
A highly secure digital data storage service.
Technological breakthroughs in security and information security are stored and transmitted
IDM
Website: https://myidm.io/
Hello welcome and welcome to read.
This time ane will review a platform for storing digital data all agan-agan. the platform name is MYidm. so stay here yes, read through thoroughly and do not forget to visit his site for more info.
What is Myidm?
So this Idm is a platform for storing highly secure digital data. The highest level of data protection, previously only available for government structures, is now available to the public. so later we can keep our digital data data safely without worrying about the attacks that will be hackers to retrieve important data data. IDM will be a new important attribute of everyone's life like ID cards. IDM is a public service with protection that exceeds existing government standards for safe storage of information.
Project Objectives
The main objective of this project is to raise funds for the development and scaling of existing data storage services, incorporating SIZE, an innovative post-quantum encryption technology, with blockchain.
Current trends and issues related to cloud data storage
The 21st century is the age of information. The more data generated every day basis creates an ever-increasing demand for storage space. Not all home computers, let alone mobile devices, can store all the data they generate themselves. The built-in memory capacity evolves along with the requirements for data security. Increased volume of proportionally generated data increases the number of potential threats to data storage. With the growing number of devices, cloud storage services are becoming increasingly important. Many cloud storage providers promise fast, reliable, and convenient services. However, the reality is a bit more complicated.
What threats to the current information?
How do you rate cloud security services?
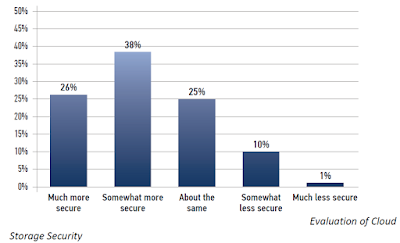
Pure statistics
o The year 2013 is marked with a scandal involving SSL services that use certificates expired by Microsoft Azure, which provides an opportunity for criminals to hack the Xbox Live system;
o An incident called Celebgate, which occurred in 2015, when hackers steal
celebrity celebrity photos from iCloud cloud storage (Apple);
o The number of hacks inflicted on the cloud service continues to increase each year by about 50%;
o About 70% of companies have at least one application running in the cloud;
o Lloyd's of London and Cyence believe that a massive attack on cloud storage could cause a loss of more than $ 5 billion, and only 15-17% of the total amount will be covered by insurance;
o In 2017, Equifax data storage, a leading US consumer credit reporting institution, has been hacked resulting in the loss of personal data of 143 million subscribers. As a result, the value of the company's shares plummeted by 13%;
o The absence of two-factor authentication resulted in the theft of personal data of 80 million customers of Anthem, an American health insurance company.
Losing data in cloud storage
Despite the fact that this type of storage is called "cloud", the data is physically stored in terrestrial and underground locations, called data centers. The actual storage device is a hard disk susceptible to various effects similar to those attached to modern HDDs, such as the appearance of bad sectors, errors caused by voltage drops or physical damage to the disk surface, either due to improper operation or design flaws. As a rule, all information is duplicated in a backup copy according to a specific schedule. However, this method does not fully guarantee the security of your data. Also we must consider the human factor.
Data theft from cloud storage
Data is not always lost as a result of technical failure. Often there is a superficial theft. That criminals can steal information just for fun or with the intention of honing their hacking skills. Information can be stolen with a very specific purpose: to make money squeezing or selling valuable data to interested parties. Not long ago, the media buzzed with the news about the theft of photographs of celebrity selebritas from the cloud storage belonging to one of the major players in the mobile market. After the scandal, the company is responsible for the security of storage, as a third party contractor, leaving the market, but the photographs were, however, going around the world.
Network Attack
Storage where your data is located may be affected by targeted cyber attacks. Because of the Case, you could be a casualty, especially if the hacker targets the entire service with the intention of stealing or destroying personal data from a particular user, be it an individual or a company.
DDoS Attack
No matter how secure cloud storage is a simple DDoS attack can cause huge losses to the service by slowing down or blocking its operation, with users not being able to retrieve their data or use the service.
Human factor
Despite the abundance of cyberthreats, the so-called human factor remains the most dangerous element in the process of securing the data. An attacker can be found inside the data center, for example, as a system administrator. This situation is quite common. Some employees are willing to commit crimes to enrich themselves. Personal data that is stolen or access to that information can be sold to various criminal organizations that can inflict massive damage.
Technological advances and data protection methods in cloud storage
According to experts from Gartner, the world's leading research and advisory company, more than 80% of data loss in cloud storage is caused by customers, not by cloud storage services. As a rule, the loss is due to inefficient organization of data work by the customer. According to statistics provided by Gartner:
64% of all data service customers believe cloud storage is safer than conventional methods of service to store and secure customer-side information;
o However, 75% of customers encrypt data before uploading it to the network;
o 52% strictly regulate and strictly control the granting of access to corporate data;
o Nearly 50% of companies regularly analyze and verify their data management systems;
o By mid-2018, 80% of all IT budgets will be allocated to cloud solutions;
o 49% of companies delay the deployment of cloud storage due to lack of cybersecurity skills;
o Currently, only 23% of companies have full confidence in cloud storage services in terms of data protection.
Project Summary
IDM has its own patented data protection technology called SIZE and is preparing to launch a new service - a global decentralized ecosystem that connects users who want to safely store information and miners who provide memory on their devices to generate revenue.
Our development team has created a working prototype of a cloud storage service called BoobookBox. The service was launched in 2015 and has more than 2 thousand active users. The work prototype was launched to test the technology, both by developers and third-party organizations.
IDM can successfully compete with all cloud data storage services, as it offers the following:
exclusive features:
o The most secure and secure data storage and data transmission system
o Affordable prices
o The only player in the market that offers this level of data protection
o Intelligent marketing strategy
o Legal guarantee on data security
IDM focuses on a tightly defined segment of the consumer and business market, and takes advantage of a competitive market opportunity, that is, the demand for secure data storage.
Market problems
Rough estimates show, as a result of cybercriminal activity, the global economy loses $ 114 billion annually. Since the advent of the World Wide Web, the United States alone suffered a loss of about $ 400 billion. This is three times more than the country's annual budget for education.
Solutions The global expansion of the IDM data storage service supported by SIZE technology, will prevent consumers and businesses from losing data, and therefore, from the losses it suffers from hacking attacks and information theft
Product Description
The IDM service provides a decentralized distributed data storage system in which security against data loss and theft is provided by the unique SIZE algorithm. To get distributed data storage, this service will rent free memory from miners for prizes. Miners around the world will be able to rent out memory on their devices, including morally and technically obsolete devices (old smartphones, hard disk dates) and receive continuous remuneration. Our patented algorithm, SIZE, supports excellent file protection from loss (corruption) and can guarantee file recovery of only 2% of the remaining data.
The administration of the service will be managed by blockchain technology. SIZE Algorithm Algorithm Description In the frame model of the eraser channel, a new method of correcting error has been developed. During the coding process, using a special algorithm, parity data is generated. This parity data makes it possible to recover deleted channels. Deleted data can be recovered using different sets of data and different parity data. The degree of reliability is determined by the number of coding cycles. The higher the reliability level, the higher is the possible recovery options of the deleted channel. The process by which reliability levels increase, and naturally leads to an increased likelihood of restoration of deleted channel options described as multidimensional parity.
Main benefits:
o Highest quality of service;
o solving data security problems;
o absolute data protection certainty.
Main service: Cloud data storage is protected.
Expected services: o complete security of stored and transmitted data;
o fast 24 hour data access.
Additional services (mining):
o renting from miners free memory on smartphones, memory cards, hard disks, game consoles, etc.
External proof of service quality:
o quality of website;
o service transparency;
o explaining technology;
o level of personnel training;
o the price.
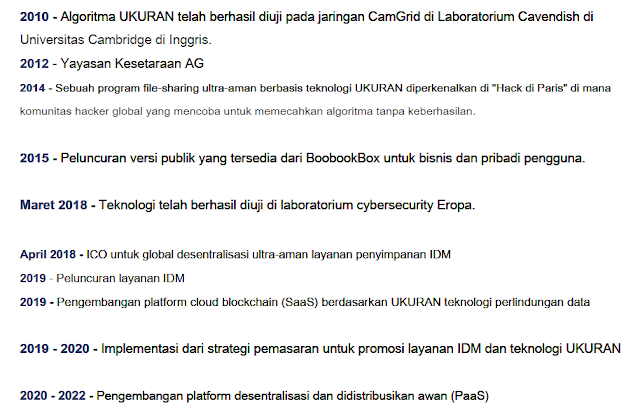
Road Map IDM
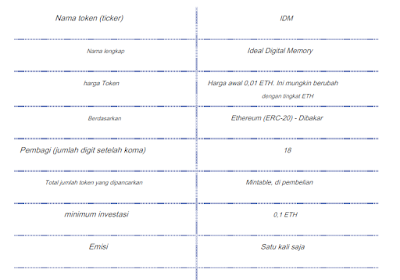
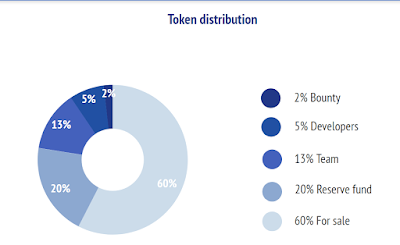
Ico & Token Distribution
Token Distribution

ICO
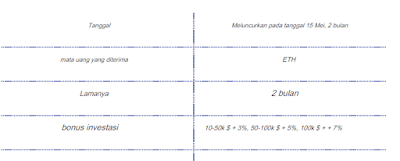
Closing

IDM team


More Info:
Website: https://myidm.io/
Whitepaper : https://myidm.io/img/doc/wp_en.pdf
Ann Thread : https://bitcointalk.org/index.php?topic=3395543.msg35555064#msg35555064
Video : https://myidm.io/video/idm_720p_en.mp4
Facebook: https://www.facebook.com/IDMdatasec
Twitter: https://twitter.com/IDMdatasecurity
Reddit: https://www.reddit.com/user/IDMdatasecurity
Telegram : https://t.me/idmprotect_en
jtwale : https://bitcointalk.org/index.php?action=profile;u=1727454