What's this all about
No single word covers all aspects of the DISARM Framework’s ambit. The framework supports wider harms, beyond disinformation, and encompasses concepts such as ‘IO’ (influence operations), ‘IMI’(information manipulation and interference), ‘FIMI’ (focusing on foreign ‘IMI’), ‘MDM’ (mis/dis/mal-information), ‘Information Disorder’, among other terms and spheres.
We hope people find DISARM a helpful name – the world definitely needs to disarm those who are weaponising the information environment. Breaking it down, we lead with “DIS-” as DISinformation (for want of a better single word) is at the very least a good and valid entry point. We finish “-ARM” as the framework’s common language enables shared Analysis for effective defence, and Risk Management for collaboration that reduces the potential impact of malign actor efforts around the globe.
We will continue to work with our colleagues in the wider community of practice on definitions, as collaboration and convergence is at the very heart of what the DISARM framework exists to do. We aim to play our part in helping the community speak a common language, so that we are all more effective in the goals we share.
Our own definition of ‘disinformation’ is: “The deliberate attempt to influence perception and decision making by presenting information that is incomplete, incorrect, or out of context.” – wider than simply ‘knowingly false information’. But, no matter how the definitions are framed, we share a common set of challenges…
State actors seek geo-political advantage; others seek financial gain; others disrupt and damage our collective security, democracy or health for notoriety or being caught under the influence of cult-like conspiracy theories. None of the above is new, but the internet is enabling the spread and hyper-targeting of disinformation at an unprecedented scale. Disinformation and its related terms comprise a fundamental issue for humankind. It also undermines our ability to collectively address other existential challenges. It requires urgent and effective collective action.
Disarm Link Dump Chronology (v.1)
| Date | Title & URL |
|---|---|
| Mar 22, 2020 | DISARMAMENT: WHAT IS IT GOOD FOR? - by Dr Kobi Leins Senior Research Fellow in Digital Ethics, Computing and Information Systems, Faculty of Engineering and Information Technology, University of Melbourne Banner: A NATO cyber warfare exercise. Jaap Arriens/NurPhoto/Getty Images |
| May 11, 2022 | DISARM: Detecting the Victims Targeted by Harmful Memes Internet memes have emerged as an increasingly popular means of communication on the Web. Although typically intended to elicit humour, they have been increasingly used to spread hatred, trolling, and cyberbullying, as well as to target specific individuals, communities, or society on political, socio-cultural, and psychological grounds. While previous work has focused on detecting harmful, hateful, and offensive memes, identifying whom they attack remains a challenging and underexplored area. Here we aim to bridge this gap. In particular, we create a dataset where we annotate each meme with its victim(s) such as the name of the targeted person(s), organization(s), and community(ies). We then propose DISARM (Detecting vIctimS targeted by hARmful Memes), a framework that uses named entity recognition and person identification to detect all entities a meme is referring to, and then, incorporates a novel contextualized multimodal deep neural network to classify whether the meme intends to harm these entities. |
| May 14, 2022 | Cognitive Security: Misinformation, Disinformation, and Influence Operations - Course Schedule. 2 Day Dojo. Course Abstract Cognitive security is the application of information security principles, practices, and tools to misinformation, disinformation, and influence operations. It takes a socio-technical lens to high-volume, high-velocity, and high-variety forms of “something is wrong on the internet”. This course starts with the ways that users and groups are influenced online, from user experience, marketing, adtech and online political campaigns through to astroturfing, online psyops, disinformation campaigns. We’ll look at the techniques and tactics used to create influence, the tools, methods and design patterns being created to detect, counter and mitigate against it, the emerging discipline of cognitive security and how it meshes with other work including information security, machine learning and geopolitics. The course is practical, arranged around a set of python notebooks and open-source tools, but also rooted in deep theories of why and how disinformation campaigns happen. |
| Jun 6, 2022 | DISARM: a Framework for Analysis of Disinformation Campaigns - 2022 IEEE Conference on Cognitive and Computational Aspects of Situation Management (CogSIMA) State actors, private influence operators and grassroots groups are exploiting the openness and reach of the Internet to manipulate populations at a distance. They are extending a decades-long struggle for “hearts and minds” via propaganda, influence operations and information warfare, often in the form of coordinated incidents that are part of longer-timescale narrative-based campaigns. Our work on cognitive security extends information security principles, practices, and tools, to the detection and management of information harms including disinformation and disinformation. Specifically, we have adapted and extended frameworks used to describe information security incidents, to create the DISARM series of frameworks for understanding and responding to organized disinformation incidents; these have been in continuous use since 2019 for analysis, simulations, training, and country-level disinformation risk assessments. In this paper, we describe how and why the DISARM frameworks were created, and discuss their components and uses, including analysis of ways, means, and ends to achieve influence goals. |
| Aug 9th, 2022 | Mapping Redditors’ attack on Kelloggs to the DISARM framework - disinfodb.org Using DISARM to make sense of a real-world Influence Operation I think it’s useful to have real-world examples of the steps people take to manipulate us online, so I’m going to map elements of an IO to DISARM’s tactics and techniques. Since this is my first time using DISARM I’m going to examine an IO I’m already familiar with; Reddit Mind-Hacktivists conduct a Disinformation Campaign against Kelloggs. This was an atypical campaign in that it was planned on a publicly accessible social media platform, and the threat actors shared recordings and write-ups of their participation (most influence operations are very secretive about their actions). This gave a behind-the-scenes view which we aren’t usually privy to, and is fun to analyse! |
| Sep 21, 2022 | Alfred Landecker Foundation - DISARM Foundation Leveraging a shared communication framework to protect democracies from disinformation To protect our democratic societies, it is vital to advance tools to combat the force's of disinformation and influence operations. By using a cybersecurity approach, DISARM enables trained experts and activists to map, analyse and coordinate responses to threats arising from dis- and misinformation. |
| Oct 19, 2022 | DISARM FRAMEWORK - EU vs Disinfo.eu DISARM is an open-source, master framework for fighting disinformation for those cooperating in the fight against disinformation. It provides a common playbook, language and approaches for diverse teams and organizations to coordinate their efforts and act in harmony. |
| Dec 8, 2022 | Foreign Information Manipulation and Interference (FIMI) and cybersecurity The EU Agency for Cybersecurity (ENISA) and the European External Action Service (EEAS) have joined forces to study and analyse the threat landscape concerning Foreign Information Manipulation and Interference (FIMI) and disinformation. A dedicated analytical framework is put forward, consistent with the ENISA Threat Landscape (ETL) methodology, with the aim of analysing both FIMI and cybersecurity aspects of disinformation. The concept of Foreign Information Manipulation and Interference (FIMI) has been proposed by the EEAS, as a response to the call of the European Democracy Action Plan for a further refinement of the definitions around disinformation. Although disinformation is a prominent part of FIMI, FIMI puts emphasis on manipulative behaviour, as opposed to the truthfulness of the content being delivered. Several strategic documents, such as the Strategic Compass for Security and Defence and the July 2022 Council Conclusions on FIMI, refer to the importance of countering FIMI as well as hybrid and cyber threats. Accordingly, in light of broader hybrid threats that cross different domains, one of the main motivations behind this report is to identify ways to bring the cybersecurity and counter-FIMI communities closer together. The ambition is to provide an input to the on-going and ever-pressing discussion on the nature and dynamics of information manipulation and interference, including disinformation, and on how to collectively respond to this phenomenon. The report proposes and tests an analytical approach describing FIMI and manipulation of information, as well as the underlying cybersecurity elements, by combing practices from both domains: - For cybersecurity: The open methodological framework used by ENISA's annual report on the state of the cybersecurity threat landscape, the ENISA Threat Landscape Reports3 - For FIMI: The open-source DISARM framework used to capture FIMI/disinformation By testing the framework on a limited set of events, the report serves as a proof of concept for the interoperability of the frameworks. |
| Nov 9, 2022 | Hybrid CoE Research Report 7: Foreign information manipulation and interference defence standards: Test for rapid adoption of the common language and framework ‘DISARM’ Foreign information manipulation and interference (FIMI) presents a growing political and security challenge, which is why there is a need for a common defence framework. As an open-source, master framework that draws on best practices in global cybersecurity, the DISARM framework contributes to FIMI defence through the coordination of effective action. This Hybrid CoE Research Report examines the DISARM framework and its suitability for rapid adoption by strategic communications practitioners, and its credibility for specialist FIMI threat analysts. link to .pdf report |
| Jan, 2023 | How A Digital Footprint Provides A Criminal Foothold: The FDD's (Foundation for Defense of Democracies) TCIL (Transformative Cyber Innovation Lab's) Technical Note. The DISARM Framework is on its way to becoming the standard for describing, identifying, disrupting, and countering techniques of influence campaigns. Various agencies worldwide have adopted the framework, including cyber threat intelligence analysts in Taiwan (to analyze Chinese influence operation campaigns),25 the European External Action Service (to monitor disinformation in Europe),26 the European Centre of Excellence for Countering Hybrid Threats, and the North Atlantic Treaty Organization’s Strategic Communications Centre of Excellence.27 |
| Jan 9, 2023 | Analysing Disinformation: Defining The Capability Of A Threat - elemendar.com Disinformation is the new kid on the block of the threat and risk analysis community. Tricky to define and challenging to anticipate multiple frameworks are being developed to help analyse the disinformation capabilities of malicious actors. The Disarm framework offers a structure similar to the lauded MITRE ATT&CK framework. Charity Wright, of Recorded Future’s Diamond Model of Influence Operations, provides another example with a more ‘meta’ framework alternative. Many of these are frameworks-in-progress. Their creators have been playing catch-up since disinformation analysis entered the broader field of threat/geopolitical analysis (relatively recently). |
| Feb, 2023 | 1st EEAS Report on Foreign Information Manipulation and Interference Threats DISARM FRAMEWORK: A COMMUNITY-DRIVEN TAXONOMY OF TTPS At the heart of the Kill Chain perspective on FIMI is the systematic and granular data collection on TTPs used by threat actors to achieve their objective. We therefore need a taxonomy of FIMI TTPs that helps us to operationalise the “B” in the ABCDE framework, which is primus inter pares in our analytical framework. Any such taxonomy needs to be agile enough to adapt to new emerging TTPs, conceptually structured and specific enough to allow for the development targeted responses, as well as open-source to allow for maximum stakeholder inclusion and widespread adoption of a shared taxonomy. Therefore, we strongly advocate for a collaborative and community driven approach that enables each member of the FIMI defender community to contribute. Such an approach would allow analytical teams from a wide range of stakeholders to weigh in with their specific experience and needs to optimise the shared taxonomy |
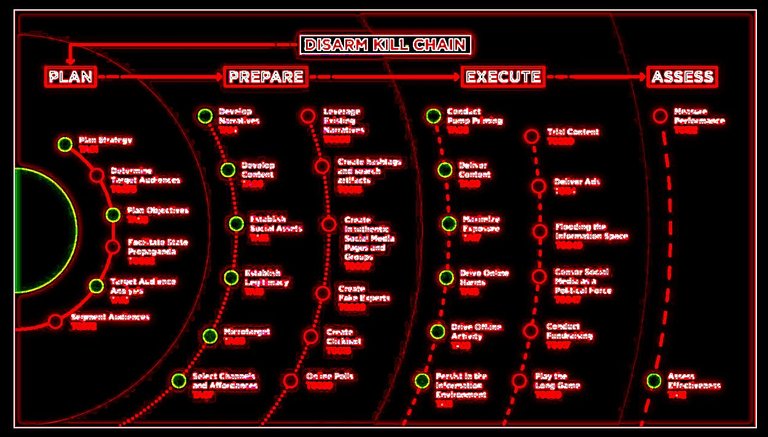
| Feb 22, 2023 | The Kill Chain Model of Disinformation - Fake News Risk Mitigator.eu The Kill Chain model is a widely used framework for understanding the stages of a cyberattack, from initial reconnaissance to post-exploitation activities. The Kill Chain model essentially breaks down the various steps of an attack conducted by a malign actor. In recent years, this model has also been applied to the realm of disinformation, which is the deliberate spread of false or misleading information with the intention of influencing public opinion or gaining some other advantage. Understanding the various stages of the disinformation "Kill Chain" can help individuals and organizations better protect themselves against these types of campaigns. |
| Apr 7, 2023 | FIMI: towards a European redefinition of foreign interference FIMI: TOWARDS A EUROPEAN REDEFINITION OF FOREIGN INTERFERENCE (Technical Paper) This DISARM framework is “the open-source, master framework for fighting disinformation through sharing data and analysis and coordinating effective action. The framework has been developed, drawing on global cyber-security best practices. It is used to help communicators, from whichever discipline or sector, to gain a clear shared understanding of disinformation incidents and to immediately identify defensive and mitigation actions that are available to them”. It provides a set of possible counter-actions to every hostile act, divided into the four typical phases of an attack: plan, prepare, execute, and assess |
| May, 2023 | Jon Brewer - Linked.in Delighted to say that the US and EU have agreed on a common language for data sharing on Foreign Information Manipulation and Interference (FIMI), with the DISARM Framework at its heart. Disinformation - an existential threat to humanity - needs a coordinated response. Step by step, we are building our ability to work together. It needs common standards and a common 'language', so that we can see and understand what's going on together, and so that we can act together. |
| May, 2023 | The Digital Disinformation Research Project - DISARMFoundation / DISARMframeworks DISARM is the open-source, master framework for fighting disinformation through sharing data & analysis , and coordinating effective action. The Framework has been developed, drawing on global cybersecurity best practices. It is used to help communicators, from whichever discipline or sector, to gain a clear shared understanding of disinformation incidents and to immediately identify defensive and mitigation actions that are available to them. |
| May, 2023 | https://coder.social/disarmfoundation Name: DISARM Foundation Type: Organization Bio: The DISARM Foundation exists to keep the DISARM Frameworks open, protected, promoted and supported — by and for the community of those combatting disinformation Twitter: disarm_disinfo Blog: https://www.disarm.foundation/ |
| May 18, 2023 | DISARM Countermeasures Workshop Series — What do individuals need to effectively defend themselves and others against online disinformation campaigns? - DISARM Foundation. |
| May 21, 2023 | How OpenCTI helps to fight disinformation and foreign interferences. In the past year, our product and engineering teams worked closely with multiple companies, public agencies and non profit organizations to extend a bit the threat intelligence model to be able to properly address and modelize disinformation threats, campaigns and incidents. |
| May 26, 2023 | "Hacker, influencer, counter-culture spy: cyberspace actors’ models of misinformation and counter-operations" - DePaul University DISARM Framework: Is the open-source, master framework for fighting disinformation through sharing data & analysis and coordinating effective action.[12]. In this work, it will be used to classify any tools, tactics, or procedures survey respondents. disclose. |
| Jun 6, 2023 | DISARM Countermeasures Workshop Series — How can platforms counter disinformation campaigns? This year, DISARM has hosted a series of workshops exploring countermeasures to online harms. The workshop series is generously supported by Craig Newmark Philanthropies. The objective of the workshops is to gather feedback on the types of countermeasures used to counter online disinformation and other harms, and how to make advice on mitigations and countermeasures to these threats accessible and practical to those who need it. The feedback from these sessions will feed into DISARM’s work to update and improve the existing ‘Blue Framework’ of countermeasures. This workshop focused on what social media platforms can do to protect their users from the threat of online disinformation campaigns. Participants had experience of working in social media companies. |
| Jun 26, 2023 | Giterhub.com - DISARMframeworks repository from DISARMFoundation DISARM Disinformation TTP (Tactics, Techniques and Procedures) Framework DISARM is a framework designed for describing and understanding disinformation incidents. DISARM is part of work on adapting information security (infosec) practices to help track and counter disinformation and other information harms, and is designed to fit existing infosec practices and tools. DISARM's style is based on the MITRE ATT&CK framework. STIX templates for DISARM objects are available in the DISARM_CTI repo - these make it easy for DISARM data to be passed between ISAOs and similar bodies using standards like TAXII. |