Intro
I have as much concern for the well-being of the self-proclaimed "elite" as they do for us...
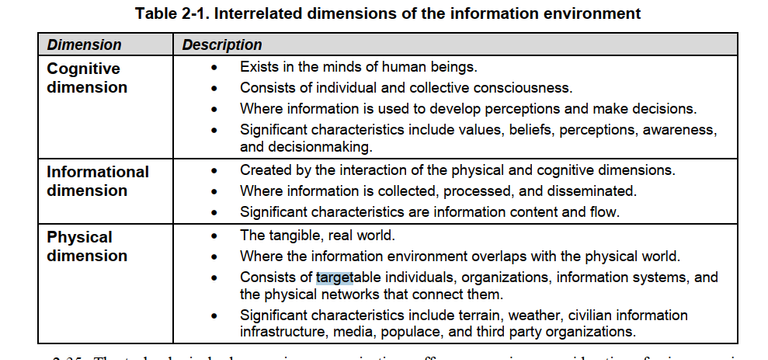
From FM 3-24,INSURGENCIES AND COUNTERING INSURGENCIES (2014 ed)
This article is going to take some reading; it isn't organized well for a couple of reasons. The primary reason is there are several versions of FM 3-24 (a book that should be studied as it applies BOTH ways), and I have read most from the 2007 edition. I'd say the the first section could probably get it done on it's own, but a well-founded understanding is CRUCIAL to success. So we'll look at both targeting models and summarize planning models.
Also, remember that understanding the basics will allow you to pull some of the military literature, and translate their scope into something that you can use.
Contents
- From Resistance To Tyranny: A Primer
- The CARVER Matrix
- From FM 3-24,INSURGENCIES AND COUNTERING INSURGENCIES (2007 ed)
- The D3A Model
- METT-TC
- SMEAC
- BAMCIS
- Last Word
From Resistance To Tyranny: A Primer (Amazon Link)
(This is ALL from the book, except that I deleted certain words)
background information about the target, for planning purposes. The various types of information needed are as follows. These lists are intended to be suggestive, not inclusive. In particular cases, additional types of information may be needed.
This information should include, but not necessarily be limited to:
- Physical description
- Photograph(s)
- Typical wardrobes and clothing preferences
- Relatives and close associates
target's practices and behavior must be studied and documented.
- Addresses of house(s), apartment(s), and other living quarters of the target
- Addresses of offices and other business locations utilized by the target
- Addresses of restaurants, theaters, gymnasiums, parks, and other places of recreation or entertainment regularly used by the target
- Tradesmen, professionals and others patronized by the target, to include doctors, dentists, barbers, tailors, lovers, brothels, and any others regularly
- Transportation, including cars, boats, aircraft or any other vehicles maintained or used by the target
- Regular times and places of visits to friends, family, tradesmen, places of entertainment, or others
- Habits or practices such as jogging, bicycling, regular lunches or dinners, hobbies
- Clubs, business or professional organizations regularly attended
it will be necessary to gather physical data about the building, layout or site.
- Location, floor plans or layout, structural details
- Neighboring buildings, including floor plans
- Nearby terrain, including topography, concealment (bushes, trees), and structures (manholes, culverts, overpasses,sewer openings, alleys)
- Security, including locks, fences, gates, alarm systems, guards, and details of badge and pass information
On the basis of the background information developed regarding the target and the places where the target might be found, a specific mission plan must be developed. It should cover the following items:
- The specific location
- the items used (edited)
- Badges, passes, uniforms, vehicle passes, or other items needed to gain access to the target site
- Location and time when the ... and other items will be provided to the
- Transportation of the ... to the target site (if this is to be a stolen government vehicle, plans must be made
for acquisition and hiding prior to ) - Backup. If the ... attempt fails, then what? A backup consisting of a second...(or team) on the site may be appropriate, depending on the circumstances.
- Escape route and transportation for the ... following the attempt
- Cleanup, including disposition of badges, uniforms, vehicles, etc. in a manner that does not provide information
At least three types of communications will be necessary.
- The “Execute” signal. The ... must be given a signal to execute the plans already developed and prepared for This signal must be delivered in a secure manner.
- The “Abort” signal. There may be some last-minute reason for calling off t... (e.g., the mission has been compromised, or the target has changed plans). There must be a secure means for delivering this to the... even if they have already begun to execute the plan.
- The “Outcome” signal. The Resistance must be informed immediately about the success or failure of the attempt. Other plans, scheduled to be executed following ..., will depend on knowing whether the attempt was successful. Depending on circumstances, it may be more appropriate to have someone else on the scene to report the outcome,
The CARVER Matrix
CARVER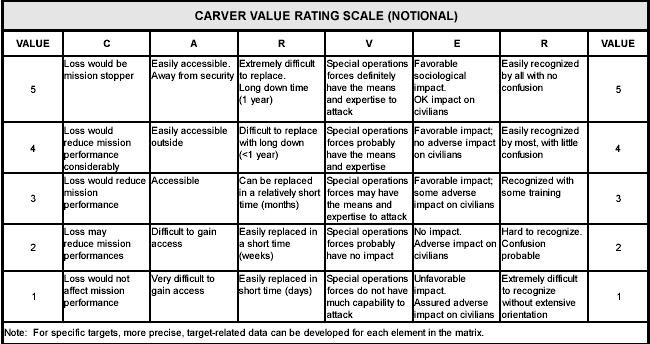
- Criticality (measure of how critical a node is to your service)
- Accessibility (ability to physically access and egress from target)
- Recuperability (ability of system to recover from an attack)
- Vulnerability (ease of accomplishing attack)
- Effect (amount of direct loss from an attack)
- Recognizability (ease of identifying target)
Me: A note on Recognizability; in civil wars, you do not want to ...address..the wrong target even more than you wouldn't want to in other contexts
The CARVER selection factors assist in selecting the best targets or components to attack. As the factors are considered, they are given a numerical value. This value represents the desirability of attacking the target. The values are then placed in a decision matrix.
The ratings in CARVER are very subjective. While the concept is simple, a deep understanding of the target and available resources to attack are vital to producing useful output.
From FM 3-24,INSURGENCIES AND COUNTERING INSURGENCIES (2007 ed)
5-103.Effective targeting identifies the targeting options, both lethal and nonlethal, to achieve effects that support the commander’s objectives. Lethal targets are best addressed with operations to capture or kill; nonlethal targets are best engaged with CMO, IO, negotiation, political programs, economic programs, social programs and other noncombat methods. Nonlethal targets are usually more important than lethal targets in COIN; they are never less important. (Table 5-8 [page 5-30] lists examples of lethal and nonlethal targets.)
5-104.The targeting process comprises the following four activities:
- Decide which targets to engage.
- Detect the targets.
- Deliver (conduct the operation).
- Assess the effects of the operation
5-108.The detect activity is performed continuously. It requires much analytical work by intelligence personnel. They analyze large quantities of all-source intelligence reporting to determine the following:
- Threat validity.
- Actual importance of potential targets.
- Best means to engage the target.
- Expected effects of engaging the targets (which will guide actions to mitigate negative effects).
- Any changes required to the exploitation plan.
Me: obviously, decentralized efforts do not have "large quantities of all-source intelligence" available": this is a case of do what you can with what you can
That last bit? it's known as the D3A model
The targeting methodology for the GCE is decide, detect, deliver, assess (D3A)
METT-TC
SMEAC (the 5 paragraph order)
Situation
Mission
Execution
Administration/Logistics
Command/Signal
METT-TC is a variant of SMEAC. Another variant is the Marine Corps (OOH RAH!!) BAMCIS (we used SMEAC when I was in, but I am an old fart)
BAMCIS
Begin the Planning, Arrange Recon, Make Recon, Complete Planning, Issue Order, Supervise
Last Word
These are models..they are helpful for planning, but play with them and find out what works for YOUR situation and planning.
You'll see that I started skimping on explanation towards the end...yes, I am lazy...but also, these are things you NEED TO STUDY AND UNDERSTAND ON YOUR OWN
Additional Reading
- Hit or Miss? The Effect of Assassinations on Institutions and War
- Building Covert Networks #1 - Introduction, Basic Questions, Background Reading
- How to be an InformationWar Activist - Part Thirteen: An Understanding of Decapitation Strategy and it's Uses Beyond Assassination
- Total Resistance- Swiss Army Guide to Guerrilla Warfare and Underground Operations Major H. von Dach Bern (if you can't find it on the net, try Amazon)
- Think Like a Green Beret: The CARVER Matrix
- Vulnerability Assessment Method: Pocket Guide: A TOOL FOR CENTER OF GRAVITY ANALYSIS

LOL I reckon you are a better man than any of them. Now, I could be wrong, and you certainly have no reason to intend them well, but even intent on their end you prolly reveal that your intent accounts your conscience of merit, while psychopaths cannot, and sociopaths do not.
I wouldn't measure yourself by them, as they are of little account on any level save for power that you regard as meaningful.
Regarding the Carver scale, aren't 1 and 2 reversed in the vulnerability column? You point out the Carver scale is highly subjective, but it just seems to me that little ability is higher than none on that scale.
I really appreciated this post, which was the result of thousands of years of culture and serious men that made a lot of mistakes to learn from. Maybe it will help me make fewer.
Thanks!
I wrote this post, in part, in response to your point about the elites trying to cull the population...the other part of the reason for writing this was after a visit from my relatives....I'll summarize their argumentation on politics REEEEEEEE!; I wasn't even arguing, just shrugging and grinning, but I wouldn't agree with them...
I don't blame them; I blame the people behind the InformationWar on the American people.
The CARVER matrix
I think that whoever put this one together missed a trick on V1. Looking at how the chart works across the board, V1 should read something like
Forces have zero or close to zero capability to attack
Their verbiage isnt clear
Most of the post is quite clear. Crystal even. I am both appreciative and sorrowful that my own REEEEEE! has influenced your thoughts and posts. Do remember it is a small thing to be judged by me. It is your opinion of you that matters.