.png)
File permissions are a basic concept in Linux systems to manage permissions to write, read and execute files.
In this article I would like to limit myself to a less common file right - the SUID-bit.
By setting the SetUserID bit a file is always executed with the rights of the file owner.
What is the file permission used for?
An example of a meaningful use of this file right is the program passwd, which changes passwords of users and groups. In order for a user to change his own password, the SUID right must be set. Thus, the program is executed as root.
Schema
The SUID bit is displayed as follows:
The SUID bit is indicated by a s or S at the position of the file permission to execute a file (x).
A small s means that an execution is also possible in addition to the SUID bit. However, this is not possible with a large S.
Why is the SUID bit "dangerous"?
The SUID bit should be used very carefully and only when really necessary. Because the privileged execution of a file creates a potential security risk. If a file is manipulated accordingly, rights can be extended ( privilege escalation).
Example
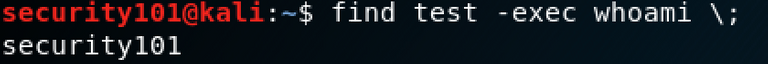
The program find with the original rights:

find offers the possibility to execute commands using -exec :
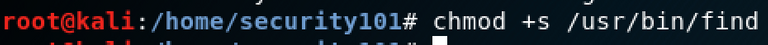
Now the SUID bit is set: chmod +s /usr/bin/find
Then we execute the same command as before:
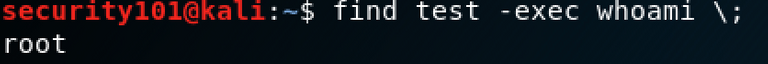
So it is now possible to execute arbitrary code as root. If unauthorized access to a system has taken place, a "backdoor" can be set up with which it is possible to obtain administrative rights from any user.
Which files have set the SUID bit?
Files with SUID rights can be found, for example, using:
find / -user root -perm -4000 -print 2>/dev/null

Thank you for reading !

Sehr schön erklärt und veranschaulicht 👍
Gerade die hacks zur suid sind super spannend 😎😅
Personally, I find a good practice to find and remove suids from everything except "su" on a new installation. Saves a lot of headache :) Good post, happy to see some quality content here.
I love Windows but since I have had a real interested in cyber-security, I deeply want to fragment my memory card and to also have Linux for the secure part of my activity. I've a friend who could do it for me but I prefer learning myself so did you've ever made an article speaking of that? :-)