “inside man” you first need to understand that this is a team of multiple people from different professions, locations and with varying roles. For instance, the Telegram admins for the most part do just that, community management. While they would have direct communication with the rest of the team they most certainly would not be communicating with them for every little thing here and there.
Therefore, we have the case where an impersonator can falsely portray themselves as a main team member and sneak in, a perfect example of social engineering. Just as easy as shown in the screenshot below, upon first glance it looks legitimate as the attacker is clearly playing on the demand and pressure the community team would have been under at the time this occurred. As an existing admin it would then be likely you wouldn’t even question this especially considering it’s coming from your “boss” for lack of a better word.
From there it’s pretty much game on for the attacker who sent messages to telegram members asking for investment and with the “admin” tag this looks quite professional. However, it must’ve been these investors first day on Telegram as inboxing members asking for funds is perhaps the biggest red flag you can get!
The team member who let the attacker in was @rebecca666 who I know is also an admin of Go Network and Arcblock as I am also a member of those groups. Therefore it shows that the admin who let the attacker in is not even a major team member rather is a Telegram admin for multiple groups. So you can see how is easy it would have been for someone who impersonates a member of the team to sneak in when the admin in question is not even a direct member of the team. Simply a lack of communication and confirmation.
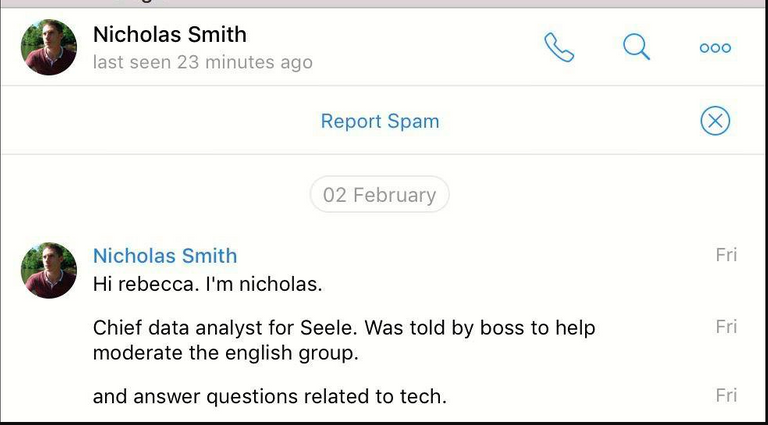
All in all this could have been avoided if there was a confirmation from the main team before adding the new admin member. I don’t believe there was any inside job or malicious activity from the Seele team, it was simply a right place right time perfect example of social engineering mixed in with beginner investors greed.
I also don’t believe it is Seele’s fault as sending money over private message without a smart contract to confirm is asking for your money to be stolen, investors should assume their own risks. I do admire that Seele have taken steps to prevent this from happening again and are also actively pursuing the attackers with their partnership with Bounty0x.
How about the fake partnerships, the lies about the qualifications of the team, Bounty0X ended the bounty with suspicions of an inside job from seele team. I mean, how many red flags do you want?